Task 5.4: Securing the Default User Accounts
During the installation of a Windows server or client operating system, two user accounts are created by default: the Local Administrator and the Guest account. These accounts live in the local accounts database (LAD) and remain there on XP, Vista, Windows 7, member servers, and stand-alone servers.
As you run DCPromo on a server to create a new domain and become a domain controller, the LAD is replaced with the AD database on that system. All accounts in the LAD are destroyed. Two default domain accounts are created for this new domain and they live in AD. These are the Administrator for the domain, and the Guest account for the domain.
In addition to the AD database, a new LAD is created for Directory Services Restore Mode (DSRM) and for Recovery Console login. Only one account lives in this LAD: the Local Administrator, which is to be used solely for these two disaster-recovery purposes.
These accounts are built automatically and assigned these names—always. This makes them an easy target for an attacker. These accounts must be secured to mitigate their vulnerability.
You should already have a strong password policy in place. You should also have an administrative policy that dictates that only a limited few, top-level administrators are allowed to use the true Administrator account or reset the true Administrator password.
Scenario
You are responsible for the security of your domain. You want to reduce the potential for attack on user accounts and have decided to strengthen the default user accounts for the domain and on several of your most critical servers.
Scope of Task
Duration
This task should take 20 minutes.
Setup
You will edit the default domain policy to rename the Local and Domain Administrator and Guest accounts of all systems in the domain. Using this same GPO, you will disable the local Guest account on all systems in the domain.
On the domain controller, you will reset the Directory Services Restore Mode (DSRM) and Recovery Console Administrator logon password.
Caveat
Renaming the Administrator account on every system on the domain can cause services, applications, drive mappings, printer mappings, and scheduled tasks to fail. You should analyze this possibility before changing the Administrator account.
Resetting passwords can cause the loss of data. The forced reset of the password in ADUC destroys access to all Encrypting File System (EFS) content by the user, all stored passwords in Microsoft Internet Explorer, and all email that was encrypted by the user. If you know the old password and can change the password for a user or have the user change their password using the Change Password utility, this loss of access to content is eliminated.
Always use caution when modifying any GPO, and be sure you understand the ramifications of your configuration, as well as where you have the GPO linked.
Procedure
You will implement a GPO at the domain level to rename the Local and Domain Administrator and Guest accounts on all systems in the domain, and disable the Guest account. You will create a decoy Administrator account with virtually no privileges. You will then reset the password on the Local Administrator account (used for DSRM and Recovery Console) on a domain controller to implement a standard, strong password.
Equipment Used
For this task, you must have:
- Windows Server 2003 domain controller system
- Domain Administrator access
Details
Managing the Default Users with the Default Domain Policy
1. Log on to the Windows Server 2003 domain controller system as the Domain Administrator.
2. Select Start ⇒ Programs ⇒ Administration Tools ⇒ Active Directory Users And Computers (ADUC).
3. Select the domain name. Right-click on the domain name and choose Properties. Select the Group Policy tab.
4. Select the Default Domain Policy and click the Edit button.
5. Expand the GPO to view Computer Configuration ⇒ Windows Settings ⇒ Security Settings ⇒ Local Policies ⇒ Security Options.
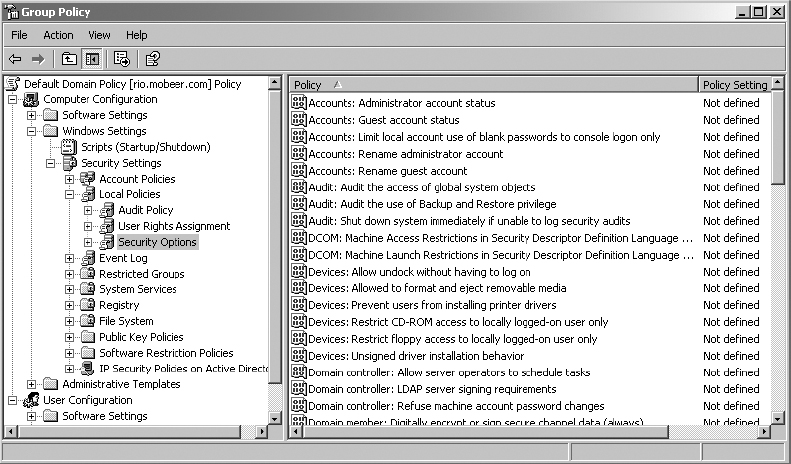
6. In the right pane, double-click Accounts and rename it Administrator Account.

Renaming the Administrator account on every system on the domain can cause services, applications, drive and printer mappings, and scheduled tasks to fail. Analyze this possibility before changing the Administrator account. Renaming the Administrator account does not rename the DSRM Administrator account on the domain controllers.
7. In the Define This Policy Setting field, type the new administrator account name: TopDog. Click OK.
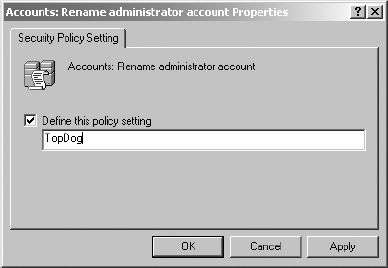
8. In the right pane, double-click Accounts and rename it to Guest Account.
9. In the Define This Policy Setting field, type the new Guest account name: JoeBlow. Click OK.
10. In the right pane, double-click Accounts and rename it to Guest Account Status.
11. Set the Define This Policy Setting option to Disabled. Click OK.

You may choose to disable the Administrator accounts on each local system as well. The GPO has a setting for Accounts: Administrator account status. This setting could be set to Disabled. However, you will not be disabling the Administrator account in this exercise.

Disabling the Administrator account on every system on the domain can cause services, applications, drive and printer mappings, and scheduled tasks to fail. Analyze this possibility before disabling the Administrator account.
12. Confirm your settings in the GPO.
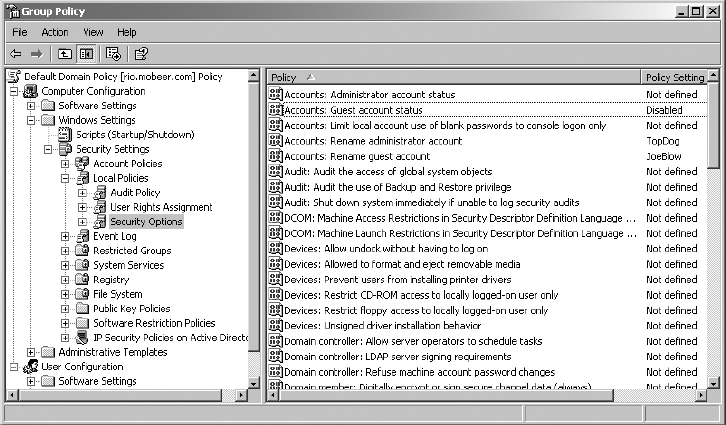
13. Close the GPO by clicking the X in the upper-right corner. Click Close in the DomainName.com Properties dialog box.

This policy should be fully effective within 120 minutes of closing the properties for the domain.
Creating a Decoy Domain Administrator Account
1. In ADUC, expand the domain name.
2. In the left pane, select the Users container.
3. In the right pane, select the Administrator user object.
4. Right-click on the Administrator user object and click Rename.

You have already changed the logon name to TopDog with the default domain policy. This step changes the display name of the account to match, and further obscures the Administrator account from the unaware attacker.
5. Type in the new name—TopDog—and press Enter. You will receive a warning about needing to log off immediately and log back on with the new credentials.
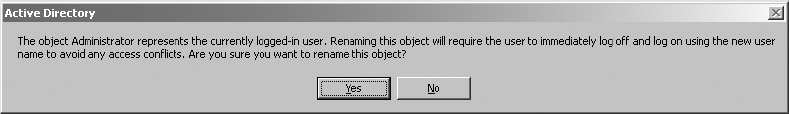

Be sure you have saved all of your work and have closed all applications except ADUC before proceeding.
6. After confirming that it is safe to log off the system, click Yes.
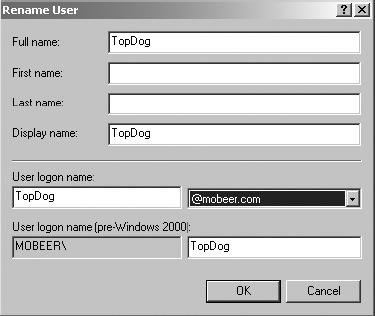
7. Complete the Rename User dialog box by filling in the new name for the Administrator account: TopDog.
8. In the User Logon Name area, select the proper User Principal Name (UPN) from the drop-down list. This usually matches the user’s email address and can be used as a logon name. Click Next.
9. Close all applications. Select Start ⇒ Log Off.
10. Log on to the domain with the new username, TopDog (formerly Administrator), and the appropriate password.
11. Select Start ⇒ Programs ⇒ Administration Tools ⇒ Active Directory Users And Computers (ADUC).
12. Expand the domain. In the left pane, select the Users container.
13. Right-click on the Users container and select New ⇒ User.
14. In the First Name field, type Administrator.
15. In the User Logon Name field, type Administrator.
16. In the User Logon Name area, select the proper User Principal Name (UPN) from the drop-down list. This usually matches the user’s email address and can be used as a logon name. Click Next.
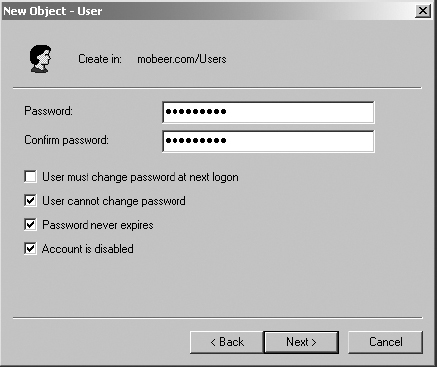
17. Type a strong password (the stronger, the better) in the Password and Confirm Password fields.
18. Disable User Must Change Password At Next Logon, and enable the other three settings.
19. Click Next. Click Finish to create the decoy Administrator account.
20. Double-click on the TopDog user object. Highlight the information in the Description field. Right-click the highlight and select Cut.
21. Close the TopDog Properties dialog box.
22. Double-click the decoy Administrator user object. Right-click in the Description field and select Paste.
23. Close the decoy Administrator Properties dialog box.

This account could be placed in groups that have restrictive Deny permissions to further reduce accesses from this account. The Deny Domain Local Group process will be covered in Task 5.5.
Resetting the DSRM Administrator Password
1. You will need to run NTDSUTIL from a command window. Close all applications. Select Start ⇒ Run, and type CMD.
2. In the command window, at the C: prompt, type NTDSUTIL and press Enter.
3. At the NTDSUTIL prompt, type HELP and press Enter. Observe the response:
? - Show this help
information
Authoritative restore - Authoritatively
restore the DIT database
Configurable Settings - Manage configurable settings
Domain management - Prepare for new domain creation
Files - Manage NTDS database files
Help - Show this help information
LDAP policies - Manage LDAP protocol policies
Metadata cleanup - Clean up objects of
decommissioned servers
Popups %s - (en/dis)able popups
with "on" or "off"
Quit - Quit the utility
Roles - Manage NTDS role owner tokens
Security account management - Manage Security
Account Database -
Duplicate SID Cleanup
Semantic database analysis - Semantic Checker
Set DSRM Password - Reset directory
service restore mode
administrator account
password
4. At the NTDSUTIL prompt, type Set DSRM Password and press Enter.
5. At the Reset DSRM Administrator Password prompt, type HELP and press Enter. Observe the response:
? - Show this help information
Help - Show this help information
Quit - Return to the prior menu
Reset Password on server %s - Reset directory
service restore mode
administrator account
password on specified
domain controller. Use NULL
for local machine.

You cannot use NTDSUTIL to reset this password if the target domain controller is currently in Directory Service Restore mode.
6. To reset the DSRM Administrator password on the local domain controller, at the Reset DSRM Administrator Password prompt, type Reset Password on Server NULL and press Enter.
7. You will be prompted for the new DSRM Administrator password. Type the new password Password1, and press Enter. The display screen should show the following:
Please type password for DS Restore Mode Administrator Account:
*********
8. You will be prompted to confirm the new password. Type the password Password1, and press Enter. The display screen should show the following:
Please confirm new password: *********
You may receive a notice as shown here:
Because the local system doesn't support application password
validation, ntdsutil couldn't verify the password with the domain
policy. But ntdsutil will continue to set the password on DS
Restore Mode Administrator account.
You should see a success message:
Password has been set successfully.

You could use this tool to reset the DSRM Administrator password on remote domain controllers in the domain by specifying the fully qualified domain name (FQDN) of each DC, as shown here: Reset Password on Server rio.mobeer.com.
9. At the Reset DSRM Administrator Password prompt, type QUIT and press Enter.
10. At the NTDSUTIL prompt, type QUIT and press Enter.
11. Close the command window by typing EXIT and pressing Enter.
Criteria for Completion
You have completed this task when you have modified the Default Domain GPO to rename the Administrator and Guest logon names, and have disabled the Guest accounts throughout the entire domain, renamed the Administrator account, created a decoy administrator account with no privileges, and then reset the DSRM.
