Task 1.1: Performing an Initial Risk Assessment
Risk assessment can be achieved by one of two methods: qualitative or quantitative. Qualitative assessment does not attempt to assign dollar values to components of the risk analysis. It ranks the seriousness of threats and sensitivity of assets into grades or classes, such as low, medium, or high.
Quantitative assessment deals with numbers and dollar amounts. It attempts to assign a cost (monetary value) to the elements of risk assessment and to the assets and threats of a risk analysis. The quantitative assessment process involves these three steps:
1. Estimate potential losses—Single Loss Expectancy (SLE) = Asset Value × Exposure Factor.
2. Conduct a threat analysis—The goal here is to estimate the Annual Rate of Occurrence (ARO). This numeric value represents how many times the event is expected to happen in one year.
3. Determine Annual Loss Expectancy (ALE)—This formula is calculated as follows: ALE = Single Loss Expectancy (SLE) × Annual Rate of Occurrence (ARO).
The goal of this task is to conduct these three steps of the quantitative risk assessment process.
Scenario
You have been asked to perform a quantitative risk assessment for a small startup social networking firm.
Scope of Task
Duration
This task should take about 30 minutes.
Setup
For this task you need access to a pen and paper. In real life, assessments require knowledge of assets, an analysis of threats, and a team of people to help identify what is truly important to the organization. These people should be from key departments of the company so that you achieve a rounded view. For this task, consider what personal information you would need. Consider how you would gather this information in a real-life risk assessment. Common methods include surveys, interviews, one-on-one meetings, and group meetings.
Caveat
In real life, risk assessment is a complex process that is usually done with the aid of software tools that perform all the calculations.
Procedure
In this task, you will learn how to perform a quantitative risk assessment.
Equipment Used
For this task, you must have:
- Paper
- Pen or pencil
Details
This task introduces you to the risk assessment process. This is a critical step in the security process since an organization must determine what is most critical and apply cost-effective countermeasures to protect those assets. A quantitative risk assessment attempts to put dollar amounts on those risks, which makes it a valuable tool when working with management to justify the purchase of countermeasures.
Estimating Potential Loss
Your first step in the risk assessment process is to estimate potential loss. You do so by multiplying the asset value by the exposure factor. The asset value is what the asset is worth. The exposure factor is the cost of the asset lost or damaged in one single attack. For example, if the threat is a computer virus and the asset is a server used for customer profiles that is valued at $32,000 with an exposure factor of 0.25, the formula would be as follows: Single Loss Expectancy = Asset Value × Exposure Factor, or $32,000 × 0.25 = $8,000. The SLE, which represents what one computer virus attack would cost, is $8,000.
Now that you have a better idea of how the process works, take a look at Table 1.1, which shows a variety of threats and their corresponding exposure factors.
TABLE 1.1 Threat Level and Exposure Factor (EF)
| Threat Level or Vulnerability | EF |
| 5 = Stolen or compromised data | 0.90 |
| 4 = Hardware failure | 0.25 |
| 3 = Virus or malware | 0.50 |
| 2 = DoS attack | 0.25 |
| 1 = Short-term outage | 0.05 |
With a list of exposure factors, you are now ready to calculate the SLE for some common systems. These are shown in Table 1.2. Complete Table 1.2 using the information provided by Table 1.1.
TABLE 1.2 Calculating Single Loss Expectancies (SLE)
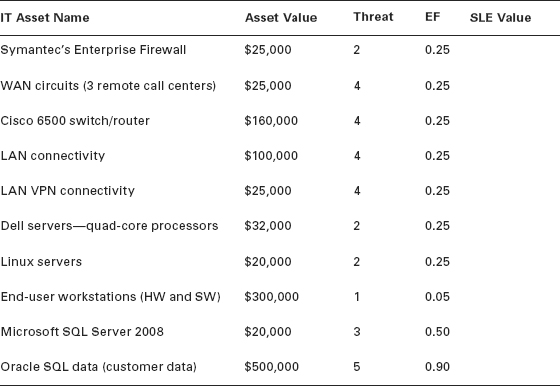
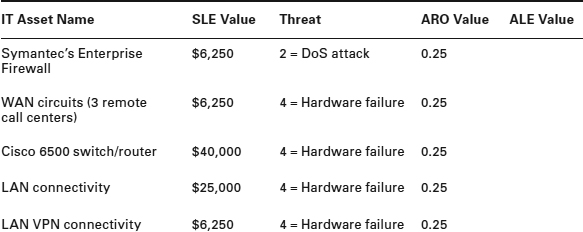
TABLE 1.4 Calculating Annual Loss Expectancies (ALE)

Conducting a Threat Analysis
With the calculations completed for SLE, the next step is to determine the ARO. The ARO is the average number of times you might expect a particular event to happen in a year. Here’s an example: Galveston typically gets hit with a hurricane at least once every 10 years. Therefore, the chance for a hurricane is 0.10.
Complete Table 1.3 to practice computing the ARO. Use the following information:
TABLE 1.3 Annual Rate of Occurrence (ARO)
| Threat Level or Vulnerability | ARO Value |
| 5 = Stolen or compromised data | |
| 4 = Hardware failure | |
| 3 = Virus or malware | |
| 2 = DoS attack | |
| 1 = Short-term outage |
Stolen Equipment Based on information provided by actuary tables, there is the possibility that your organization will lose equipment or have its equipment compromised once in a 5-year period.
Hardware Failure By examining past failure rates of equipment, you have determined that it has happened twice in the last 8 years.
Computer Virus Historical data shows that the company has been seriously affected only once in the last 2 years.
DoS Attack Your research has shown that the average company in your field is affected by denial-of-service (DoS)/Botnet attacks up to three times every 12 years.
Short-Term Outage Trouble tickets from the help desk indicate that three-fourths of all trouble tickets in one year are related to some type of outage.
You can check your answers against the ARO Value column in Table 1.4.
Determining the Annual Loss Expectancy
Armed with SLE values and ARO values, you are now ready to complete the final steps of the risk assessment process:
1. To calculate ALE you will use the following formula: ALE = Single Loss Expectancy (SLE) × Annual Rate of Occurrence (ARO). For example, if the SLE is $1,000 and the ARO is 0.25, the formula would be $1,000 × 0.25 = $250 ALE.
2. Using the information gathered earlier in this task, complete Table 1.4.

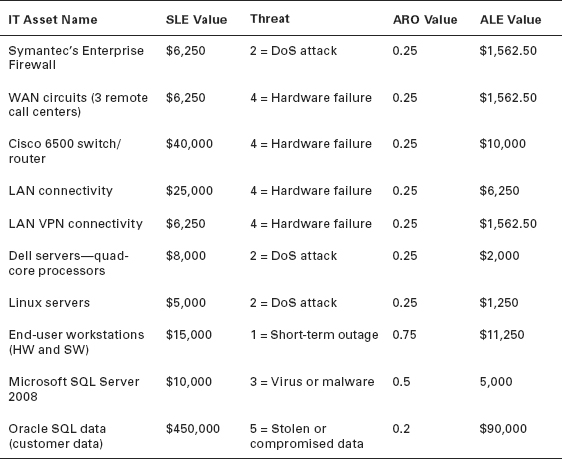
The answers for Table 1.4 can be found in Table 1.5. Given the risk calculated for Table 1.5, note that the customer’s database has the largest ALE.
TABLE 1.5 Calculating Annual Loss Expectancies results
Criteria for Completion
You have completed this task when you have calculated the SLEs, AROs, and ALEs for a range of IT products.
