Internet Protocol Security (IPSec) is currently one of the strongest VPN technologies available. In its default configuration, it can be relatively easy to set up, but it is versatile and can become quite complex. It is an open standard and can be adjusted to integrate with your existing environment. The strength of the encryption, authentication, and integrity validation can also be adjusted.
In the Microsoft implementation, an Active Directory environment currently running on Windows Server 2000, 2003, or 2008 and Windows 2000, XP Professional, Windows Vista, or Windows 7 uses Kerberos as the default configuration for authentication. For integrity validation, the default settings for these operating systems use the Secure Hashing Algorithm, 160 bit (referred to as SHA1). Windows 2000, 2003, and XP use three passes of the Data Encryption Standard—referred to as 3DES or triple DES—for its data-encryption algorithm. Windows Server 2008 and Windows Vista use AES-128 as their default data-encryption algorithm. AES is the newer, stronger data-encryption standard that is replacing 3DES.
If you need to improve system performance, you can implement a single pass of DES, along with using Message Digest version 5 (MD5) for integrity validation. These are weaker but less demanding of the resources on the system, thus resulting in better system performance.
Scenario
You have several file servers that contain sensitive data. You must ensure that all communications with these servers are implemented through a VPN.
Scope of Task
Duration
This task should take 30 minutes.
Setup
You are an administrator in an Active Directory environment. You will configure a Secure Server IPSec Policy GPO on the organizational unit (OU), which holds the file servers with sensitive data. This policy will require that all communications to these servers be protected with IPSec.
You must then implement a second Client Respond IPSec Policy GPO to enable IPSec for the users. You will link this to an OU that holds the only clients authorized to access these secure servers. IPSec isn’t available for users by default since it degrades the performance of the systems.
Caveat
If the IPSec policy is implemented incorrectly, the entire network infrastructure can fail. Do not implement the Secure Server IPSec Policy for any systems that provide network infrastructure services, like domain controllers, DNS servers, WINS servers, or RRAS servers. These services will fail. Implement the Secure Server IPSec Policy only on the select few file servers holding sensitive data. You should also expect noticeable performance degradation, due to the CPU horsepower required to perform the massive mathematical calculations inside the encryption standard.
Procedure
For this task, you will produce a Secure Server IPSec Policy GPO that is linked to a new OU called the Confidential Servers OU. You will then produce a Client Respond IPSec Policy GPO that is linked to a new OU called the Confidential Clients OU.
Equipment Used
For this task, you must have:
- Windows Server 2003 domain controller system
- Domain Administrator access
Details
Creating the OU Infrastructure
1. Log on to the Windows Server 2003 domain controller system as the Domain Administrator.
2. Select Start ⇒ Programs ⇒ Administration Tools ⇒ Active Directory Users And Computers (ADUC).
3. Expand the domain. Click on the domain name.
4. In the right pane, right-click and select New ⇒ Organizational Unit.
5. Name the new OU Confidential Servers. This OU would be populated with the computer accounts for the file servers holding the sensitive data.

Any systems placed in this OU will require IPSec for all communications. If the system is providing any network infrastructure services, many of these services will fail. Place in this OU servers that are providing file- and printer-sharing services only.
6. Click on the domain name.
7. In the right pane, right-click and select New ⇒ Organizational Unit.
8. Name the new OU Confidential Clients.

This OU would be populated with the computer accounts for the client systems that need to access the sensitive data.

Any systems placed in this OU will experience performance degradation when communicating with IPSec secure servers.
Building the Secure Server IPSec Policy GPO
1. Right-click on the Confidential Servers OU and select Properties. Select the Group Policy tab.
2. Click the New button and name the new GPO IPSec Secure Servers Policy.
3. Click Edit to open the IPSec Secure Server GPO.
4. Expand Computer Configuration ⇒ Windows Settings ⇒ Security Settings, and select IP Security Policies On Active Directory.

Notice that none of the policies are currently assigned.
5. In the right pane, right-click on Secure Server (Require Security), and select Assign.

6. Confirm that the policy is now assigned.
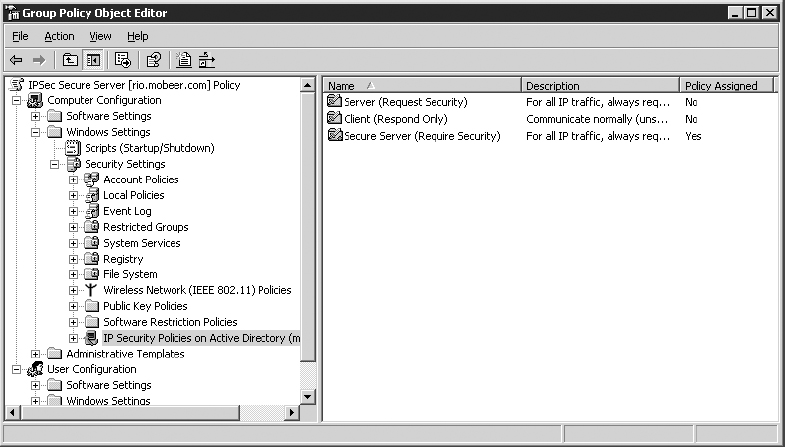

Any Windows 2000 Server, 2000 Workstation, Server 2003, 2008, XP, Vista, or Windows 7 system placed into this OU will require IPSec for all communications that are initiated remotely.
7. Close the IPSec Secure Server Policy GPO. Click OK to close the Confidential Servers Properties dialog box.
Building the Client Respond IPSec Policy GPO
1. Right-click on the Confidential Clients OU and select Properties. Select the Group Policy tab.
2. Click the New button and name the new GPO IPSec Client Respond Policy.
3. Click Edit to open the IPSec Client Respond GPO.
4. Expand Computer Configuration ⇒ Windows Settings ⇒ Security Settings, and select IP Security Policies On Active Directory.

Notice that none of the policies are currently assigned.
5. In the right pane, right-click on Client (Respond Only), and select Assign.
6. Confirm that the policy is now assigned.

Any Windows 2000 Server, 2000 Workstation, Server 2003, 2008, Server 2008, XP, Vista, or Windows 7 system placed into this OU will implement IPSec for all communications that are initiated locally to IPSec servers.
7. Close the IPSec Client Respond Policy GPO. Click OK to close the Confidential Clients Properties dialog box.
Criteria for Completion
You have completed this task when you have created the OU for the servers and another one for the clients. You must also have created and assigned the Secure Server IPSec Policy on the server’s OU and the Client Respond IPSec Policy on the client’s OU.
