It is important to know when users are authenticating on your network. This could reveal such events as a user authenticating at unexpected times of the day or week, or users failing to correctly authenticate. The latter indicates a possibility that a user account is being used in a brute-force logon attack (when an attacker is trying to guess a user’s password by attempting multiple logons so that the attacker can gain unauthorized access to system resources).
Two settings are related to the auditing of logons. The first, Audit Account Logon Events, identifies when a user attempts to authenticate against a domain controller. In other words, a user is attempting to log on as a domain user. This event gets recorded in the authenticating domain controller’s security event log.
The second, Audit Logon Events, identifies when a user attempts to authenticate against the local account database. In other words, a user is attempting to log on locally, as a local user. This event gets recorded in the local system’s security event log.
Scenario
You are an administrator in an AD environment. You are responsible for the maintenance of security for all domain user accounts. You must be able to track who logs on or attempts to log on, from which system, and at what time and day. An appropriately configured audit policy is the proper tool to implement this capability.
Scope of Task
Duration
This task should take 15 minutes.
Setup
You need to generate an audit trail of all domain user logons. You will implement an audit policy for account logons in the Default Domain Policy GPO.
Caveat
Implementing an audit policy is a common approach to monitoring and recording events on your information systems. An administrator should be aware of several aspects of auditing:
- Review the log files, manually or with an automated tool. Monitoring the audit logs of many domain controllers and servers can be an overwhelming task. Third-party applications are often used to collect and filter the logs from numerous servers to make them intelligible to the administrative staff.
- Secure the log files to prevent scrubbing of the logs. An attacker will erase his tracks in the log files if you do not implement proper security on the log files.
- Know when a real problem exists versus when there is just “noise.” In this case, from time to time users will be working late or may forget their passwords. This is routine noise. It should be recognized as such and not be confused with fraudulent activities or brute-force password-cracking attacks.
- Know how to react when you do detect a real problem. You should have an incident-response team and plan in place for the occasions when a real threat is perceived.
- Turn the log files and be aware of the log file size so you don’t fill a drive and crash a system. To turn the log files, save the log as a file to the hard drive, and then clear all events on the log.
Once again, modifying any GPO, especially the Default Domain Policy GPO, is a dangerous thing to do. This specific policy affects every computer and every user in the domain. Inappropriate changes to this policy could severely cripple access to your information systems.
Always use caution when modifying any GPO, and be sure you understand the ramifications of your configuration, as well as where you have the GPO linked.
Procedure
For this task, you will configure the audit policy in the Default Domain GPO to detect all domain account logons and failed domain logon attempts.
Equipment Used
For this task, you must have:
- Windows Server 2003 domain controller system
- Domain Administrator access
Details
Setting the Audit Policy in the Default Domain Controllers Policy
1. Log on to the Windows Server 2003 domain controller system as the Domain Administrator.
2. Select Start ⇒ Programs ⇒ Administration Tools ⇒ Active Directory Users And Computers (ADUC).
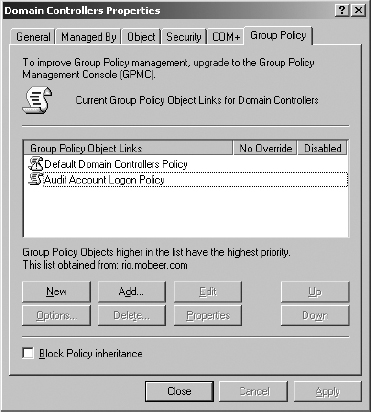
3. Expand the domain. Right-click on the Domain Controllers OU and select Properties.
4. Select the Group Policy tab.
5. Create a new GPO by clicking the New button and typing the name Audit Account Logon Policy. Click Edit.
6. Expand the GPO to view Computer Configuration ⇒ Windows Settings ⇒ Security Settings ⇒ Local Policies ⇒ Audit Policy.

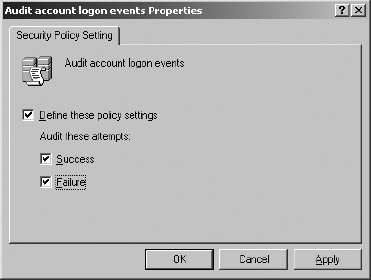
7. In the right pane, double-click on Audit Account Logon Events.
8. Set Define These Policy Settings to Success and Failure. Click OK.
Configuring the Security Event Log in the Default Domain Controllers Policy
1. In the Audit Account Logon Policy, expand the GPO to view Computer Configuration ⇒ Windows Settings ⇒ Security Settings ⇒ Event Log.
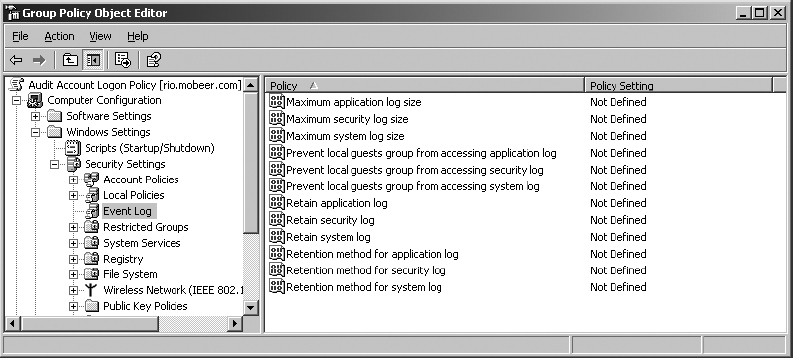
2. Double-click on Maximum Security Log Size.

Audit events get written to the security log, and are viewed and managed in Event Viewer.
3. Define the policy setting and configure the size to 100,000 kilobytes (100 MB). The range is from 64 KB to 4 GB and must be in increments of 64 KB. This size will be automatically adjusted as you configure the settings. Each event consumes approximately 500 bytes; 100 MB allows for approximately 200,000 events written to this security log.
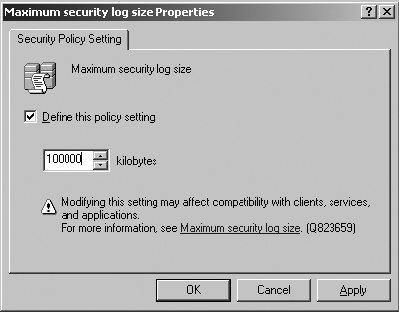
4. Click OK.
5. Double-click on Prevent Local Guests Group From Accessing Security Log.
6. Set this policy setting to Enabled. Click OK.
7. Double-click on Retention Method For Security Log.
8. Set this policy setting to Do Not Overwrite Events (Clear Log Manually). Click OK.

Configuring Security Options for Security Logging in the Default Domain Controllers Policy

This setting will ensure that you never miss an auditing event by actually shutting down the server, in this case the domain controller, if the security log gets full. Because this GPO is linked to the Domain Controllers OU, this setting will kill the domain controller(s) if their security log fills.
1. In the Audit Account Logon Policy, expand the GPO to view Computer Configuration ⇒ Windows Settings ⇒ Security Settings ⇒ Local Policies ⇒ Security Options.
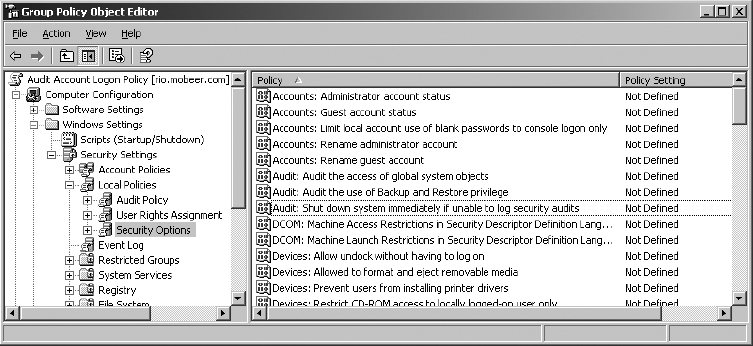
2. Double-click on Audit: Shut Down System Immediately If Unable To Log Security Audits.
3. Set this policy setting to Enabled. Click OK.
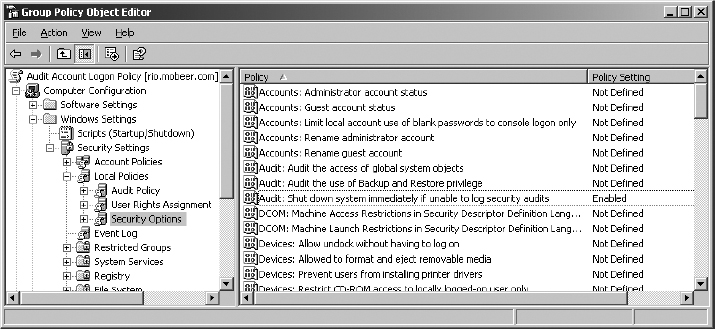
4. Close the GPO by clicking the X in the upper-right corner. Click Close in the Domain Controllers Properties dialog box.

This policy should be effective within 5 minutes of closing the property pages for the GPO.
5. Close ADUC.
Monitoring the Security Logs for Account Logon Events
1. Launch Event Viewer by selecting Start ⇒ Run. In the Open field, type EVENTVWR and click OK.
2. In the left pane of Event Viewer, select Security. This presents the log of all Security events.
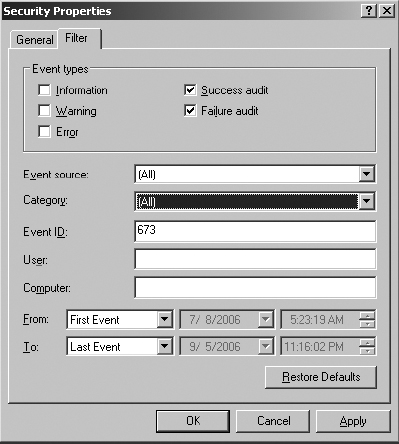
3. In the left pane of Event Viewer, right-click Security and select Properties. Select the Filter tab.

An indication of a successful logon event is Event ID 673 – TGT Granted. An indication of a failed logon event is Event ID 675 – Failed Logon for XP or 2003 clients, or Event ID 681 – Failed Logon for non-XP or 2003 clients.

Event descriptions and ID numbers were redesigned beginning with Windows Vista and Server 2008.
4. Clear the selections for event types of Information, Warning, and Error, and in the Event ID field, enter the first of the account logon event IDs—673—and click Apply.
5. Review any events that match this filter. This event indicates a successful logon.
6. In the Event ID field, enter the event ID 675 to review failed logons.

If no events match this event ID, 675, you may perform one or two logons with an incorrect password to generate this event, and then log on successfully. Launch Event Viewer and review the security log with this filter configured.

You must reset these manually to display all events again. Check all five event types for Information, Warning, Error, Success Audit, and Failure Audit and clear the Event ID field. Then click Apply.
7. After resetting the filter on the security log, click OK to close the properties and close Event Viewer. You must either set the security log to Overwrite As Needed or you must remember to turn the log on a regular basis. Turning the log means to save the open log to a file for archival purposes, and then clear the events in the open log. This improves the performance of the event viewer and can free up disk space on the boot disk.
Criteria for Completion
You have completed this task when you have modified the Default Domain Controller GPO to audit success and failure of all domain account logons, configured and secured the security event log, and ensured that you will never miss an account logon event. Also, you should know how to filter and monitor these Account Logon events in Event Viewer.
