Task 7.11: Logging and Recording Internet Activity
Have you ever wondered what types of activity are really happening on your Internet connection? There is a range of traffic, malware, exploits, and denial-of-service (DoS) attacks sweeping the Internet at any moment. One way to get a better idea of what type of activity is out there is by using a logging tool.
Scenario
Your organization has decided to get proactive about monitoring Internet activity and network traffic. You have been asked to set up a logging device to review and monitor network traffic.
Scope of Task
Duration
This task should take about 30 minutes.
Setup
For this task, you’ll need a Windows computer, access to the Administrator account, and an Internet connection.
Caveat
Logging is a detection control. As such, it only tells you what types of activities have occurred. It does not prevent attacks from occurring.
Procedure
In this task, you will learn how to set up Link Logger.
Equipment Used
For this task, you must have:
- A Windows XP, Windows Vista, or Windows 7 computer
- Access to the Administrator account
- An Internet connection
- A router
Details
This task will show you how logging is set up so you can review network traffic.
1. Download the Windows version of Link Logger from www.linklogger.com/download.htm.

Link Logger supports a wide variety of routers, so make sure you download the correct version before beginning.
2. After downloading the program, click Install and the program will automatically load.
3. Before you can use the program, you will need to first enable logging on the router. This will allow your router to forward the information to the Link Logger program. You will need to log on to your router and go to the logging page. Set the IP address to the computer that you have Link Logger installed on. The system we have installed Link Logger on is 192.168.123.150, so that is the IP address we have configured in the router.

4. Open the Link Logger program. Alerts are recorded on the main screen.

5. You will need to configure Link Logger to accept logs from the router. To do so, choose Edit ⇒ Setup. This window has five tabs:
User This tab allows you to set up traffic load and history.
Audio This tab enables audio alerts for various types of events.
Email This tab allows you to have email sent for specific events.
Router This tab configures the source of logged events.
Database This tab allows Link Logger to be used in conjunction with a database.
6. Edit the Router tab to match the IP address of the router. In our network, that is 192.168.123.254.


If Windows Firewall asks you to allow Link Logger traffic through, you should unblock the port.
7. Once configured, Link Logger will begin to collect logs for review. Selecting the Report menu option allows you to review any attacks that have been captured.
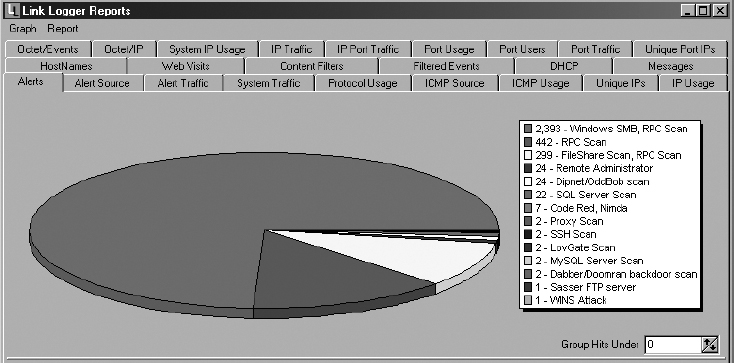
8. By choosing the IP Traffic tab, you can highlight or copy the details of the single attack and perform further research. As an example, Link Logger captured these attacks targeted at our computer network:
1 2008-01-08 09:07:25 Possible DoS HGOD SynKiller Flooding
67.212.170.234
2 2011-01-08 08:49:06 Possible DoS HGOD SynKiller Flooding
58.218.209.136
3 2011-01-08 08:48:32 Possible DoS HGOD SynKiller Flooding
61.176.194.92
4 2011-01-08 07:21:32 Possible DoS HGOD SynKiller Flooding
125.65.109.222
5 2011-01-08 07:17:23 Possible DoS HGOD SynKiller Flooding
202.109.175.74
9. You can use a tool like DShield (http://dshield.org/indexd.html) to look up these addresses if you would like to know their origin. DShield is also a good resource for learning more about specific attacks.


DShield will also allow you to upload logs to their database so they can better trend Internet attacks.
Criteria for Completion
You have completed this task when you have set up Link Logger to capture traffic and analyzed what types of activity are on your network.
