Task 6.6: Configuring a Packet Filter
Packet filters are a fundamental component of every router and firewall, and are built into virtually every operating system. They primarily operate at Layer 3 of the Open Systems Interconnection (OSI) model, but have functionality at both Layer 3 and Layer 4. They are fast, easy to configure, and strong.
The downside of packet filters is that they are not very intelligent. Packet filters either allow an IP/port combination or they block the IP/port combination. They are either wired open or wired closed.
Most contemporary firewalls combine the packet filter (called a generation 1 firewall) with a proxy service (called a generation 2 firewall) and a stateful inspection engine (called a generation 3 firewall).
Scenario
You are the administrator of a Microsoft Windows environment and have been experiencing unexpected and undesired traffic from a remote network. You also suspect that your server has been probed in an attempt to execute a specific exploit. You must stop these activities from affecting your network and your systems.
Scope of Task
Duration
This task should take 20 minutes.
Setup
The configuration of packet filters, in this case, will be performed on a Windows Server 2003 system that is also performing a routing function in your network. You will utilize the Routing And Remote Access Services (RRAS) server to implement the packet filter.
Caveat
Implementing a packet filter to block undesirable traffic will also block desirable traffic that matches the filter specifications.
Also, attacks come from many different locations, target many different systems on your network, and can be implemented using any number of ports and/or protocols. The packet filter is one of your tools to secure your environment, but it is certainly not going to be the answer to all risks. You must implement many layers of security in addition to packet filters.
Procedure
You have noticed unsolicited, unexpected, and undesired traffic on your network that is coming from a network where the IP address range of 192.168.10.1 through 192.168.10.254. You want to stop all of this traffic.
You have also noticed many failed Telnet logon attempts on your server, and you must block this inbound traffic as well.
You will implement two packet filters to eliminate this traffic from your network.
Equipment Used
For this task, you must have:
- Windows Server 2003 system running RRAS
- Administrator access
Details
Configuring the Packet Filter in RRAS
1. Log on to the Windows Server 2003 system as the Administrator.
2. From the Start button, select Programs ⇒ Administrative Tools ⇒ Routing And Remote Access.
3. Expand server_name (Local). Expand IP Routing and select General.
4. In the right pane, select your Local Area Network Interface.

In the following graphic, this interface has been renamed with the IP address bound to the interface: 192.168.222.200.
5. Right-click on the Local Area Network Interface and select Properties.
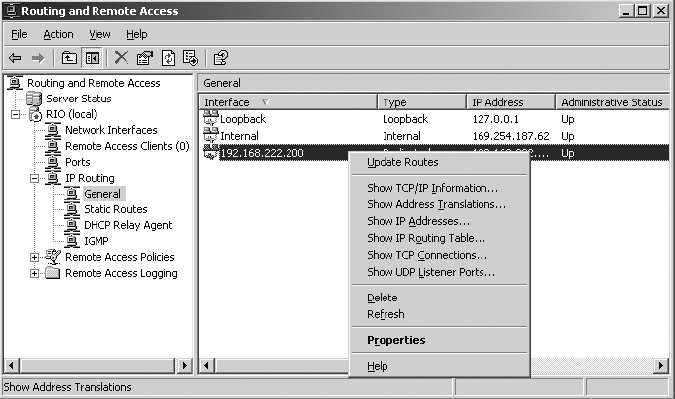
6. In the Properties dialog box, click the Inbound Filters button on the General tab.

7. In the Inbound Filters dialog box, click New to add a new packet filter.
8. Your first objective is to block all traffic coming from the network 192.168.10.0.
9. Select the Source Network check box, and fill in the IP address 192.168.10.0. Fill in the Subnet Mask value of 255.255.255.0. Leave the Protocol option set to Any.
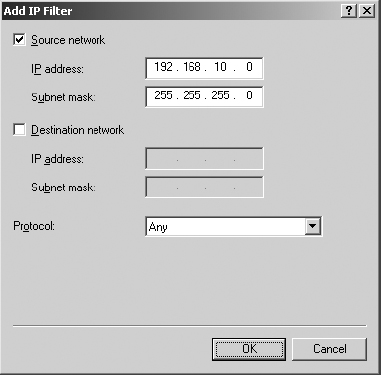
10. Click OK to close the Add IP Filter dialog box.

This packet filter will drop all packets from the IP address range of 192.168.10.0 through 192.168.10.255, going to any destination and using any port or protocol.
11. Your next objective is to block any inbound packets aiming at Telnet, which uses TCP port 23.
12. In the Inbound Filters dialog box, click New to add a new packet filter.
13. Select the Destination check box, and fill in the IP address of this system: 192.168.222.200. Fill in the Subnet Mask value of 255.255.255.255. Select TCP from the Protocol drop-down list. Leave the Source Port option blank. Type 23 in the Destination Port field.
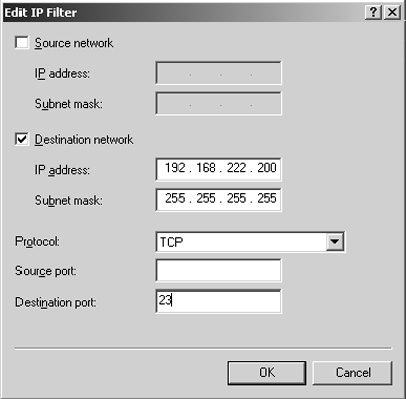

In this packet filter, the subnet mask of 255.255.255.255 means any packet whose destination is this one system. It identifies a single machine on the network.
14. Click OK to close the Add IP Filter dialog box.

This packet filter will drop all packets from any IP address going to this server and using TCP port 23, the port used by Telnet.
15. In the Inbound Filters dialog box, carefully read the filter actions. They can be confusing at first.
- Receive All Packets Except Those That Meet The Criteria Below allows all traffic except the traffic type you need to block.
- Drop All Packets Except Those That Meet The Criteria Below drops all traffic, allowing only the undesired traffic that you’ve identified. In this case, this is the opposite of what you want.
Select Receive All Packets Except Those That Meet The Criteria Below.
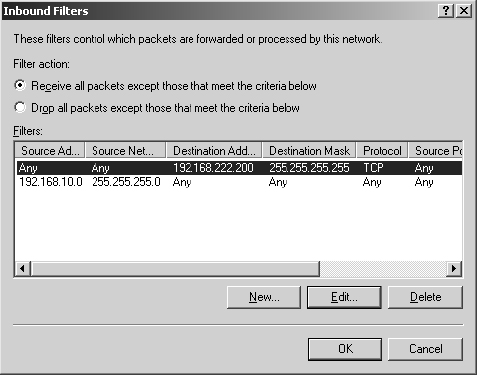
16. Click OK to close the Inbound Filters dialog box.
17. Click OK to close the Interface Properties dialog box.

These filters will disallow traffic that you may desire. You may want to delete these two packet filters when you have successfully completed Task 6.6 to restore your system to its normal operating state.
Criteria for Completion
You have completed this task when you have implemented the two identified packet filters.
