Task 8.6: Tracking Hostile IPs
Knowing who is connected to your company’s computers and if they are a known attacker is an important skill for the Security+ certified professional. This task will show you how to identify hostile IP addresses and determine whether they are connected to any of your computers.
Scenario
The organization for which you work has grown quickly and is concerned that outsiders may try to access critical servers to steal the company’s secret formulas. You have received a call about suspicious traffic and have been asked to investigate.
Scope of Task
Duration
This task should take about 15 minutes.
Setup
For this task, you will need a Windows computer, access to the Administrator account, and an Internet connection.
Caveat
When dealing with intrusions, it is important to follow a strict methodology and avoid altering evidence. If any signs of intrusion are detected, you should contact the organization’s incident-response team.
Procedure
In this task, you will learn how to use Netstat to identify active connections to your computer.
Equipment Used
For this task, you must have:
- A Windows computer
- Access to the Administrator account
- An Internet connection
Details
In this task you will use the site www.dshield.org and Netstat. DShield is a site that gathers log files from users around the world. This task will explore DShield.
Running Netstat
1. Open Internet Explorer or the browser you use on your Windows computer.
2. Enter the URL for the DShield site: www.dshield.org. DShield is a site operated by the SANS Internet Storm Center to collect and analyze web traffic and attacks. DShield collects data about attacks and activity from across the Internet and then parses this data so users can spot attacks and develop better firewall rules.

3. Click on the link at the top of the screen for Data/Reports.
4. Once on the Data/Reports page, review the most common ports probed. As of this writing, the number-one port is 445. Port 135 is the fifth most probed port.
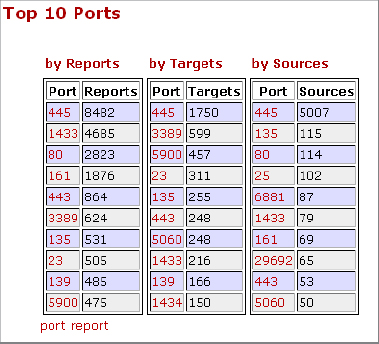
5. Now determine whether your computer has connections open on port 135. One quick way to do so is by using Netstat. To start Netstat, open a command prompt and enter netstat –a, then press Enter. A list of open connections will appear. Shown here is an example of the output:
C:>netstat -a
Active Connections
Proto Local Address Foreign Address State
TCP neptune:epmap neptune:0 LISTENING
TCP neptune:microsoft-ds neptune:0 LISTENING
TCP neptune:135 220.80.114.240 LISTENING
TCP neptune:1038 neptune:0 LISTENING
TCP neptune:1038 neptune:1235 ESTABLISHED
TCP neptune:1067 localhost:1066 ESTABLISHED
TCP neptune:netbios-ssn neptune:0 LISTENING
TCP neptune:1070 www.cnn.com:http CLOSE_WAIT
TCP neptune:1082 www.hackthestack.com ESTABLISHED
TCP neptune:1088 4.2.2.2 ESTABLISHED
TCP neptune:1235 ftp.sybex.com:ftp ESTABLISHED
TCP neptune:1237 www.sybex.com ESTABLISHED
TCP neptune:2869 192.168.123.254:1298 ESTABLISHED
TCP neptune:netbios-ssn neptune:0 LISTENING
TCP neptune:netbios-ssn neptune:0 LISTENING
6. Observe how many connections to port 135 are present. Are these computers in your own domain? Remember from your studies for the Security+ exam that port 135 is used by NetBIOS and can represent a security threat if accessible by attackers. If connections to your computer by computers outside your domain are present, write down the IP address of those connections.
7. With these IP addresses recorded, first look to see if there is a match in the list of top 10 reported IPs. If so, note that this IP address has already been reported as a malicious IP.
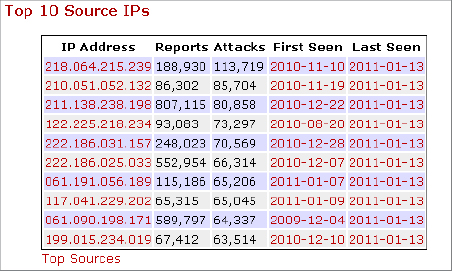
8. Enter the recorded IP address from step 6 in the Port/IP Lookup/Search box found on the upper-right corner of the web page. This is the location of DShield’s IP address database. Where are the remote computers located?
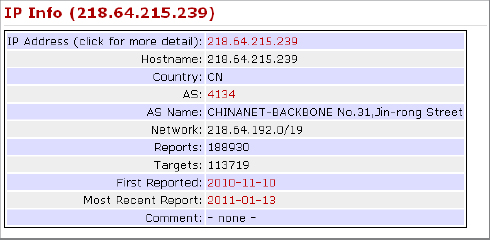
Many attacks come from a cluster of IP addresses in developing countries, including China, Pakistan, and India. Any address that is found to repeatedly target your company should be blocked at the corporate firewall.

If you would like to participate in the DShield process, you can download a client that will allow your firewall’s alerts to be added to the DShield database. The client is available at https://secure.dshield.org/howto.html. It works with most firewalls.
Criteria for Completion
You have completed this task when you have used DShield and Netstat to learn what IP addresses are connected to your local system on port 135.
