Task 3.7: ARP Poisoning with Cain & Abel
Computer security is something the Security+ certified professional must always be thinking about. In addition to security countermeasures and controls, a security professional must understand the ways in which attackers bypass security. This task will examine one of these bypass methods.
This task will examine Address Resolution Protocol (ARP) poisoning. ARP is used to resolve known IP addresses to unknown (MAC) physical addresses. ARP poisoning allows an attacker to bypass the functionality of a switch. This makes it possible for an attacker to attempt a man-in-the-middle attack and to intercept traffic that they would not normally be able to access.
Scenario
Your manager is concerned about the security provided by Ethernet switches. He has asked you to set up a demonstration to show the IT director how switches can be bypassed. The objective in this exercise is to gain support for stronger security controls and push for policy changes to block many clear-text protocols, such as FTP and Telnet.
Scope of Task
Duration
This task should take about 15 minutes.
Setup
For this task, you will need a Windows computer, access to the Administrator account, an Internet connection, one or more switches, and the ability to download files.
Caveat
Although many security tools can be used for positive purposes, they can also be used maliciously; therefore, always obtain permission before installing any tool that may be viewed as malicious.
Procedure
In this task, you will learn how to run Cain & Abel to perform ARP poisoning.
Equipment Used
For this task, you must have:
- A Windows computer
- Access to the Administrator account
- An Internet connection
Details
This task will show you how to install and run Cain & Abel. While the tool has many uses, this task will look specifically at how the tool is used for ARP poisoning.
Installing and Running Cain & Abel
1. Once you have accessed your Windows computer and have logged in as Administrator, open your browser, go to www.oxid.it/cain.html, and click the link to download Cain & Abel.
2. Once you start the download, the program will prompt you to accept the licensing agreement. Once you choose Yes, the download will begin.
3. Upon completion of the download, you will be prompted to download WinPcap. This is a low-level packet driver that is needed for the program to function properly.
4. Once installed, Cain will be accessible from a shortcut placed on the Desktop of your computer. Double-clicking the icon will allow you to start the program.
There are eight tabs on this interface:
Decoders This tab contains password-decoder tools.
Network This tab contains a set of network enumeration tools.
Sniffer This tab features sniffing tools.
Cracker This tab contains dictionary, brute-force, and rainbow table password-cracking tools. Rainbow tables are an alternative to traditional brute-force password cracking. Whereas traditional password cracking encrypts each potential password and looks for a match, the rainbow table technique computes all possible passwords in advance. This is considered a time/memory trade-off technique. Rainbow tables facilitate the quick recovery of passwords and allow them to be cracked within a few seconds.
Traceroute This tab contains a route-tracing tool.
CCDU This tab contains Cisco router tools.
Wireless This tab features wireless-network-discovery tools.
Query This tab features database-discovery tools.
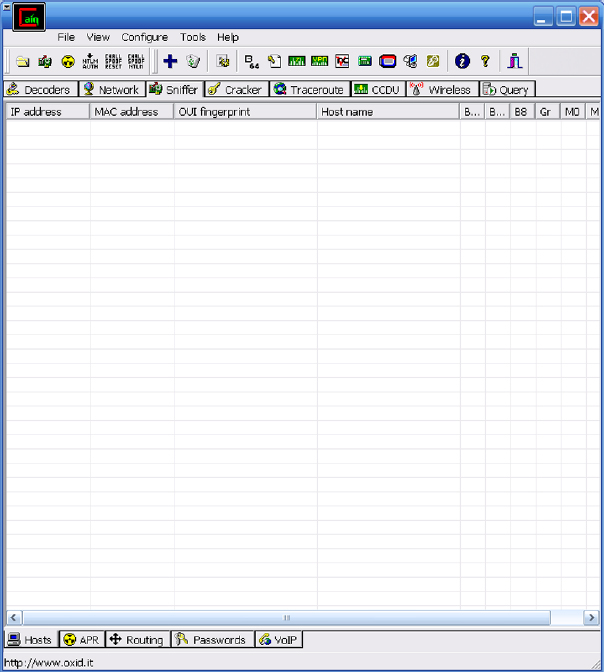
5. Select the Sniffer tab. Notice at the bottom of the page there are now the following additional tabs:
Hosts This tab features host tables.
ARP This tab features ARP spoofing.
Routing You’ll find routing-protocol sniffing tools on this tab.
Passwords This tab contains captured or sniffed passwords.
VoIP This tab contains voice-over IP (VoIP)–sniffing tools.

Use caution when experimenting with unknown tools. It is advisable to use such tools on a test network to avoid disrupting production traffic.
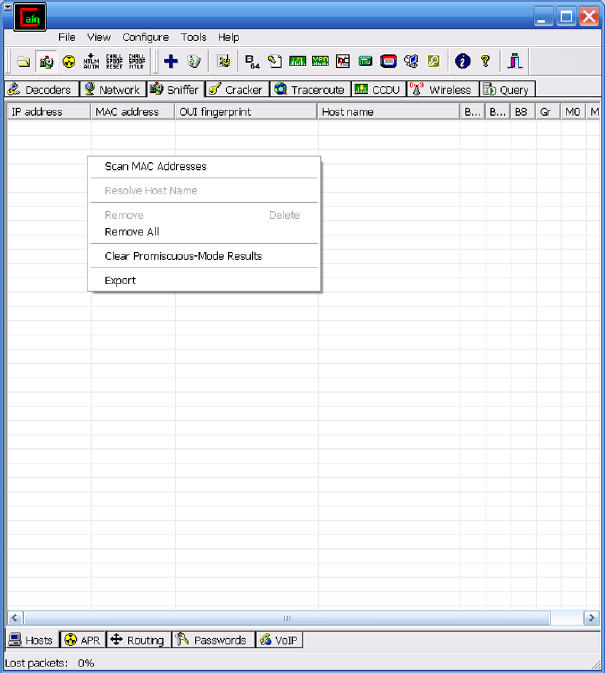
6. Right-click anywhere on the page and choose Scan MAC Addresses. This will build a table of MAC-to-IP addresses that is needed to perform ARP poisoning.
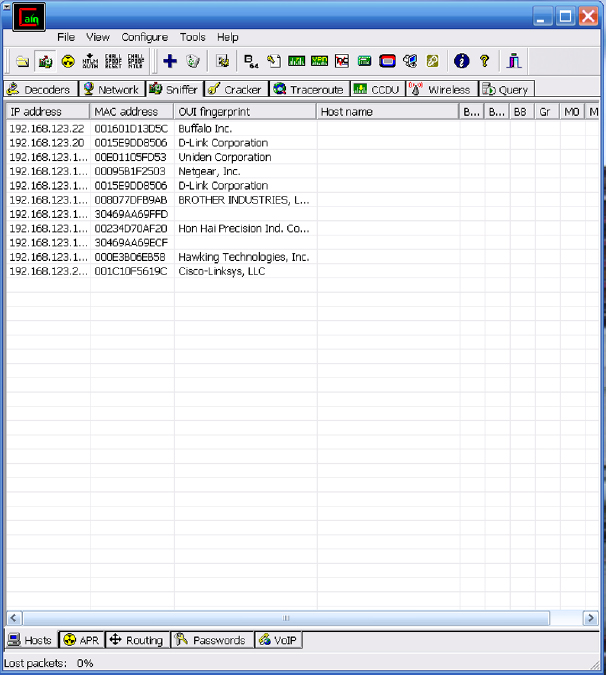
7. Once the host scan is completed, you will be provided with a list of all devices that responded to the initial ARP request.
8. Choose the ARP tab at the bottom of the page. This will take you to the ARP poisoning section of Cain. On the left side of the screen, you will see some of the ARP poisoning techniques that Cain can attempt.
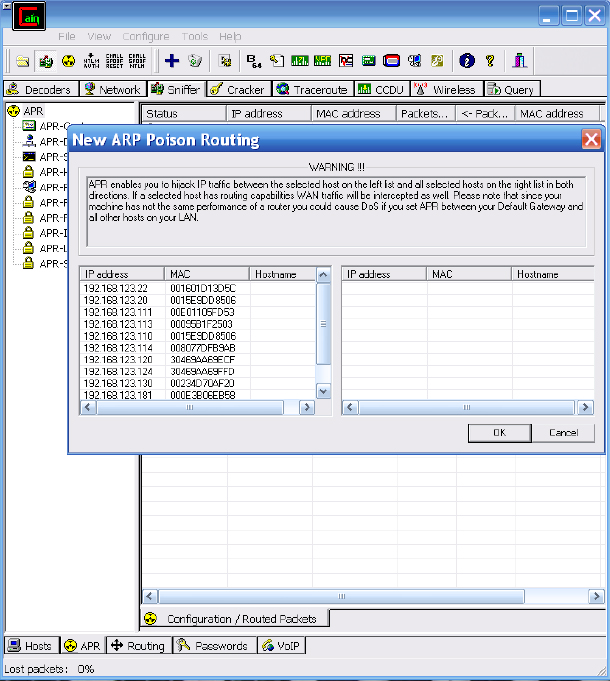
9. To select which targets to perform ARP poisoning against, select the + at the top of the page. This will cause the New ARP Poison Routing selection box to appear.
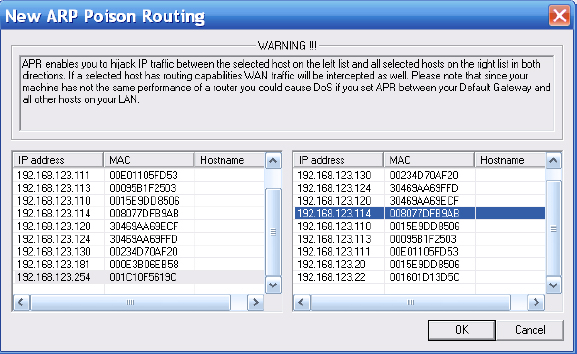
10. You will want to choose the gateway IP address and the local system you would like to perform the ARP poisoning against. Doing so will allow you to intercept traffic between these two systems.

The real danger of ARP poisoning is that it allows an attacker to see traffic on a switched network that would not normally be visible. For example, if a user performs a transfer to an FTP server on the Web, ARP poisoning would allow the attacker to capture the FTP password even though the network is switched and that type of traffic would normally be blocked.
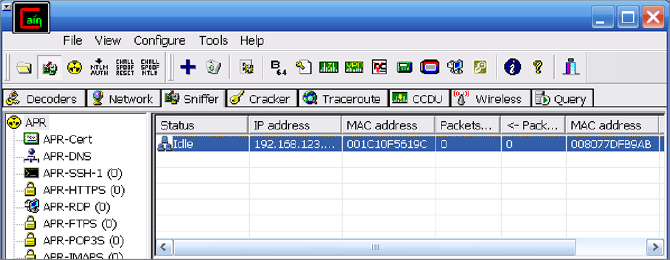
11. Once the IP addresses are selected, click the yellow nuclear icon at the top-left corner of the page. This will start the ARP poisoning attack.
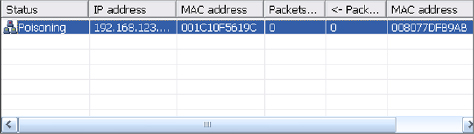
12. While that ARP poisoning is occurring, you will notice that the screen says poisoning in the status column. This will tell you that the attack is ongoing. The attack will continue until you right-click and choose Stop.
13. To fully appreciate the power of this attack, you will want to have someone at the computer you are performing the poisoning attack against visit a website or FTP site that uses clear-text authentication. As an example, you may want to use ftp://ftp.microsoft.com/. After they have accessed the site, choose Passwords from the bottom of the program screen.
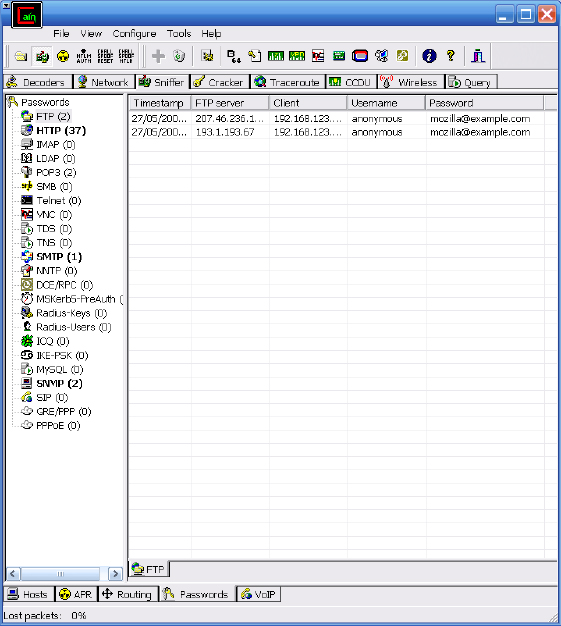
14. From the passwords screen, you can see the different types of passwords that Cain can capture. These include FTP, Telnet, HTTP, IMAP, POP3, and SMB. Notice in the example how many passwords were captured in just the few minutes the tool was allowed to run. Two FTP passwords were captured and are visible at the right of the screen. While these were just demo passwords, consider the security threat had these been real passwords and account details.

To learn more about how ARP poisoning works, take a look at Phase 9 and consider running a protocol analyzer such as Wireshark (www.wireshark.org) while performing this exercise.
Criteria for Completion
You have completed this task when you have downloaded Cain & Abel, installed it on a Windows system, and used it to perform ARP poisoning.
