In a large network environment, the challenge of configuring security on many systems can be daunting. Configuring a security template and deploying this standardized security configuration simultaneously to many systems can simplify this process substantially.
Scenario
You have just completed assembling 20 Windows Server 2003 systems for a new department. These systems require a specialized and uniform security configuration. You must develop and deploy a custom security template to these systems.
Scope of Task
Duration
This task should take 90 minutes.
Setup
Security templates can be reviewed, developed, and deployed from a single system in the environment. A convenient system to use for this process is a domain controller, since it has all of the required tools already installed.
Caveat
The deployment of security templates can cause serious problems in networks. These are powerful controls, which can severely restrict functionality of the systems. Use caution and test these templates prior to deployment. If you’ve ever locked yourself out of your car or house, you understand the seriousness of this caveat.
Procedure
You will configure a custom security template and incorporate it into a GPO for deployment to your specialized systems.
Equipment Used
For this task, you must have:
- Windows Server 2003 system, domain controller
Details
You will first build an MMC with the proper security-related snap-ins. You will then do a quick review of the default templates supplied by Microsoft. Then you will launch the Security Configuration And Analysis tool (SCAT), and create a custom template that meets your specialized security needs. Last, you will deploy the security template by GPO to the target systems for a uniform security configuration.
Security MMC and Default Templates
1. Log on to the Windows Server 2003 domain controller as a Domain Administrator.
2. From the Start menu, select Run. Type MMC and click OK.
3. In the MMC, select File ⇒ Add/Remove Snap-in.
4. Click Add.
5. In the Add Standalone Snap-in dialog box, scroll down and select Security Configuration And Analysis, then click Add.
6. In the Add Standalone Snap-in dialog box, select Security Templates and click Add.
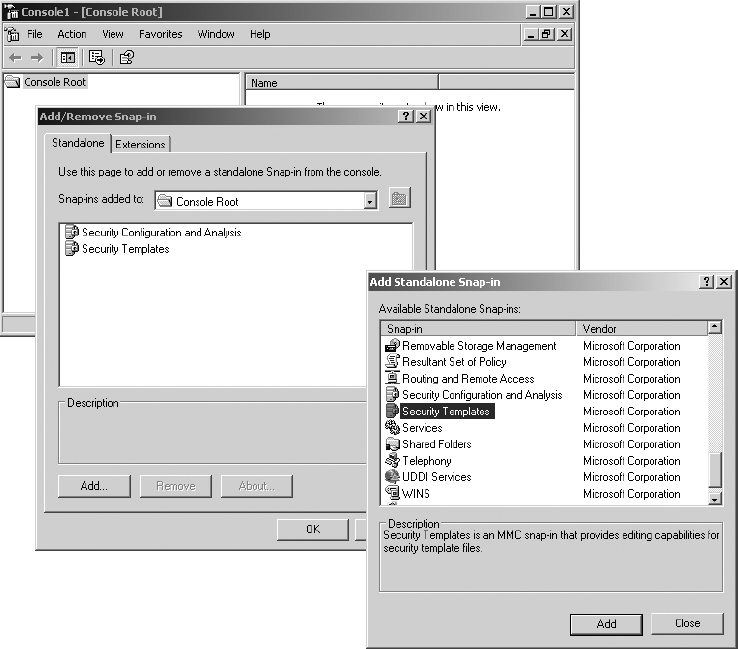
7. Click Close, then click OK.
8. Expand Security Templates: C:WINDOWSsecurity emplates.
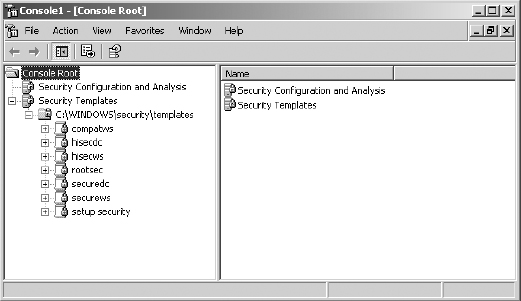
9. Microsoft provides several default security templates during installation. They are contained in files with a .inf extension in the path indicated.
- Setup Security—Configures security settings to match a fresh install of the operating system.
- Securedc and Securews—Stronger security for domain controllers and for workstations and servers, respectively.
- Hisecdc and Hiscews—Still stronger security for domain controllers and for workstations and servers, respectively.
- Compatws—Weakens permissions on the files and folders under the Windows folder to match that of Windows NT 4. This level of permissions may be required to run legacy (NT 4) applications.
- Rootsec—Resets folder permissions on the root of volumes to the original, default permissions. This may be required if these permissions have gotten adjusted erroneously.

Your system may have slightly different templates available. These, however, are a fairly standard collection.
10. Save the MMC by selecting File ⇒ Save As, then name the file Security.msc and click Save.
Security Configuration and Analysis: Creating a Custom Security Template
1. Click on Security Configuration And Analysis.
2. In the left-hand pane, right-click on Security Configuration And Analysis and select Open Database. Type the name Hardened Servers, and click Open.
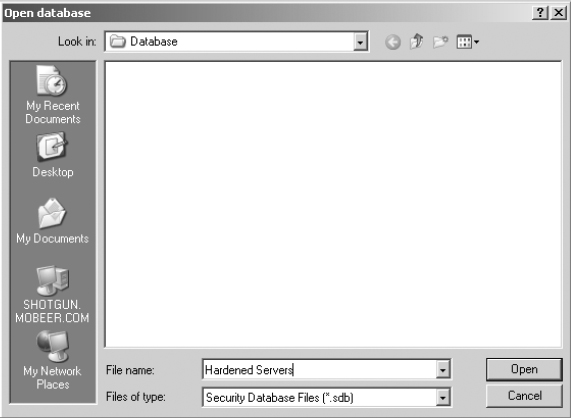
3. select the securews.inf default security template.
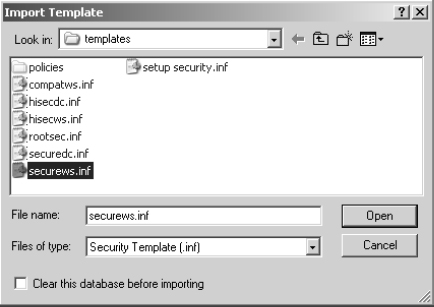
4. Click Open.
5. In the left-hand pane, right-click on Security Configuration And Analysis and select Analyze Computer Now.
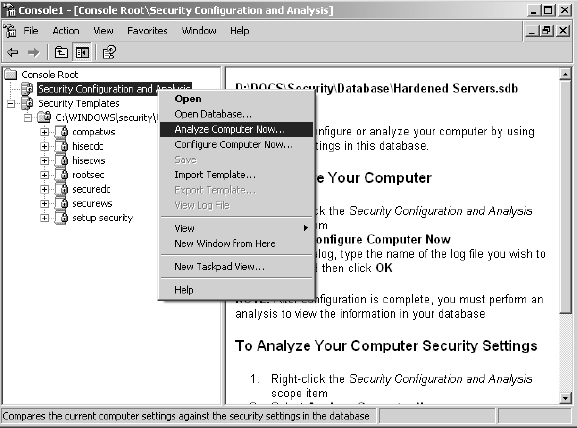

Do not select Configure Computer Now. Doing so would implement this strong security template on the system you are currently working on. This could cause the failure of desired functionality and could disable you from accessing the system.
6. Accept the default path for log files by clicking OK.
7. Once the analysis is complete (this should take just a few seconds), expand Local Policies and select Audit Policy.
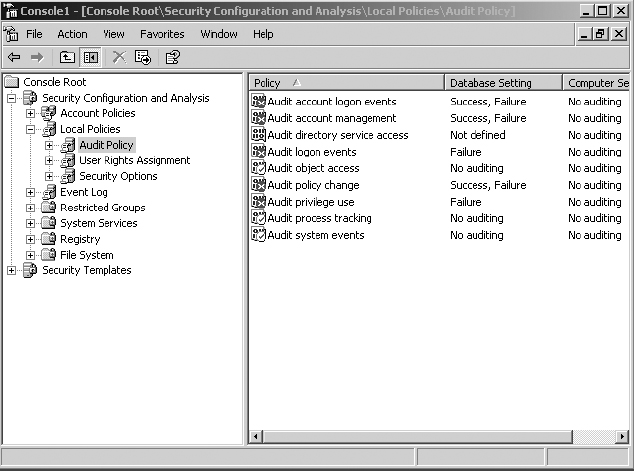
8. Double-click Audit Process Tracking in the right-hand pane. Enable the policy and configure it for Success and Failure.
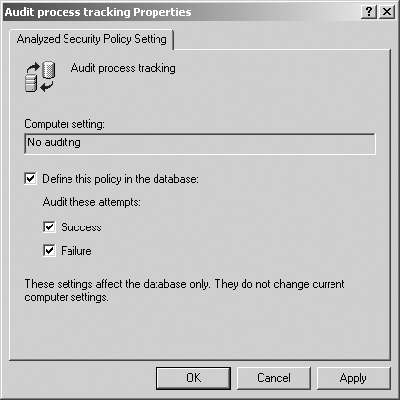
9. Click OK.

You have just customized the security template. You could make additional configuration changes, as desired, for this new custom template.
10. Once you have introduced all of the desired security configuration parameters for the new custom template, in the left-hand pane right-click on Security Configuration And Analysis and select Save.
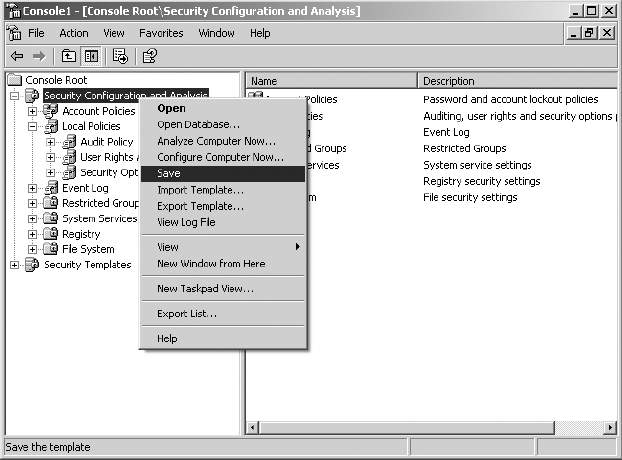
11. Right-click on Security Configuration And Analysis and select Export Template.
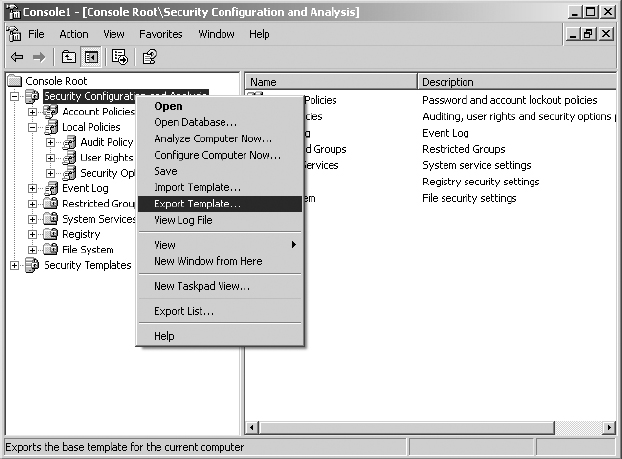
12. Type the name Hardened Servers and accept the default extension .inf by clicking Save.
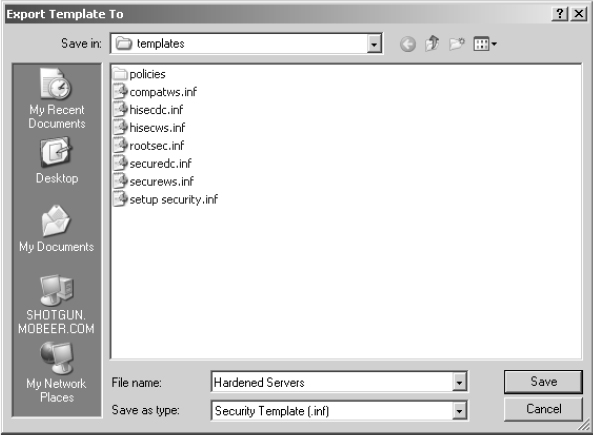

This template is now available in the folder C:WINDOWSsecurity emplates.
Security Template Deployment by GPO
1. From Administrative Tools, launch Active Directory Users And Computers.
2. Earlier, you created an OU called Hardened Servers. Right-click this OU and select Properties. Select the Group Policy tab.
3. Click New and name the new GPO HS Security Template.
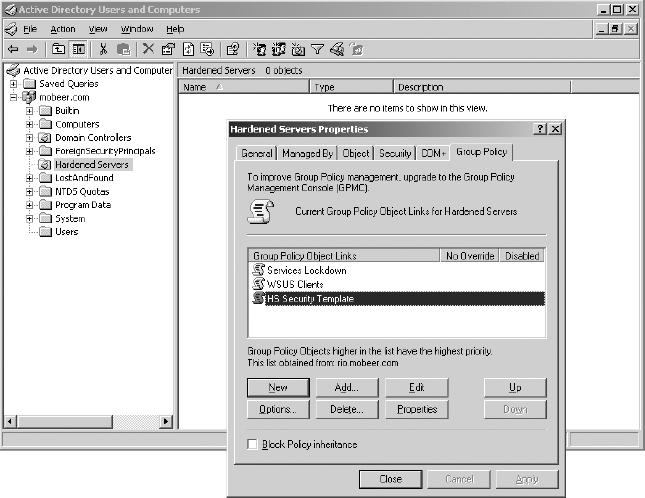
4. Click Edit. Expand the GPO to view Computer Configuration ⇒ Windows Settings and click Security Settings.
5. Right-click on Security Settings and select Import Policy.
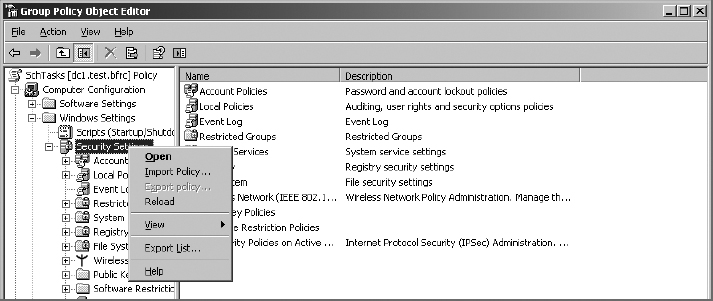
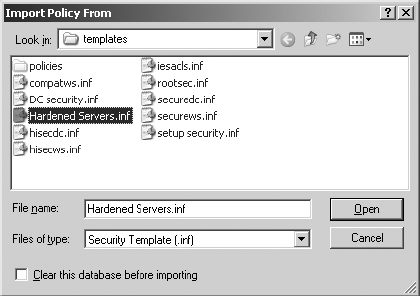
6. Select the Hardened Servers.inf template and click Open.
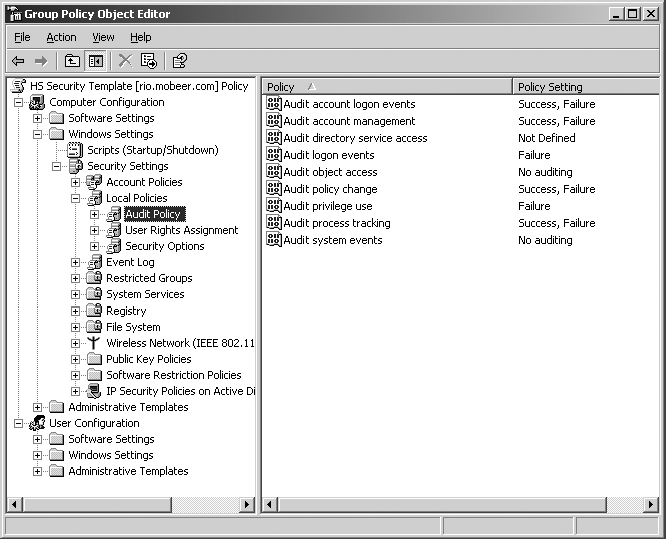
7. Expand Local Policies and select Audit Policy. You should observe your custom setting of Success and Failure for the Audit Process Tracking audit policy. Confirm the presence of any other template settings you may have configured.
8. Close the GPO by clicking the X in the upper-right corner.

Any computer account you place in the Hardened Servers OU is now subject to this new security template.
Criteria for Completion
You have completed this task when you have built the Security MMC and reviewed the default security templates; imported a template into the SCAT; analyzed the local system security; modified, saved, and exported the new custom template; and then imported the custom template into a GPO for mass deployment of these custom security settings.
