In this recipe, we will look at a few of the switches supported by nmap that can be used to bypass IDS/IPS/firewalls. Many a time, when we are performing a scan, we come across a firewall. In case the firewall is not configured correctly, we will be able to execute the following firewall-evasion commands of nmap.
We will use nmap for this activity. Let's begin with the machine we have detected to run a few evasion switches.
For this recipe, we will perform the following steps:
- We will use the fragment packet switch to perform the discovery:
Fragment packet switch splits up the TCP header over several packets to make it harder for packet filters, intrusion detection systems, and other annoyances to detect an ongoing active scan. There could be occurrences where this could fail as some programs might not be able to handle tiny packets. For a more detailed understanding visit https://nmap.org/book/man-bypass-firewalls-ids.html.
We will enter the following command:
nmap -f <ip address>The output will be as shown in the following screenshot:

- Another switch is the
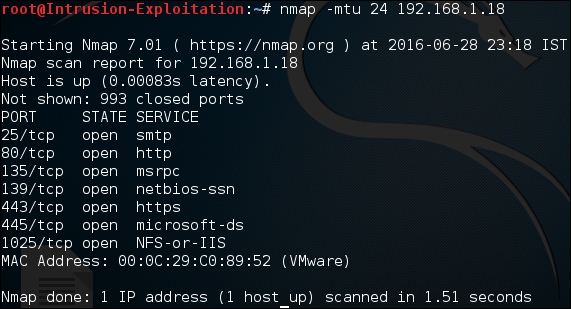
mtuswitch available in nmap, when we perform a fragment scan nmap divides the packet in 8 bytes or less, so to understand a 30 byte packet would be divided in 4 packets on respecifying-fthe packet would be divided in 16 bytes thus reducing the fragments, mtu allows us to specify our own offset size that we want to use for the purpose of scan.To perform evasion by MTU here, enter the following command in Terminal:
nmap -mtu 24 <ip address>Note
For more information on the MTU switch, refer to https://nmap.org/book/man-bypass-firewalls-ids.html.
The output will be as shown in the following screenshot:
- Here we will use a decoy attack. Enter the following command in terminal:
nmap -D <Fake IP>,<Fake IP>,<Fake IP> <Real IP>The output will be as shown in the following screenshot:

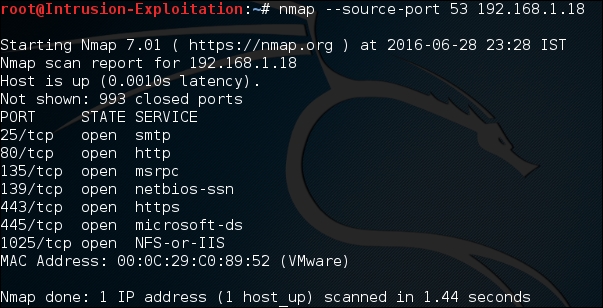
- Here we will do a custom port attack. Enter the following command in terminal:
nmap -source-port 53 <IP address>The output will be as shown in the following screenshot:
Following is an example to help you better understand the scenario:

Notice how the ports respond to a normal scan as compared to a fragmented scan. This complies that we were able to bypass the firewall and detect open ports.
Let us understand how these switches worked:
-f: This technique has been used for quite a long time over misconfigured firewalls. What it does is send the packets in smaller sizes, in order to evade the firewall.-mtu <8,16,24,32>: MTU stands for maximum transmission unit. Here we can manually specify the size of the packets; once we specify the size, nmap will send packets of the entered size to perform the scan activity.-D: This is used to spoof packets mentioning the source IP of our choice so that garbage entries are created in the logs and it becomes difficult to locate from which system the scan was initiated.--source-port: Most of the time, firewalls set an allow-incoming rule for certain ports in the network for various devices. This can be exploited by using a custom source port that might have an inbound access allowed over the system to perform the scanning activity.
