In this recipe, we will be using tools to determine what kind of operating system the target IP is running on. Mapping a target IP with a corresponding operating system is necessary to help shortlist and verify vulnerabilities.
In this recipe, we will use the nmap tool to determine the operating system. All we require is an IP address against which we will run the OS enumeration scan. Others tools that can be used are hping and xprobe2.
Let us begin by determining the operating system:
- Open terminal and type the following:
nmap -O <IP address>The output will be as shown in the following screenshot:

We can use advanced operators to help us find out the operating system in a more aggressive manner. Type the following command in terminal:
nmap O --osscan-guess <IP address>The output will be as shown in the following screenshot:
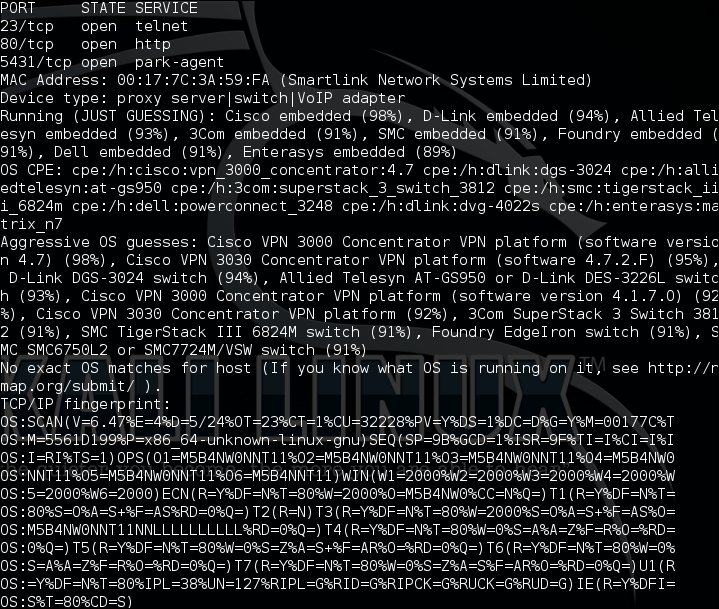
This shows that using additional parameters of the operating system detection in nmap, we can get a probable idea of the best fit.
- Xprobe2 uses a different approach to nmap. It uses fuzzy signature matching to provide the probable operating system. Open terminal and type the following command:
xprobe2 <IP Address>The output will be as shown in the following screenshot:
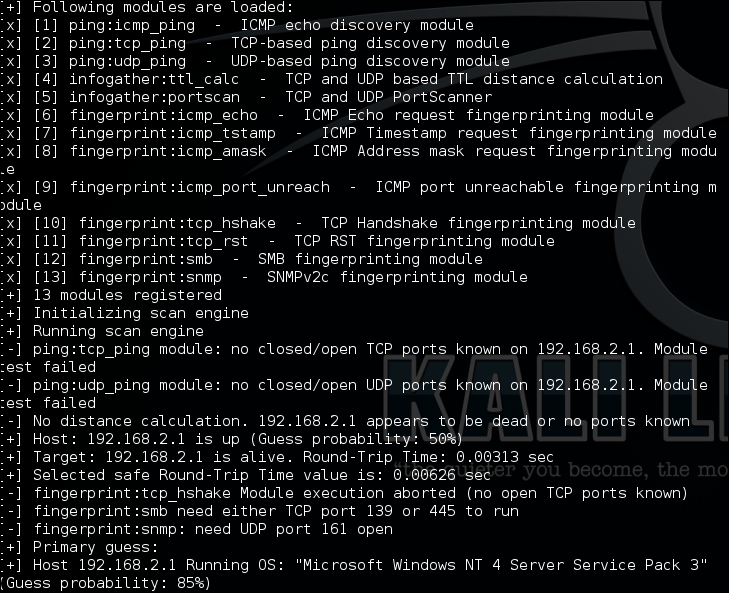
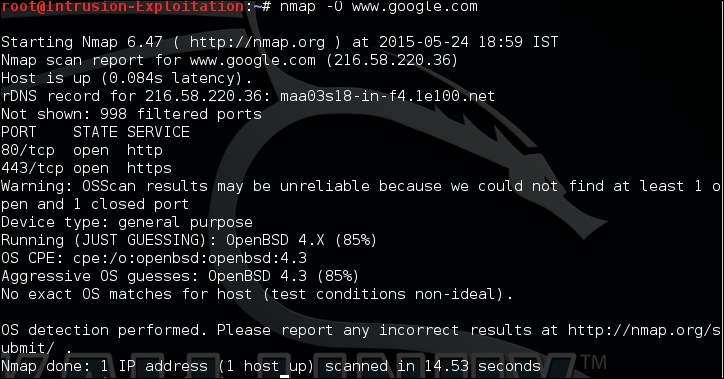
We cannot determine which is the best scanner, since every scanner has its own method of implementation. To prove what we are talking about, let's have a look at the following scenario. We set a common target for enumerating the operating system. The target is www.google.com .
The following screenshot shows the nmap result :
The following screenshot shows the Xprobe result:

Nmap performs the activity of determining the operating system based on TCP/IP stack fingerprinting. It sends a series of packets, consisting of the TCP and UDP packets, and analyzes all of the responses. It then compares them with the signatures that are available with the nmap engine to put in the best-fit operating system, and tells us what the target machine's operating system could be. In the preceding scenario, there was one target IP that did not give any operating system details; this is because the nmap tool was not able to match any responses with the signatures available in the tool.
Let's look at some details of the switches used above:
- The
-Oargument enables the nmap engine to start determining the possible OS based on the information retrieved from the banner. It mentions that it is far more effective if it finds one open and one closed TCP port on the target IP. - The
--osscan-guessargument enables the nmap engine to show the best probable matches for the detected signatures, in case it was not able to find a perfect match.
Xprobe2 has around 14 modules that can be used to scan for the detection of the type of OS running over the remote target.
In this recipe, we learned how to effectively determine the operating system using different scanners. We will now be using this information to proceed to the next recipe.
There are additional options in the nmap operating system discovery module, which are as follows:
--osscan-limit: This argument will limit detection only to the promising targets; it will skip the target if it does not find any port open. This saves a lot of time when scanning multiple targets.--max-os-tries: This is used to set the number of times nmap is supposed to try detection if it fails. By default, it tries five times; this can be set to a lower value to avoid time consumption.
