A MAC address is the unique identity of the user who tries to authenticate over a wireless network. Often as a best practice users prefer to Mac-filter their networks to protect themselves from attackers; however it is very easy to change a Mac address and attack the network. In this recipe, we are going to see how one can change the Mac address of a wireless card.
A wireless card and a Kali machine are required to perform this exercise. In this recipe, we will scan the available network and the devices connected to it, after which we will change the Mac ID of the wireless card to that of the host connected to the network.
- Before we begin, ensure that you stop Monitor mode, enabled in the previous recipe, by issuing the stop monitor command on its interface:
airmon-ng stop wlan0mon - Let us check our MAC address for our device, using the following command:
ifconfig wlan0The output will be as shown in the following screenshot:

- Now we will disable the network interface using the following command:
ifconfig wlan0 down - We now select one of the Network device and use
macchangerto change our Mac address. We will change it to a legitimate authenticated user's Mac, which can be found by running theairodump-ngcommand explained in the next recipe to see which Mac ID is connected to our target router:macchanger -m xx:xx:xx:xx:xx:xx wlan0The output will be as shown in the following screenshot:
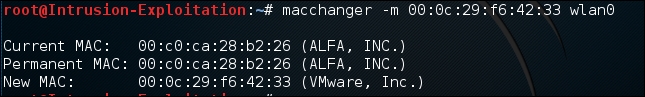
- In the absence of Mac filtering, if the user decides to maintain anonymity, a random Mac address can be obtained from:
macchanger -r wlan0The output will be as shown in the following screenshot:
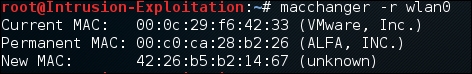
- Now we can enable the wireless device using the following command:
ifconfig wlan0 up
