In this recipe, we will look at how to make use of tools meant for online information gathering. We will cover tools that serve the purpose of gathering information with respect to Whois, domain tools, and MX mail servers. Shodan is a powerful search engine that locates drives for us over the Internet. With the help of various filters, we can find information about our targets. Among hackers, it is also called the world's most dangerous search engine.
We will make use of tools such as DNsenum for the purpose of Whois enumeration, find out all the IP addresses involved in a domain, and also how Shodan provides us with open-port information of the target searched.
The steps are as follows:
- For DNS scan, we will use a tool called DNsenum. Let us start by typing the following command in terminal:
dnsenum <domainname>The output will be as shown in the following screenshot:

- We can also use the function available to search for more subdomains via google scraping. Enter the following command:
dnsenum -p 5 -s 20 facebook.comThe output will be as shown in the following screenshot:
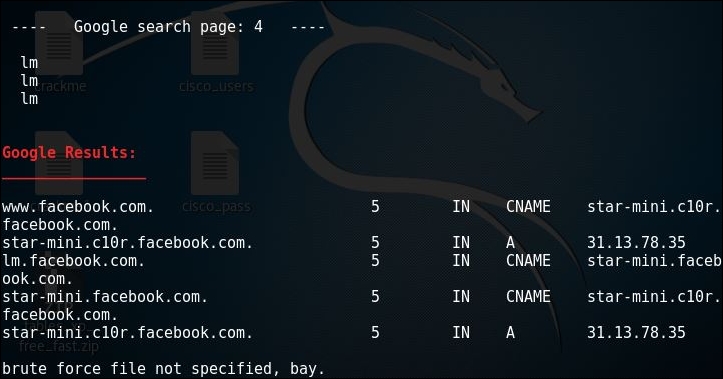
As we can see the
pand thesswitches tell dnsenum to search across 4 pages of google and the maximum number of scrape entries to be pulled from google. - Another feature of dnsenum is to provide it a list of subdomain dictionary file to find out valid subdomains and their address. The same can be done by issuing the following command:
dnsenum -f subdomains.txt facebook.comHere subdomains is a custom list of possible subdomains, we get the output as follows:

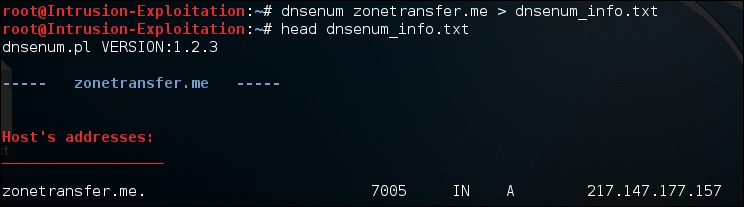
Coming back to the simplisting dns enumeration, we performed and for the ones above, it is observed that the output contains a lot of information, so it is always better to save the output in a file. One option is to use the push the output to the file using the following command:
dnsenum <domain name> > dnsenum_info.txtThe output will be as shown in the following screenshot:
How ever if we need to use the output enum for another tool we must use the switch provided in dnsenum to take the output in the XML format as majority of tools support XML import functions. Use the following command:
dnsenum -o dnsenum_info <domain name>The output will be as shown in the following screenshot:

- When we use the head command to the output file, we get the following:
- The
dnsenumcommand gives you a lot of information about your target:- Name server: Nameserver is a server that handles queries regarding the location of a domain name's various services
- MX record: This specifies the IP that corresponds to the mail server of the given host.
- Host address: This specifies the IP address where the server is hosted
- Sub domains: A subset of the main site; for example, mail.google.com and drive.google.com are sub domains of google.com.
- Reverse lookups: A way to query the DNS server with an IP address to find the domain name
- Register yourself for Shodan at http://www.shodan.io, and click on explore to browse through the available list of features that you can see.
- Now go to the Webcam section, and you will see a list of all the IPs with a webcam server running on their system.
- Let's say you manage to get the target IP or web URL; you can retrieve a lot of information just by entering the IP in the search filter, as shown in the following screenshot:
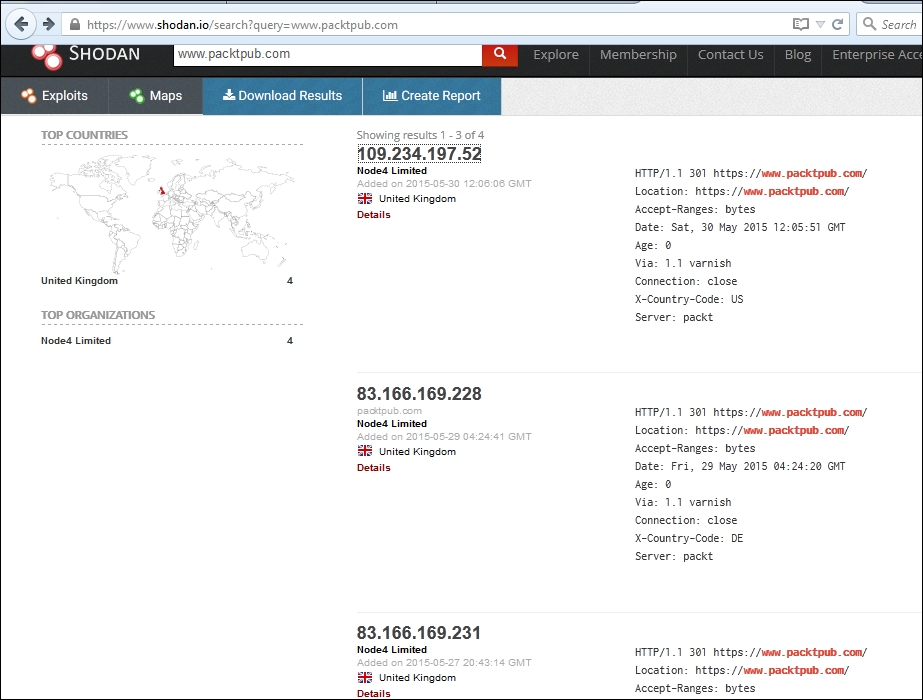
- Let's say you want to check for all the servers belonging to a country; in the search filter, enter
Country:IN.You can see how it fetches a humungous output:
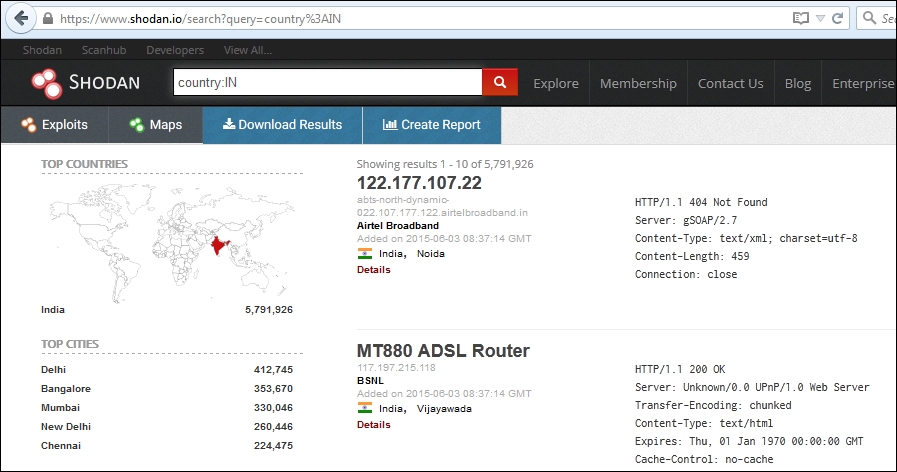
- This is how the output of a specific IP address would look:

- In the top left-hand corner, when you click on the View All... tab, you will get a list of all the available features of Shodan:
As we can see, the amount of functionality provided is vast. We should take the time to explore all the options one after another.
The dnsenum <domain name> syntax queries the DNS server of the mentioned domain name, followed by the name server and mail server. It also performs a check on whether zone transfer can take place.
The commands used work as follows:
-o: When specified with a file name, this provides an XML-based output of the DNS enumeration done-p = pages <value>: The number of google search pages to process when scraping names; the default is 20 pages; the-sswitch must be specified-s = scrap <value>: The maximum number of subdomains that will be scraped from google-f, = file <file>: Read subdomains from this file to perform brute force
Shodan has a huge list of filters; the filter used above is as follows:
- Country: This specifies the country in which to search for the given target; it is generally identified by the country code
More information gathering can be done by using the Shodan search engine.
The Shodan search engine lets a user find specific types of computers or devices over the Internet with the help of different filter combinations. This can be a great resource for gathering information about a target. We can learn more about the Shodan filters by visiting http://www.shodanhq.com/help/filters .
