In this recipe, we will learn to use a tool called WAFW00F. WAFW00F identifies and fingerprints web application firewall (WAF) products.
- WAFW00F is fairly simple and easy to use. Just open the terminal and enter the following command:
wafw00f https://www.microsoft.comThe output will be as shown in the following screenshot:
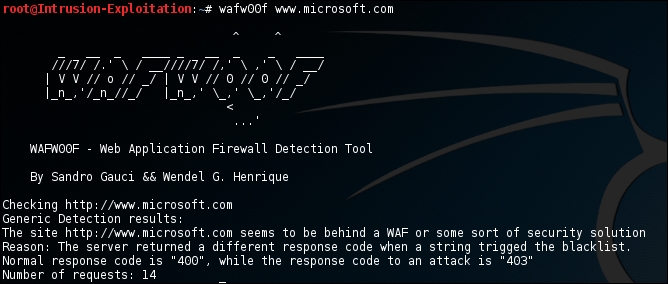
- Similarly, you can just keep changing the target domain to find the existence of the web application firewall.
In this recipe, we have used WAFW00F to identify if we do have any web application firewall running. Detecting a web application firewall accurately can help you save a lot of hours later, during penetration testing.
WAFW00F works in the following way:
- It sends a normal HTTP request and analyzes the response; this identifies a number of WAF solutions
- If that is not successful, it sends a number of (potentially malicious) HTTP requests and uses simple logic to deduce which WAF it is
- If that is also unsuccessful, it analyzes the responses previously returned and uses another simple algorithm to guess whether a WAF or security solution is actively responding to our attacks
For further details, check out the source code on the main site, github.com/sandrogauci/wafw00f .
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
