Once the services have been fingerprinted, we can perform enumeration. There can be many different sources used to achieve the goal of this recipe. In this recipe, we will look at how to perform service-discovery scans using various tools, for the following:
- SMB scan
- SNMP scan
- Using the NSE (nmap scripting engine) engine
Nbtscan is a script in Kali that enumerates for the NetBIOS name of the target IP. It can be used as the early part of SMB enumeration. It basically requests a status query of the NetBIOS name in a human-readable format.
For this recipe, the steps are as follows:
- To enumerate the NetBIOS name, we will run the following command in terminal:
nbtscan <IP address>The output will be as shown in the following screenshot:
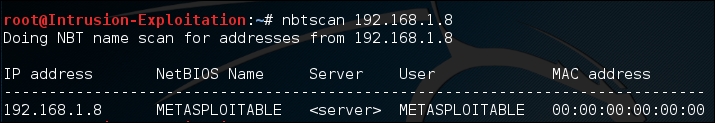
- You can run the NetBIOS enumeration over a class range as well, using the following command in terminal:
nbtscan -r <IP address>/<class range>The output will be as shown in the following screenshot:
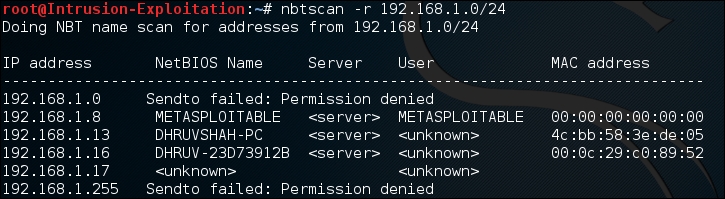
- To perform an SMB scan, we can use commands such as
enum4linux. Enter the following command in terminal to start an SMB scan:enum4linux <IP address>The output will be as shown in the following screenshot:

Additionally, it even provides share-enumeration information to check the available shares on the system:

It even shows us the password policy (if any applied) on the target:
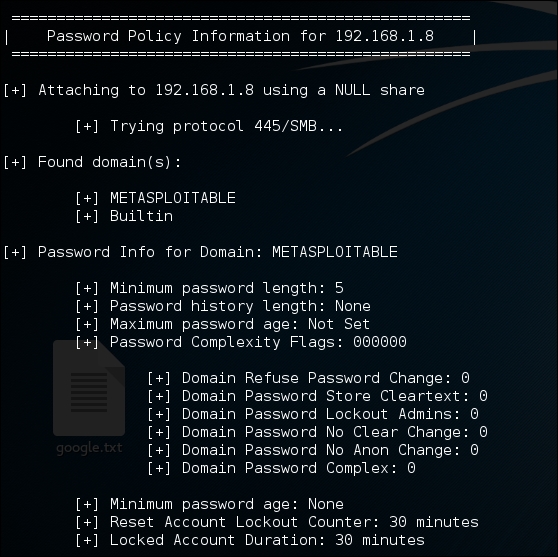
As you can see, enum4 Linux is a powerful tool, especially in the scenario where null sessions are enabled.
Note
A reference from Wikipedia to understand null sessions: A null session is an anonymous connection to an inter-process communication network service on Windows-based computers. The service is designed to allow named pipe connections. However, it can be exploited to retrieve information. For a basic understanding of null sessions, visit http://www.softheap.com/security/session-access.html . A thoroughly detailed pentest scenario can be understood at https://pen-testing.sans.org/blog/2013/07/24/plundering-windows-account-info-via-authenticated-smb-sessions .
- Let's move on to SNMP scanning. For this purpose, we will use a scanning tool called SnmpWalk and start browsing through the MIB (management information base) tree.
Start by typing the following command in terminal:
snmpwalk -c public -v1 <IP address>The output will be as shown in the following screenshot:
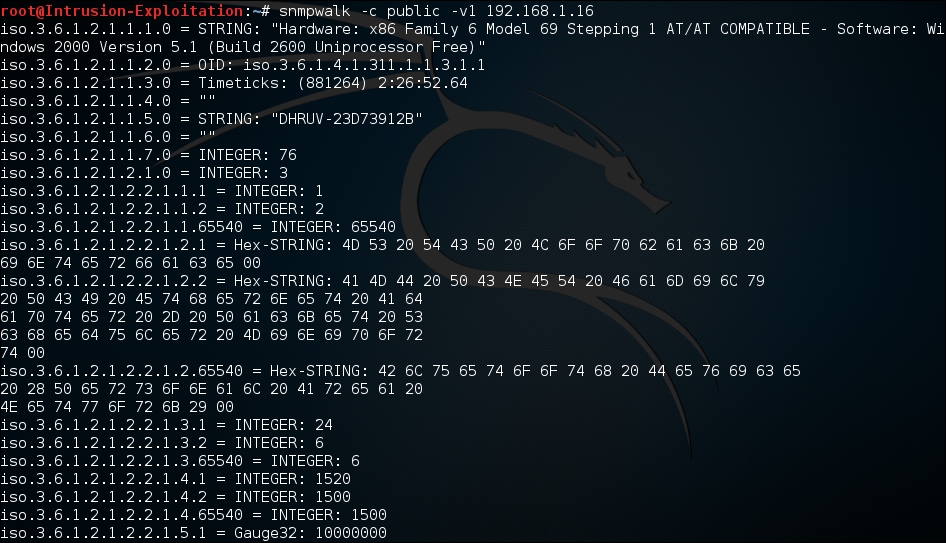
- We can see that a lot of information is fetched when we try to access the SNMP service, with the default string public if not changed. In order to make sure we do not get so much information, and to request information in an orderly manner, we can make use of the MIB tree.
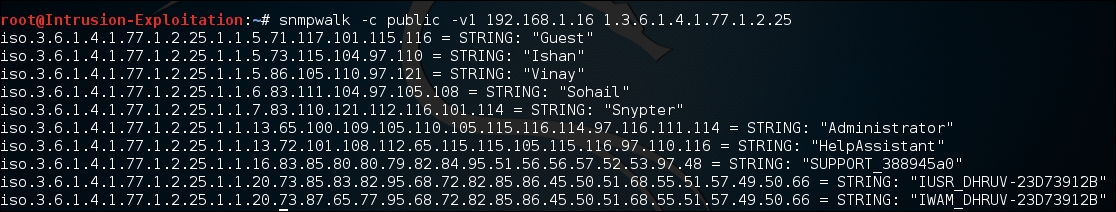
For example , if we wish to extract only system users then we can use this value
1.3.6.1.4.1.77.1.2.25, enter the following command in terminal:snmpwalk -c public -v1 <IP address> <MIB value>The output will be as shown in the following screenshot:
- We will be using nmap to find vulnerabilities in the open ports. Nmap has a huge list of scripts used for assessment purposes, which can be found at
/usr/share/nmap/scripts/. The output will be as shown in the following screenshot:
These scripts need to be updated from time to time.
Once we select a target, we will run nmap scripts over it.
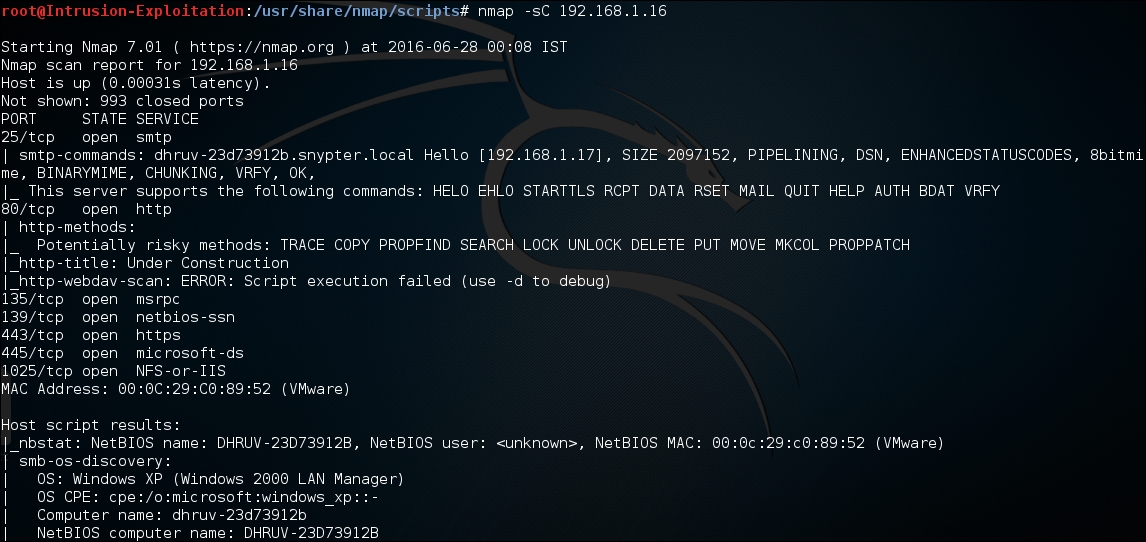
- Open terminal and type the following command to perform a script scan:
nmap -sC <IP address >The output will be as shown in the following screenshot:
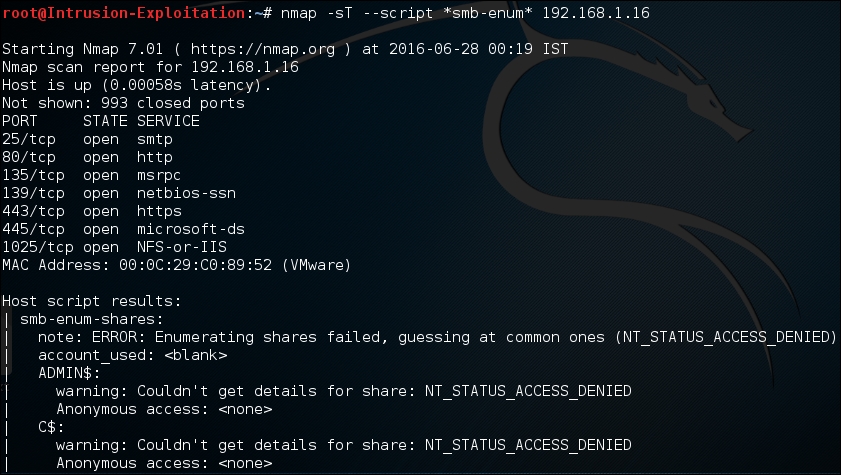
- We can even downsize the scope of scanning to specific services only. Type the following command in terminal to run all enumeration scripts related to SMB services only:
nmap -sT --script *smb-enum* <IP address>The output will be as shown in the following screenshot:
- However, we should be aware that there are certain scripts that can stall or crash the service while trying to analyze if a target is vulnerable. These can be invoked by using the unsafe args, for example, on typing the following command in terminal:
nmap -sT -p 139,443 --script smb-check-vulns --script- args=unsafe=1 <IP address>The output will be as shown in the following screenshot:
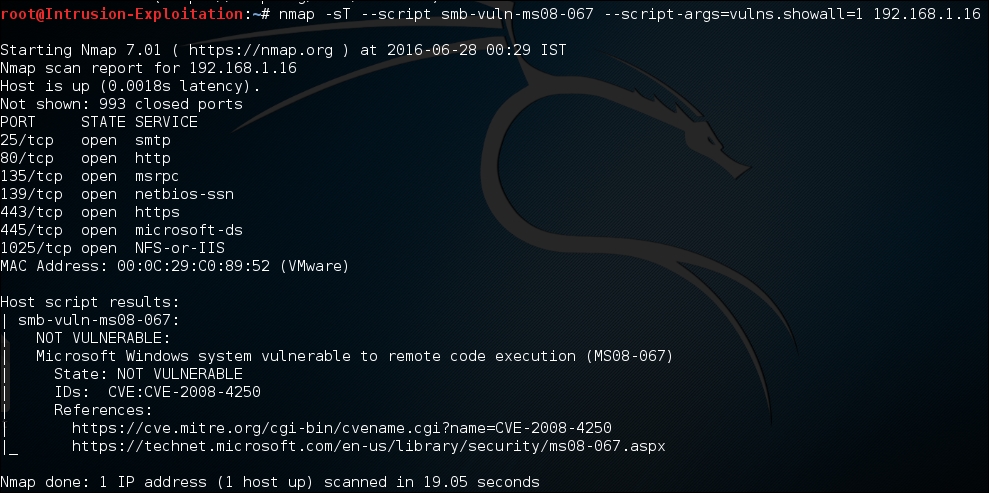
This tells us if the port is vulnerable to any attack.
Let us understand a few of the switches used in this recipe:
In Nbtscan, we used the -r switch, which tells nbtscan to scan for a given whole class network/subnet; it queries all the systems on UDP port 137. This port has a service referenced to "Network Neighborhood" also known as netbios. When this port receives a query, it responds with all the running services on that system.
The enum4linux is a script that enumerates pretty much all the possible information that includes RID cycling, user listing, enumeration of shares, identifying the type of remote OS, what the running services are, password policy, and so on, if the target IP is susceptible to null-session authentication.
Following are the switches used in SnmpWalk:
-c: This switch tells SnmpWalk what type of community string it is. By default, the SNMP community string is public.-v1: This switch specifies that the SNMP version is 1. We can even use 2c or 3 depending on the type of SNMP service version it is running on.dnsenum: This is a DNS enumeration tool. It basically enumerates all the DNS-related information from a DNS server, and even checks if it is possible for a zone transfer.-sC: This switch enables nmap to run default NSE scripts for all the open ports detected on the target IP, from the repository.--script: This switch enables us to specify which script we want to execute. We can use regex, as shown in the preceding example.--script-args=unsafe=1: This switch enables nmap to run dangerous scripts to assess if a port is vulnerable to a type of attack. The reason it is not a part of default script analysis is because, at times, these can cause the remote service to crash and be rendered unavailable, leading to a DOS situation.
In this recipe, we learned how to run different scripts on the services detected by nmap, and how to run dangerous enumeration scripts.
