In order to perform a successful credential crack, it is important to have a list of possible usernames and passwords. One of the ways this is possible is by making use of the dictionaries available in the Kali Linux Distro. These are located under /usr/share/wordlists/. The following screenshot shows the available wordlists in Kali:

You will find a rockyou.txt.gz file, which you will need to unzip. Use the following command in terminal to unzip the contents of the file:
gunzip rockyou.txt.gz
Once this is done, the file will be extracted, as shown in the preceding screenshot. This is a prebuilt list of available passwords in Kali Linux. Let us begin to formulate one of ours with the help of enumeration and information gathering.
To commence, we will first find the IP address of the hosted Stapler machine and begin enumerating information to collect and create a set of custom passwords.
The steps for the recipe are as follows:
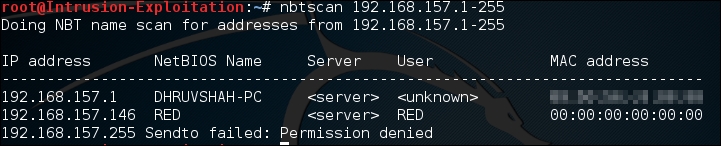
- Discover the IP address of Stapler on the subnet, using the following command:
nbtscan (x.x.x.1-255)The output will be as shown in the following screenshot:
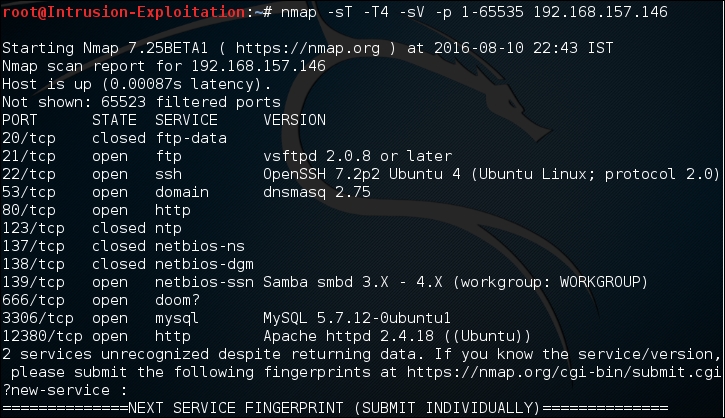
- Run a quick
nmapscan to find the available ports:nmap -sT -T4 -sV -p 1-65535 <IP address>The output will be as shown in the following screenshot:
- Connect to open ports and gather valuable information; let's enumerate the
ftp,Ssh, andhttpports. The following is a series of ways the information can be gathered and stored.Information gathering on the FTP port:
We entered the default anonymous login by entering the username and password as
Ftp: ftp.We successfully got access to the login and found a file called note. On downloading it, we got a few usernames. As a part of the information-gathering process, these were stored in a document. The same can be seen in the following screenshot:

Information gathering on SSH:
We connect to SSH using the
sshclient and gather information as shown in the following screenshot: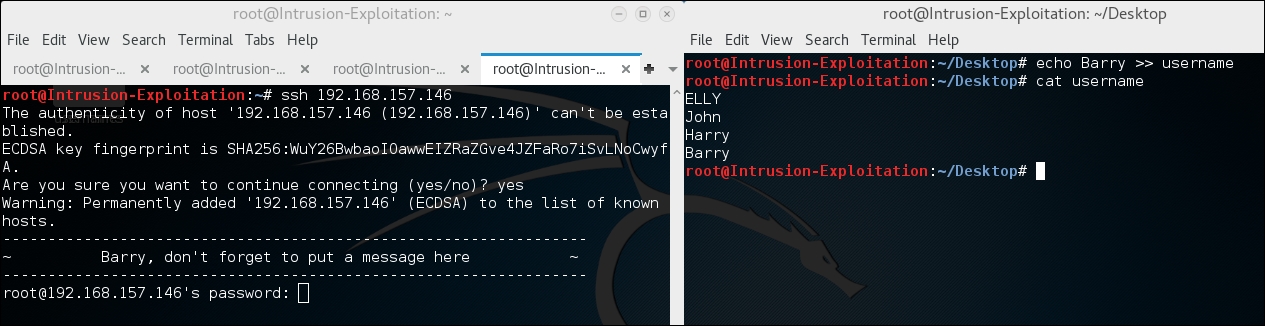
We have found one more possible username.
Information gathering on HTTP:
There are quite a few ways to gather possible useful words from the Web application. On the nmap screen, we found out that there is one port,
12380, running a web server. On visiting and trying to check forrobots.txt, we found some interesting folders as shown in the following screenshots: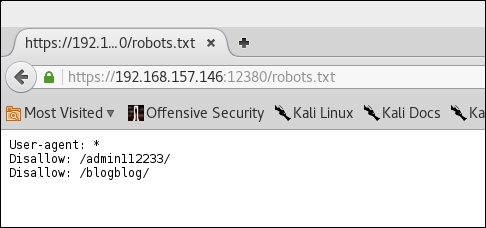

On accessing the
/blogblog/URL, we discovered that it is a WordPress site, so we'll try to enumerate the possible usernames for the WordPress blog.Use the following command to enumerate WordPress users:
wpscan -u https://<IP address>:12380/blogblog/ --enumerate uThe output will be as shown in the following screenshot:

Information gathering via shares:
Here we will gather information that will help us build our potential credentials list. Let's check how this is possible. We will run
enum4linuxon the machine, using the following command:enum4linux <IP address>The output will be as shown in the following screenshot:

Share enumeration via
enum4linuxlooks similar to the following screenshot: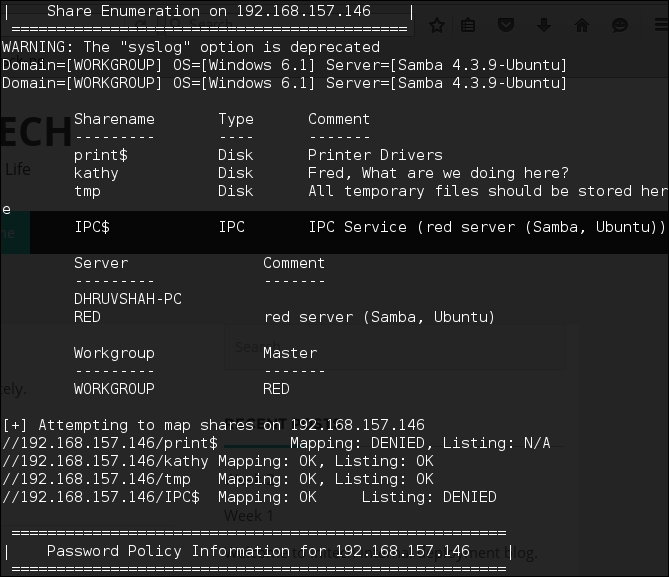
On doing so, we realize that there are more usernames available, and hence, we can add them to our username list. On further assessment, we hit the jackpot: the available usernames on the server. SID enumeration via
enum4linuxlooks similar to the following screenshot: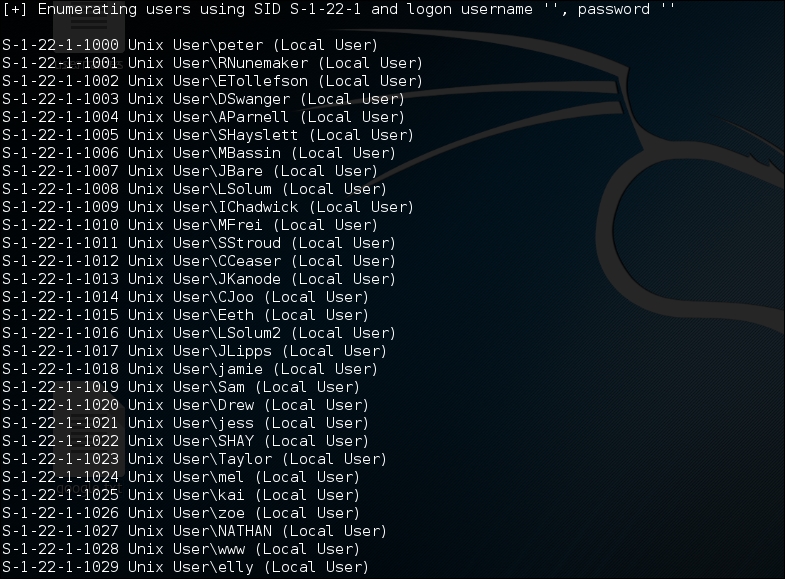
- Now an entire list of usernames is formulated and stored in the username file, which looks as shown in the following screenshot:
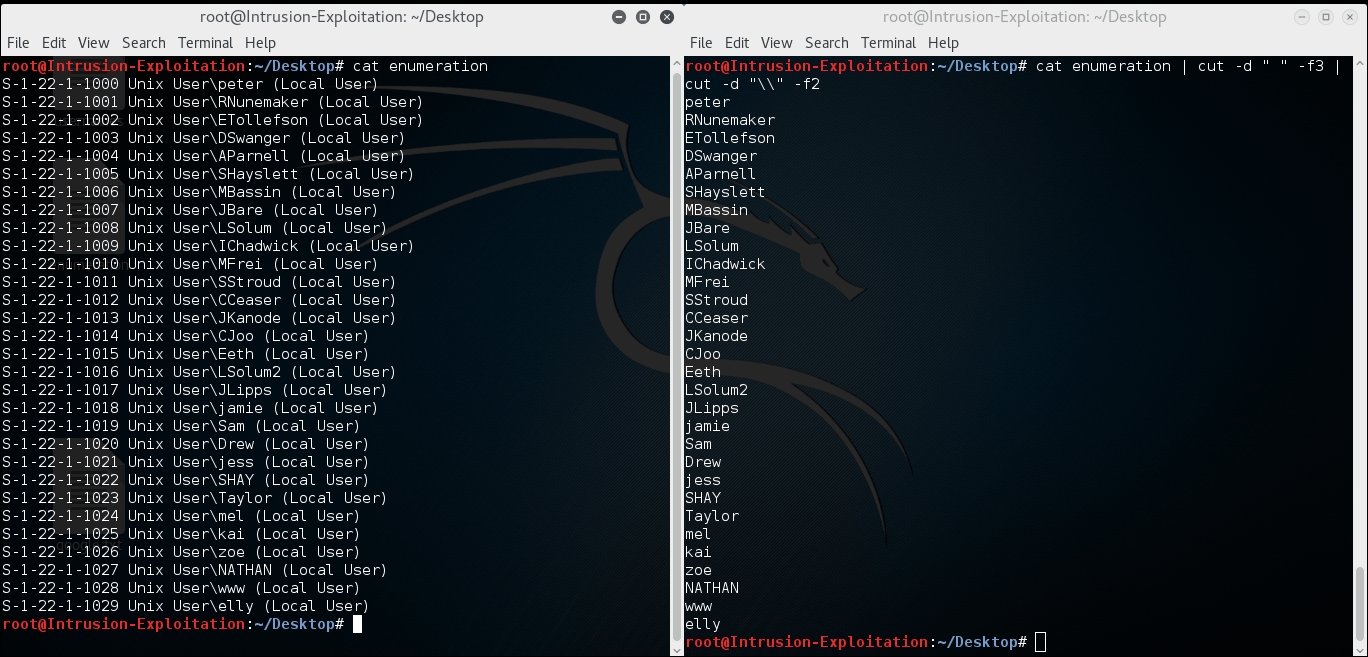
Let's do the same for the Metasploitable 2 machine. In our testing lab, the Metasploitable 2 machine is hosted at
192.168.157.152. We have created a customgrepthat will enumerate the share for users and also give only the username as output:enum4linux <IP address> | grep "user:" |cut -d "[" -f2 | cut -d "]" -f1The output will be as shown in the following screenshot:

Once this is done, save the usernames in a file of any name. In this case, we name it
metasploit_users. This can be done by redirecting the output of the preceding command using the following command:enum4linux <IP address> | grep "user:" |cut -d "[ " -f2 | cut -d "] " -f1 > metasploit_usersWith this, we have completed the first recipe of information gathering to build a credible credentials dictionary. In the next recipe, we will look at how to make use of this to attack and try to gain access to the server.
