By now it is evident that nmap plays a very important role right from IP discovery. Nmap also has a vulnerability assessment functionality, which is achieved via the Nmap Scripting Engine (NSE). It allows the user to run vulnerability detection scripts. The NSE contains a very large set of scripts that range right from discovery to exploitation. These scripts are available in the nmap folder, and are segregated by their categories. These categories can be better understood by reading the scripts.db file, located in the nmap folder. However, in this chapter we will limit ourselves to vulnerability detection.
In order to begin this chapter, we will be using nmap to check the NSE scripts located in nmap under the scripts folder. For demonstration purposes, we will be using Metasploitable 2 and Windows XP SP1.
The steps for this recipe are as follows:
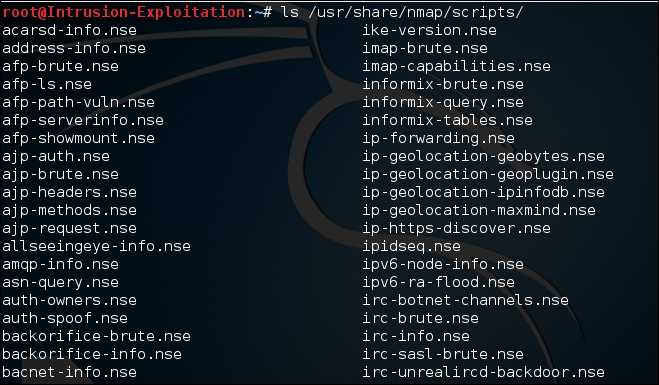
- We should first see where the NSE scripts are located. Type the following command:
ls /usr/share/nmap/scripts/The output will be as shown in the following screenshot:
- In order to understand all the different categories that these scripts belong to, type:
cat /usr/share/nmap/scripts/script.db | grep "vuln"The output will be as shown in the following screenshot:
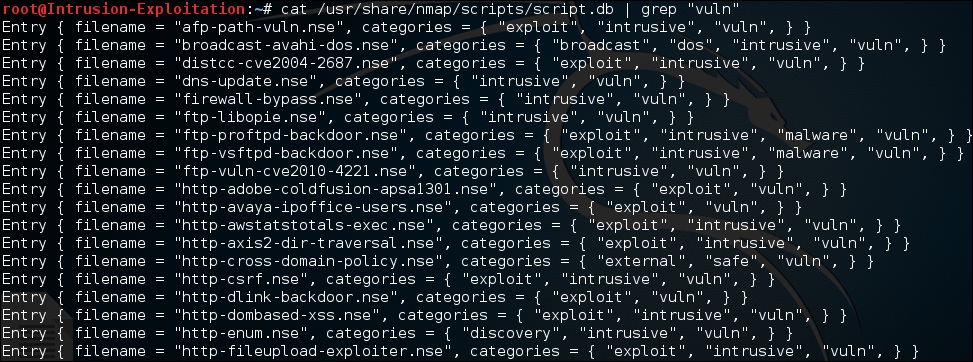
- You might notice from the preceding screenshot that there is a category called
vuln. We will be working mainly with this category. To run a simplevulncategory scan, use the following command on your terminal window:nmap -sT --script vuln <IP Address> - Let's say we want a quick assessment of just a few sets of ports. We can run a port-based
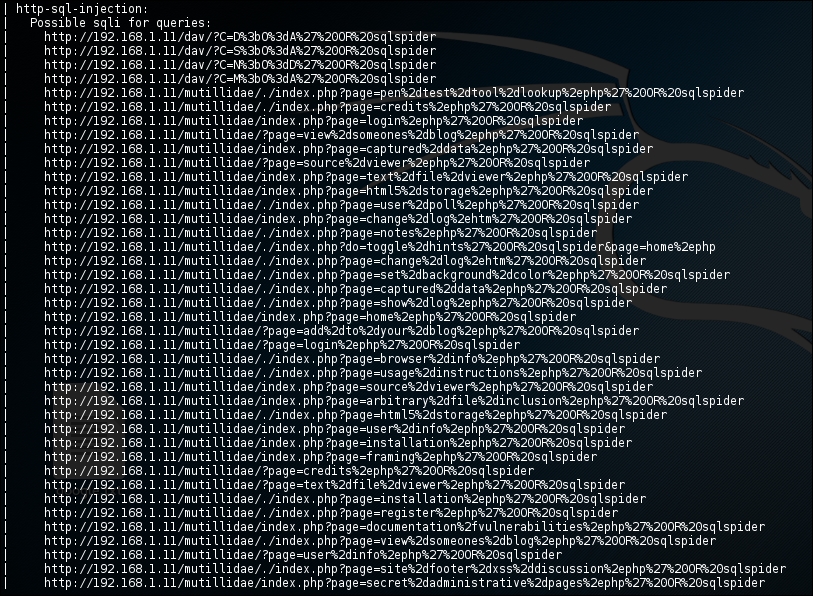
vulnassessment scan:nmap -sT -p <ports> --script vuln <IP Address>The output will be as shown in the following screenshot:

We can see that it revealed a lot of information, and showed us many possible attack vectors; it even detected the SQL injection for a potential attack:
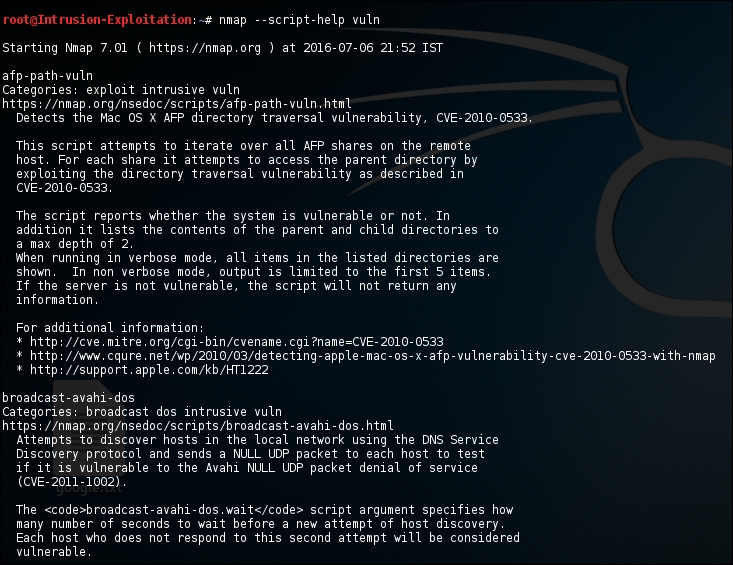
- Let's say we want to know the detail of what the script category
vulndoes. We can simply check that by typing the following command in the terminal:nmap --script-help vulnThe output will be as shown in the following screenshot:
- Let's check whether the remote machine that is running is vulnerable to SMB. We first find out whether the SMB port is open:
nmap -sT -p 139,445 <IP address>The output will be as shown in the following screenshot:
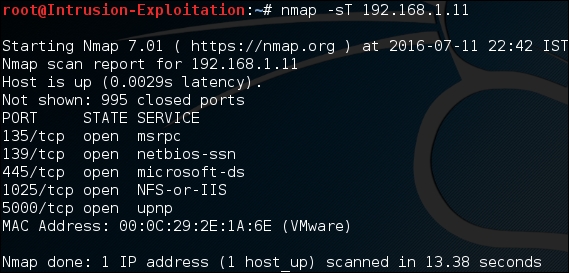
- Once we detect that the port is open, we run an
smbvulnerability detection script, shown as follows:nmap -sT -p 139,445 --script smb-vuln-ms08-067 <IP address>The output will be as shown in the following screenshot:
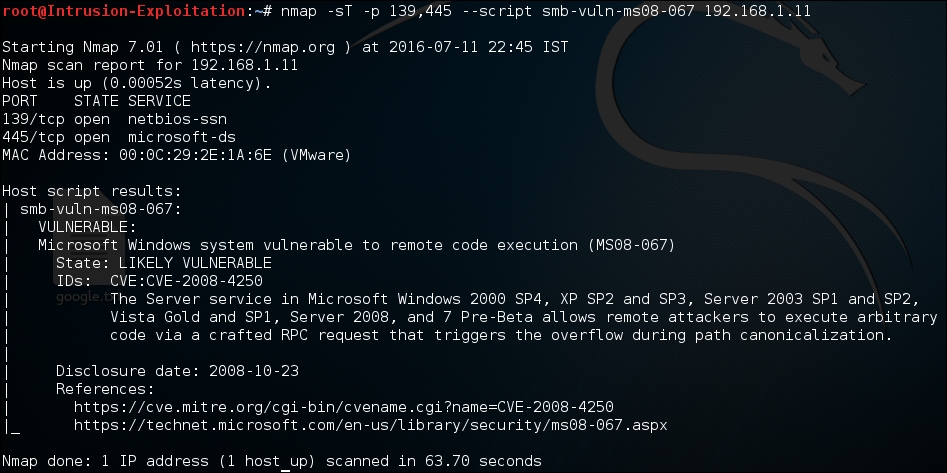
So, one can use the various scripts available in nmap with the category of
vulnto perform an assessment over the target IP and find vulnerabilities based on the port and services running.
Understanding all the parameters is rather easy; we have been toying with the scripts available in the NSE engine. Let's understand a few of the commands used in this method:
- The
scripts.dbfile contains all the NSE categorizing information that it uses to specify which scripts can be considered a particular kind of vulnerability. There are different categories, such asauth,broadcast,brute,default,dos,discovery,exploit,external,fuzzer,intrusive,malware,safe,version, andvuln. - In the preceding example, we ran an
nmapcommand with thevulnparameter along for the script. We were simply instructing nmap to use thevulncategory and run all the scripts that are categorized undervuln.
- At one point, we specified an additional port parameter to the
vulncategory scan. This just makes sure that the script only runs for the specified ports and not the other ones, thereby saving us a lot of time. - The
--script-help <filename>|<category>|<directory>|<expression>|all[,...]command is the help feature for the NSE engine. Thehelpcommand should always be accompanied by the category or a specific filename of the NSE script, or an expression. For example, to check for all SMB-related help, one can simply use the expression*smb*. - In the
--script-args=unsafe=1command, thescript-argssyntax is similar to the additional parameters to be passed to the script that we just selected; in this scenario, we are passing an additionalunsafeparameter with the value1, stating that the script has permission to run dangerous scripts that could cause a service crash.
We have learned how to use the NSE for vulnerability assessment. The script-args parameter is used for many purposes, such as providing the file for username and passwords, specifying the credentials for a given service so that the NSE can extract information, post authentication, and so on. This is recommended so that you have a deeper insight of the script-args feature.
- More information can be found in the NSE documentation at https://nmap.org/book/nse-usage.html .
