In this recipe, we will learn to use the DirBuster tool. The DirBuster tool looks for hidden directories and files on the web server. Sometimes, developers will leave a page accessible but unlinked; DirBuster is meant to find these files, which might have potential vulnerabilities. This is a Java-based application developed by awesome contributors at OWASP.
- Launch DirBuster from the Kali Linux | Web Application Analysis | Web Crawlers and Directory Brute | Dirbuster, as shown in the following screenshot:

- Open DirBuster and enter your target URL; in our case, we will enter
http://demo.testfire.netfor the purpose of demonstration, as shown in the following screenshot:
- Select list based brute force. Browse and navigate to
/usr/share/dirbuster/wordlistsand selectdirectory_list_medium.txt, as shown in the following screenshot: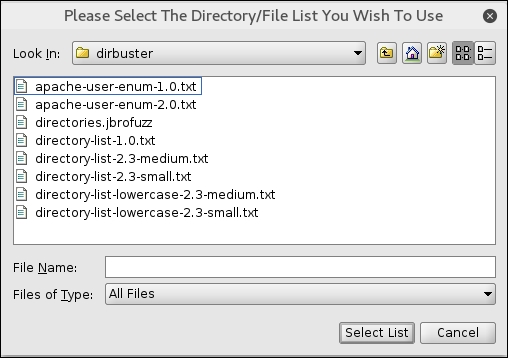
- Click on Select List and enter
php(based on the technology used by target) in the file extension column, as shown in the following screenshot: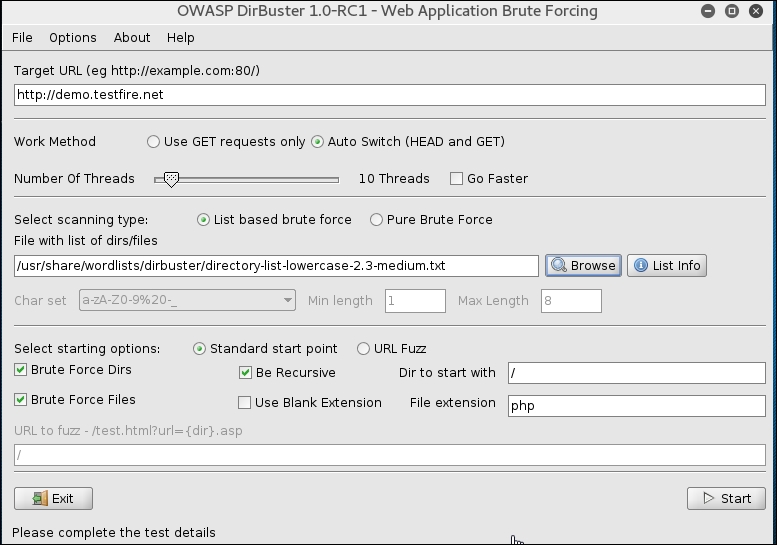
- Click on Start and DirBuster will start brute forcing directories and files, as shown in the following screenshot:
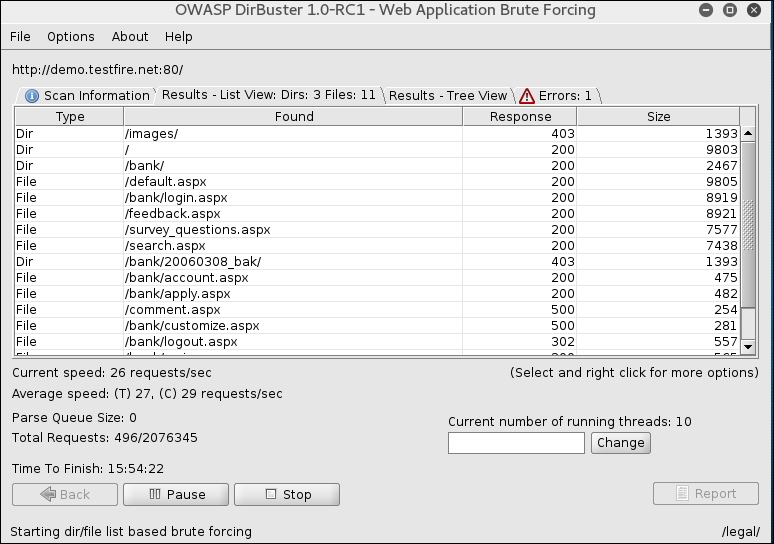
- As you can see, DirBuster has started brute forcing files and directories. You can click on the Response column to sort all files/folders with 200 HTTP code, as shown in the following screenshot:
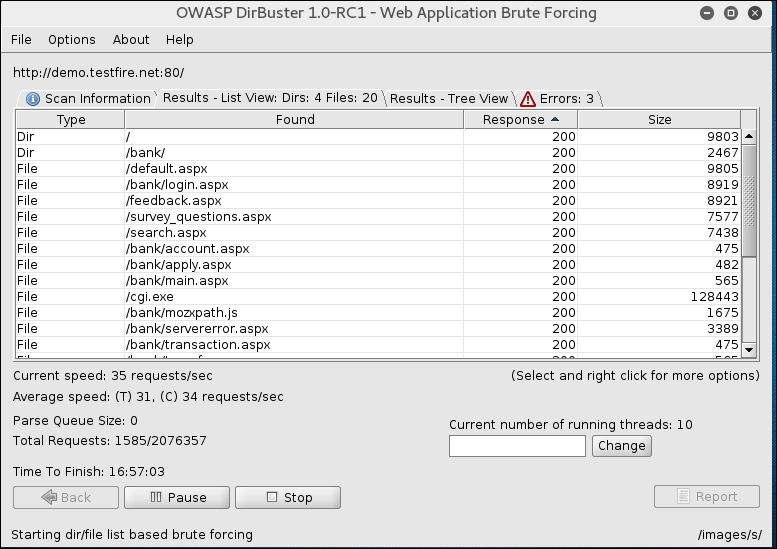
- Now you can spend some time going to each of these links and investigating which ones look interesting and could be used for further attacks. For example, in our case file, the
/pr/docs.xmlfile seems to be the standalone file sitting on the server which isn't being mentioned in sitemap orrobots.txtfile. Right-click on that entry and select Open In Browser, as shown in the following screenshot:
- The file has been opened in the browser; as you can see, this is an XML file, which wasn't supposed to be a public file and it's not linked anywhere in the application but is accessible, as shown in the following screenshot:

- Similarly, you can keep investigating other files and folders which can divulge a good amount of information, or some backup files or development pages, which may have vulnerabilities.
In this recipe, we have used DirBuster to locate hidden directories and files available on the web server. DirBuster has a dictionary file generated of the most common web server directories and it reads values from the dictionary and makes a request to the webserver to check its existence. If the server returns 200 HTTP header code, it means the directory exists; if the server returns a 404 HTTP header code, it means the directory does not exist. However, it is important to note that HTTP status codes of 401 and 403 may also point to a file or directory being present, but not allowed to be opened unless authenticated.
At the same time, a few applications which have been architected well also return 200 OK for unknown files and folders, just to mess with tools such as DirBuster. Therefore, it is important to understand how the application is behaving, based on which you could further tune your scans policies and configurations.
This way, we were able to locate certain files and folders which were not linked within the application but were available on the web server.
