This recipe provides the steps required to complete the creation of a Service Request role.
You must meet the following prerequisites before you complete this task:
- Planning: Agree the support group analysts and categories for Service Requests (for example, use a table to capture the planning information). Plan for views and queues for security scope filtering. We will use a Service Request support team called Service Desk in this recipe. The table below shows the required planning information:
Process
Process role
SCSM Security role (template)
AD group
Categories
(classification)
Service Request
Fulfillment
Service Desk
Service Request
Analysts
SCSM - SR
SCSM - Service Desk
User account
Password resets, printer, consumables
- Installation and authorization: You need to have successfully installed the SCSM product, be a user in the SCSM Administrators role and have the SCSM console open.
- Console tasks: Create custom Service Request queues and views to reflect the organization process for managing service request fulfillment.
In this recipe, we assume you have configured the following:
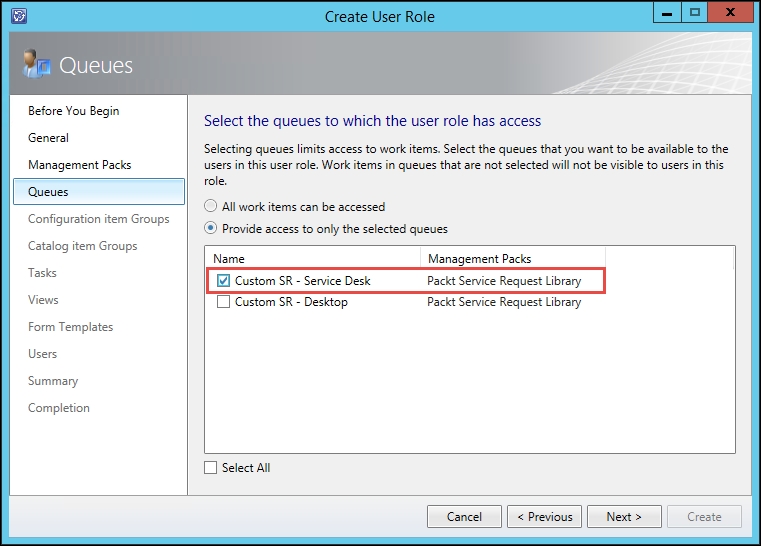
- A queue called Custom SR - Service Desk (scoped to the Service Request Class | Criteria support group = SR - Service Desk). See Chapter 3, Configuring Service Level Agreements (SLAs), for detailed steps on how to create SCSM queues.
- A view called Custom SR - All Service Desk Requests (Criteria support group = SR - Service Desk).
Follow these steps to create and manage a Service Request security role:
- Navigate to Service Manager Console | Administration | Security | User Roles.
- Select User Roles | Create User Role | Service Request Analyst from the Tasks menu:

- Click on Next in the Before You Begin wizard page.
- On the General wizard page, type the following mandatory and optional information:
- Name:
SR - Service Desk Team - Description (optional):
Service Request Role scoped for the Service Desk support group
- Name:
- On the Management Packs wizard page, select only the management packs related to Service Requests. (Include custom management packs used to store Service Request configurations.)
- On the Queues wizard page, select Provide access to only the selected queues. Select the custom queue for the role (for example, Custom SR - Service Desk). Click on Next:
- Click on Next on the Configuration item Group and Catalog item Group wizard pages.
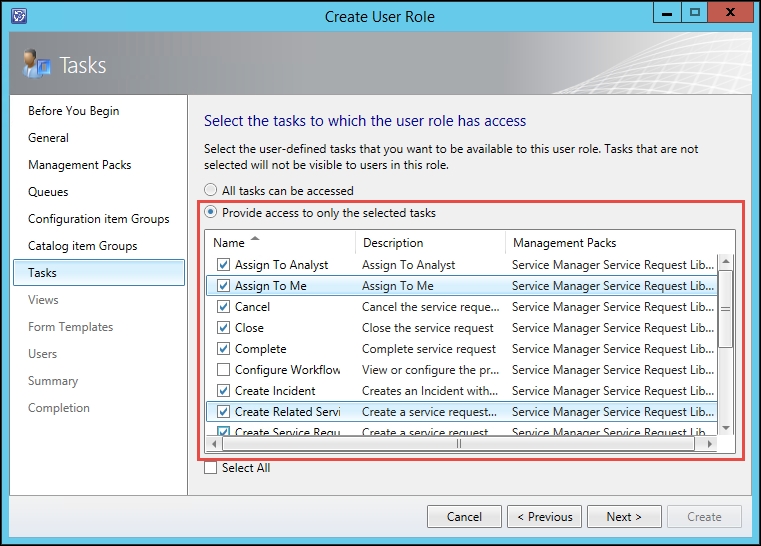
- On the Tasks wizard page, select Provide access to only the selected tasks. Select the specific tasks relevant to the role (for example, we will not select Configure Workflow Rules for this analyst role). Click on Next:
- On the Views wizard page, select Provide access to only the selected views. Select the specific views relevant to the role and click on Next:

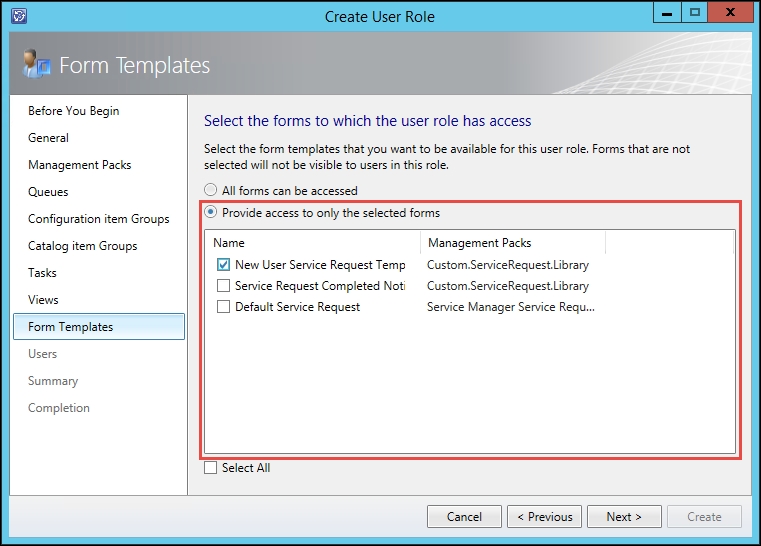
- On the Forms Templates wizard page, select Provide access to only the selected forms. Select the specific forms relevant to the role and click on Next:
- On the Users wizard page, follow the Adding Users to the End User Role task steps to select the Active Directory group for the role (as discussed in the Getting ready section of this recipe). Click on Next.
- Review the Summary page; click on Previous to correct any configurations in previous wizard pages. Then, click on Create to complete the role creation.
- Click on Close on the Completion wizard page.
Role-based security configuration and management is similar to computer file access security. Compare SCSM security delegation to granting access to files stored in a particular network location. You need to plan for the following:
|
Computer files Access Network Share |
SCSM console or portal |
|
Folders structures grouped by file type, department, or content |
SCSM Access Categories: Administration, library, Work Items, and Configuration Items |
|
Create shares to represent a logical view and abstract the physical structure |
SCSM Queues and Views |
|
Grant action permissions on the content of the folders |
SCSM Create, Delete, Edit, and category specific actions |
|
Grant permissions for actions on the host machine of the shares |
SCSM Infrastructure Administrative Settings |
|
Local Security Groups (for example, Power Users) |
SCSM built-in roles that you copy to create custom roles |
|
Grant access permission by user or groups |
Active Directory users or groups |
|
Windows Explorer and other file access tools including file processing applications |
SCSM console and portal |
The following figure presents a graphical illustration of how role-based security works in SCSM:
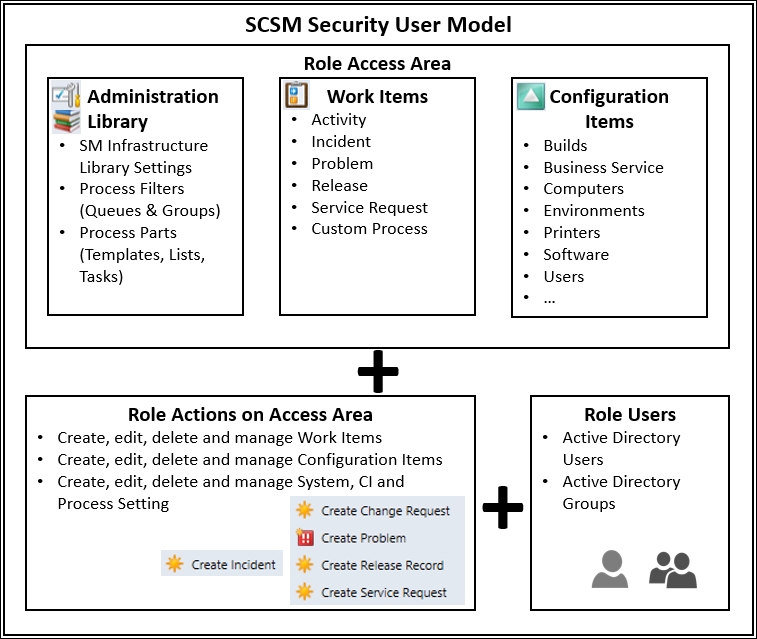
The principles of file access delegation apply to SCSM; in both cases, you must plan for roles to support the processes. In this recipe, we focused on Service Request fulfillment as a process and created a role with access to perform actions on the process objects in the scope of management. The following table is a breakdown of the wizard selection categories:
|
SCSM wizard page |
Description and notes |
|
Management packs |
This provides the means to filter what you select in subsequent wizard pages when you are creating a role. This is a major benefit of organizing your configuration in specific management packs. |
|
Queues |
Queues are similar to the principle of a fairground ticket. By default, all work items can be accessed based on the SCSM security role template (get in line for all rides). You use a queue to grant access to a subset of work items (get in line for these specific rides). |
|
Configuration Item Groups |
These are similar to queues but applicable to configuration items. For example, you can create a group for all workstation class computers and grant access to only those groups for the role. |
|
Catalog Item Groups |
These groups are specific to the service catalog and grants the role access to specific categories accessed by using the Self-Service Portal. |
|
Tasks |
The actions you can perform relevant to the process category and infrastructure settings. For example, you may be able to create and modify service requests but not be able to cancel a service request. |
|
Views |
The views selected here control what is displayed in the SCSM console for the specific role. By default, this would be the built-in system views. You must configure custom views before you create the role if you want to assign the views at the role creation stage. Views created after the security role wizard completion can be granted by editing the role. |
|
Forms templates |
These are the process templates a role user can select when creating objects in a specific process. For example, you can create a new service request using a pre-configured template. You are only presented with templates assigned to the role. The default option grants access to all process specific templates. |
|
Users |
This is where you associate the SCSM specific role with the console or portal users. |
Plan and create roles for the process instead of creating roles for specific people within a team.
There is a hidden but very important security configuration for SCSM security roles and full implication for members of the security roles. The hidden configuration is better known as implied and inherited security.
Appendix B, Useful Websites and Community Resources, provides links to useful resources on complex security models for SCSM and official online product documentation
