- The first step is to identify the data portion of the mail messages. We can use the filter to display the data portion of the mails. The use of email protocol and data will display the packets with data. For example, use pop || data-text-lines to filter the mails with data using the POP3 protocol:

- In the preceding screenshot, the data exchange between the specific endpoints is not so big. Based on the size, it appears to be a text message and does not carry any attachments, so we can ignore this:

- On the other hand, the previous capture shows that the data exchange is pretty big and it appears to carry an attachment.
- Use follow the stream to narrow down the TCP flow. This will filter and list the mail exchange in clear text as follows:
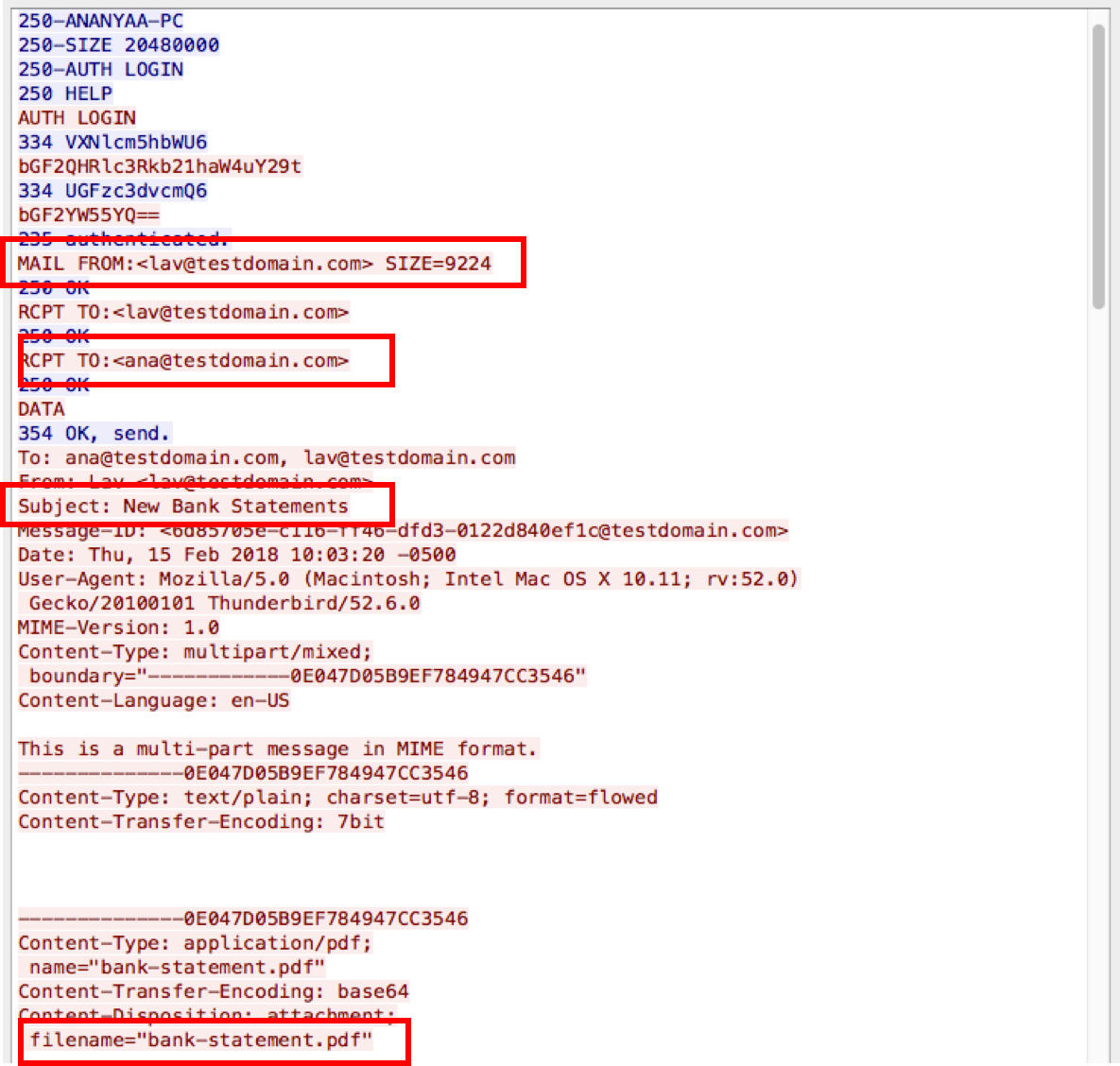
In the preceding screenshot, we can see that this email carries a PDF file. Use the sender, receiver, subject, and related information to identify whether the mail is genuine. Alternatively, we can use other malware detection software to look for any issues in the attachment.
If a similar attachment is seen on multiple emails, identify the common sender and create a spam rule in the server to mark it as spam or filter such emails directly.
