Index
A
Absorption costing, 493
Access logs, reviewing, 268
Accountants
in design/implementation team, 22
role in AIS, 22
unethical behaviors and, 23–24, 70
Accounting cycle, 517
Accounting information system (AIS). See also Foundational concepts of AIS; Types of AIS
business process to capture accounting data, 4–5
internal and external reports, 5
internal controls, 5
manual or computer-based records, 5
raw accounting data, process, classify, summarize, and consolidate, 5
Accounting software market segments, 52–54
Accounts payable fraud, 91
Accounts payable subsidiary ledger, 373
Accuracy, 187
Acknowledgment, 335
Adequate records and documents
cash collection processes, 323
cash disbursement processes, 389
fixed assets processes, 451
general ledger processes, 525
payroll processes, 438
purchase return process, 381
purchasing processes, 374
sales return processes, 315–316
Administrative processes and controls, 509–539. See also General ledger processes
capital processes, source of, 513–514
corporate governance in, 531–532
securities, 515
treasury stock, 515
underwriter, 514
AICPA Trust Services Principles, 140–145
general controls from, 140–145
availability, 140
confidentiality, 140
online privacy, 140
processing integrity, 140
security, 140
physical access risks, 145
availability risks, 142–143, 145
confidentiality risks, 142–143, 145
processing integrity risks, 142–143, 145
security risks, 141–142, 144–145
American Institute of CPAs (AICPA), 258
Analytics, 624
Antivirus software, 135
Application controls, 20, 129, 156–164, 269–274
input controls, 269
processing controls, 269–273. See also individual entry
ARPANET, 580
ASB has issued Statements on Auditing Standards (SASs), 258
Assurance services, 254
Audit committee, 183
Audit evidence, 261
Audit program, 259
Auditing information technology, 253–297
assurance services, 254
audit completion/reporting, 276–277
adverse opinion, 277
disclaimer, 277
qualified opinion, 277
unqualified opinion, 277
audit program, 259
auditing IT processes, 254
audits and auditors, types of, 254–256
certified information systems auditors (CISAs), 255
certified internal auditors (CIAs), 255
certified public accountants (CPAs), 255
compliance audits, 254
external audit, 255
financial statement audits, 255
government auditors, 255
internal auditor, 255
IT auditors, 255
operational audits, 255
authoritative literature used in, 257–259
client's IT environment changes, 280–281
different IT environments, 277–280
availability risks, 279
compliance risks, 280
IT outsourcing, 279
processing risks, 280
security risks, 279
ethical issues related to auditing, 281–285
due care, 282
integrity, 282
objectivity and independence, 282
professional skepticism, 283
public interest, 282
responsibilities, 282
scope and nature of services, 282
materiality, 261
planning phase, 261
risk, 262
management assertions, 259–261
sampling, 281
tests of controls, 265–274. See also individual entry
Auditing Standards Board (ASB), 258
Auditor of AIS, 22
Authentication, 334
of users, 130
Authenticity tests, 268
Authoritative literature used in auditing, 257–259. See also under Auditing information technology
Authority table, 132
Authorization of transactions
cash collection processes, 322
cash disbursement processes, 388–389
fixed assets processes, 450–451
general ledger processes, 520–522
payroll processes, 437
purchase return process, 381
purchasing processes, 373
sales processes, 309
sales return processes, 313–315
Automated matching, 15–16, 393
availability risks, 395
process, 393
processing integrity risks, 395
requirements, 16
security and confidentiality risks, 394–395
Automation, 441
Availability risks, 142–145, 148, 331
automated matching, 15–16, 393
defined, 143
e-business (expenditures), 398–400
evaluated receipt settlement, 395
hacking, 144
physical access, 145
B
Back office modules, 626
Backbone provider, 582
Backbone, 582
Balancing tests, 270
Batch processing, 12, 57–59, 546
characteristics, 547
determining, 546
legacy systems, 57
real-time processing versus, 547
requirements, 57
sequential access files, 12
Battery power (UPS), 138
Benford's Law, 271
Best of breed versus ERP modules, 629
Big Bang approach, 632
Bill, 307
Biometric devices, 132
Bit, 10
Blind purchase order, 371
Board of directors, 183
Bricks and clicks, 590
Bricks and mortar, 589
Business continuity planning (BCP), 139–140
disaster recovery plan (DRP), 140
off-site backup, 140
redundant arrays of independent disks (RAIDs), 139
redundant servers, 139
Business continuity risks, 145
Business process linkage throughout the supply chain, 6–8
input methods used in, 54–57. See also individual entry
internal controls, 4
types, 3
Business process reengineering (BPR), 9, 225, 327, 393, 630
in ERP system implementation, 630
IT relationship, 226
in purchasing and payments, 364
Business to business (B2B), 328, 586, 594
Business to consumer (B2C), 328, 586–587
Byte, 10
C
Capital budget, 445
Capital processes
risks and controls in, 516
unethical management behavior, 529–530
Cardinality, 67
Cases, this book
administrative processes/controls, 538–539
auditing IT-based processes, 294–295
conversion processes/controls, 502–506
corporate governance, 208
e-commerce and e-business, 612–615
expenditure processes, 415–421
fraud, ethics, and internal control, 121–124
internal controls/risks in IT systems, 173–175
payroll and fixed asset processes, 467–471
sales and cash collection processes, 352–359
Cash collection processes, 299–362. See also Revenue processes; Sales processes
cash receipts journal, 318
IT-enabled systems of, 325–328
remittance advice, 318
risks and controls in, 322–325
Cash collections, 302
Cash disbursement processes, 383–388
accounts payable records, 386
cash disbursements journal, 387
cash management, 383
remittance advice, 387
risks and controls in, 388–391
Cash disbursements journal, 387
Cash management, 383
Cash receipts journal, 318
Cash receipts theft, 91
Centralized processing, 559–560
Certified fraud examiners (CFEs), 285
Certified information systems auditors (CISAs), 255
Certified internal auditors (CIAs), 255
Certified public accountants (CPAs), 255
Channel stuffing, 337
Character, 544
Check fraud, 92
Checks
dual signature, 389
fraud, 92
writing, 383
Chief executive officer (CEO), 89, 216
Chief financial officer (CFO), 89, 216
Chief information officer (CIO), 216
Clicks and mortar, 590
Client server, cloud computing and, 51
Client's IT environment changes, 280–281
Client-server computing, 47–48
characteristics, 48
clients, 626
defined, 47
distributed applications, 48
distributed presentation, 48
servers, 617
task assignment, 47
web-based model, 48
Cloud-based databases, 561–562
Cloud computing, 14, 48–52, 154–156
advantages, 49
cost savings, 50
expanded access, 49
reduced infrastructure, 50
scalability, 49
availability, 154
and client server, 51
as a conceptual design, 232
confidentiality, 155
disadvantages, 50
infrastructure is reduced, 154
processing integrity, 155
public cloud computing, 154
security, 154
COBIT, 109
company development/adherence, 20
defined, 282
as documented guidelines, 86
due care, 282
for financial officers, 195
objectivity and independence, 282
public interest, 282
responsibilities, 282
scope and nature of services, 282
Collusion, 91
Committee of Sponsoring Organizations (COSO) Report, 18, 85, 99–107, 113, 184
accounting internal control structure, 20
control activities, 102–106. See also individual entry
information and communication, 106–107
internal control environments, characteristics, 100
risk assessment, 101
Committee of Sponsoring Organizations of the Treadway Commission (CSOTC), 85n3
Common carrier, 366
Communities, 184
Company
ethical responsibilities of, 564–565
access, 565
choice and consent, 564
collection, 564
disclosure to third parties, 565
employees, 566
management, 564
monitoring and enforcement, 565
notice, 564
quality, 565
security for privacy, 565
use and retention, 565
Compensating control, 103
Completeness check, 162
Compliance audits, 254
Computer-aided design (CAD) techniques, 490
Computer-aided manufacturing (CAM), 491
Computer-assisted audit techniques (CAATs), 265, 271
embedded audit modules, 272–273
integrated test facility (ITF), 271–272
list of, 272
Computer-based matching, 393–394
risks and controls in, 394–395
availability risks, 395
processing integrity risks, 395–396
security and confidentiality risks, 394–395
Computer fraud
denial of service (DoS) attack, 95
input manipulation, 93
output manipulation, 93
program manipulation, 93
salami technique, 94
trap door alteration, 94
Trojan horse program, 94
Computer-integrated manufacturing systems (CIMs), 492
Computer log, 132
Computers and IT concepts, 10–14. See also under Information technology (IT) enabled business processes
file access and processing modes, 11–12
Concurrency, 547
Confidentiality risks, 142–145, 148, 330–331
Configuration tables, 133
Conflicting abilities, 637
Consolidation, 558
adequate records and documents, 103–105
batch totals, 105
categories, 102
authorization, 102
general authorization, 102
specific authorization, 102
compensating control, 103
security of assets and documents, 105
segregation of duties, 103
factors of, 101
Control objectives for IT (COBIT), 114–115, 213
Control structures types of, 18. See also Internal control structure of organizations
Controls, 265–274, 363–423. See also Tests of controls
in IT, 110
availability, 110
confidentiality, 110
online privacy, 110
processing integrity, 110
security, 110
corporate governance in, 494
cost accounting reports generated by, 485–486
computer-aided design (CAD) techniques, 490
computer-aided manufacturing (CAM), 491
computer-based conversion process, 490
computer-integrated manufacturing systems (CIMs), 492
computerized systems, 490
database containing conversion process, 490
enterprise-wide resource planning (ERP), 491
industrial robots, 491
just-in-time (JIT) production systems, 492
manufacturing resource planning (MRP-II), 491
materials resource planning (MRP), 491
radio-frequency identification (RFID) systems, 492
logistics function, components of, 477–485. See also Logistics function
risks and controls in, 486–489
authorization of transactions, 486
cost–benefit considerations, 488–489
independent checks and reconciliation, 487–488
physical inventory count, 488
physical inventory reconciliation, 488
security of assets and documents, 487
segregation of duties, 486–487
Corporate governance, 20–21, 179–209. See also Sarbanes–Oxley Act of 2002
in administrative processes and reporting, 531–532
in conversion processes, 494
in expenditure processes, 403–404
in fixed assets processes, 457–459
ethical conduct, 189
financial stewardship, 188–189
internal controls and compliance, 186–188
audit committee, 183
board of directors, 183
communities, 184
creditors, 184
customers, 184
employees, 183
external auditors, 184
internal auditors, 183
investors, 184
management team, 182
regulators, 184
shareholders, 183
stakeholders, 181
suppliers, 184
in revenue processes, 339
tone at the top, 181
Corrective controls, 99
Cost accounting reports by conversion processes, 485–486
periodic inventory systems, 486
perpetual inventory systems, 485
standard costs, 485
variances, 486
Cost–benefit considerations, 105, 310–313, 324–325, 375–376
cash collection processes, 324–325
cash disbursement processes, 390–391
fixed assets processes, 453
payroll processes, 440
purchase return process, 382–383
sales return processes, 316–318
Cost savings, 154
Credit card fraud, 92
Credit limit, 303
Credit memorandum, 313
Creditors, 184
Crew, J., 328
Customer fraud, nature of, 92. See also under Fraud
Customer relationship management (CRM), 621, 625–626
Customers, 184
Customers, ethical responsibilities of, 566
Cutoff, 372
D
Data, 541–576. See also Distributed data processing (DDP); Normalized data
information, 542
standardizing, 556
storing and accessing data, 544–545
structured data, 543
unstructured data, 543
uploading, 556
Data analysis software (DAS), 276
Data flow diagram (DFD), 65–67, 313
standard procedures for, 160–161
data preparation, 160
online analytical processing (OLAP), 557–559
Data processing techniques, 546–547
batch processing, 546
real-time processing, 546
Data redundancy, 547
Data segments, 332
Data structures, computer, 10–11
Data warehouse, 12–13, 554, 618
building, 555
Database administrator, 137
Database as a Service (DaaS), 49, 232, 561
Database management system (DBMS), 150, 548
accounts payable, 150
inventory, 150
purchasing, 150
Databases, 10, 149–150, 278, 547–551. See also Cloud-based databases
attributes, 549
concurrency, 547
data redundancy, 547
flat file database model, 549–550
hierarchical database model, 550
network database model, 551
relational database model, 551
storage, trade-offs in, 554
Debit memo, 379
Defalcation, 87
Delta Air Lines, 328
Denial of service (DoS) attack, 95
Depreciation schedule, 447
Design or implementation team of AIS, 22
Detailed design, 219
Detective controls, 99
Digital Equipment Company (DEC), 580
Direct cutover conversion, 237
Disaster recovery plan (DRP), 140
Disbursements journal, 436
Distributed data processing (DDP), 559–561
Distributed databases (DDB), 560
Documentation review, 224
Documenting processes and systems, 60–69
data flow diagrams (DFD), 65–67
entity relationship (ER) diagrams, 67–69
Documenting the system, 236
Domain name servers (DNS), 584
Domain name, 584
Drill down, 558
Dual signature, 389
Dynamics ERP, 54
E
Earnings management, 87, 189, 493
availability risks, 331
confidentiality risks, 330–331
IT infrastructure for, 615–647
data warehouse, 618
enterprise resource planning (ERP), 616–619
manufacturing resource planning (MRP), 617
operational database, 618
SAP in data processing, 620
Y2K compatible, 620
processing integrity risks, 330–331
risks and controls in, 328–331
eBusiness Transitionary Working Group (eBTWG), 73
E-business, 15, 56–57, 398–400, 577–614
risks and controls in, 398–400
E-commerce, 56–57, 327, 577–614
advantages of, 329
for the business
privacy expectations in, 590–592
access, 591
choice and consent, 591
collection, 591
disclosure to third parties, 591
management, 590
monitoring and enforcement, 591
notice, 590
quality, 591
security for privacy, 591
use and retention, 591
traditional commerce and, 589–590
Economic feasibility, 231
Economic order quantities (EOQ), 480
Electronic data interchange (EDI) systems, 15, 153, 234, 327, 331–335, 398–400
availability, 400
characteristics of, 15
intercompany, 15
data segments, 332
header data, 332
labeling interchanges, 332
processing integrity, 399
authentication, 334
availability, 334
confidentiality, 333
intrusion detection, 398
penetration testing, 398
processing integrity, 334
security and confidentiality, 399
security, 333
vulnerability testing, 398
trailer data, 332
value added networks (VANs), 332
Electronic data interchange (EDI), 56, 601, 619
traditional EDI, 602
Electronic funds transfer (EFT), 603
Electronic invoice presentment and payment (EIPP), 16, 229, 400, 594
Embedded audit modules, 272
Emergency power supply (EPS), 138
collusion, 91
defined, 91
ethical responsibilities with data, 528–529
kickbacks, 91
larceny, 91
nature of, 91
skimming, 91
types, 91
ethical responsibilities of, 566
ghost, 456
hiring, 429
personnel records, 429
protection for, 195
public key, 134
salaried, 434
as stakeholders, 183
symmetric, 134
training (ERP systems), 631
training, 236
Encryption, 335
Enterprise application integration (EAI), 46
Enterprise resource planning (ERP), 16, 616–619
current ERP system characteristics, 621–622
best of breed versus ERP modules, 629
customization of ERP system, 630
hiring a consulting firm, 628
modules, 629
training of employees, 631
Oracle, 626
Peoplesoft, 626
SAP, 626
methods of conversion to, 632–634
Big Bang, 632
location-wise implementation, 633
modular implementation, 634
analytics, 624
customer relationship management (CRM), 625
financials, 623
human resources, 624
procurement and logistics, 624
product development and manufacturing, 624
sales and services, 624
supply chain management (SCM), 624–625
and Sarbanes–Oxley Act, 637–639
Enterprise risk management (ERM), 18
Enterprise-wide resource planning (ERP), 491
Entities, 67
Entity relationship (ER) diagrams, 67–69
attributes, 67
cardinality, 67
entities, 67
Environmental factors
risks from, 144
availability risks, 144
processing integrity risks, 144
Errors avoidance, policies to assist in the and errors, 96–97
E-tailers, 589
Ethical considerations
Ethical issues
in administrative processes and reporting, 528–531
in conversion processes, 493–494
in expenditures processes, 401–403
internal reporting of, 530–531
Ethical responsibilities
of company, 564–565. See also under Company
of customers, 566
Ethics and corporate governance, 200–202
Ethics, 83–125. See also Code of ethics
Evaluated receipt settlement (ERS), 16, 395–396
risks and controls in, 397–398
processing integrity, 397
security and confidentiality, 397
Exception reports, 558
Exercises, this book
administrative processes/controls, 536–537
AIS foundation concepts, 77–78
auditing IT processes, 292–293
conversion processes/controls, 499–501
corporate governance, 207
data and databases, 572
e-business and e-commerce, 610–611
ERP systems, 644
expenditure processes, 411
fraud, ethics, and internal control, 118–119
internal controls and risks, 170–172
payroll and fixed asset processes, 464–465
Expanded access, 154
Expenditures processes, 363–423. See also Cash disbursement processes; Purchasing processes; Purchase return process
corporate governance in, 403–404
Expense account fraud, 91
Exposure areas in IT system, 146
eXtensible Business Reporting Language (XBRL), 601
for financial statement reporting, 603–604
eXtensible Markup Language (XML), 601
External audit, 255
External auditors, 184
External sources of computer fraud, 94–96. See also under Computer fraud
Extranets, 14
internal controls for, 599–600
F
economic feasibility, 221, 231
operational feasibility, 221, 231
schedule feasibility, 221, 231
technical feasibility, 221, 230–231
Fiduciary duty, 188
Field check, 161
access and processing modes, 11–12
batch processing, 12
data mining, 13
online processing, 12
operational database, 12
random access, 11
real-time processing, 12
sequential access, 11
Financial Accounting Standards Board (FASB), 185
Financial statement audits, 255
Financial statement reporting, XBRL for, 603–604
Financial stewardship, 198
Finished goods inventory, 480
Firewall, 133
Fixed asset processes, 427
Fixed asset subsidiary ledger, 446
Fixed assets disposals, 447–449
Fixed assets processes, 442–450
capital budget, 445
corporate governance in, 457–459
depreciation schedule, 447
ethical issues related to, 455–457
fixed asset acquisitions, 442–446
fixed asset subsidiary ledger, 446
fixed assets continuance, 446–447
fixed assets disposals, 447–449
risks and controls in, 450–453
Flat file database model, 549–550
Foreign Corrupt Practices Act (FCPA), 113, 190
Forensic auditing, 285
Foundational concepts of AIS, 39–81
client-server computing, 47–48
ethical considerations at, 69–70
interrelationships of business processes, 41–43
processes, 42
resulting reports, 42
transactions, 42
outputs from AIS and business processes, 59–60
Fraud avoidance, policies to assist in the and errors, 96–97
accounting-related fraud, 86–89
categories of, 88
computer fraud, nature of, 93–96
industrial espionage, 93
software piracy, 93
customer fraud, nature of, 92
check fraud, 92
credit card fraud, 92
refund fraud, 92
employee fraud, nature of, 91–92
accounts payable fraud, 91
cash receipts theft, 91
collusion, 91
expense account fraud, 91
inventory theft, 91
kickback, 91
larceny, 91
payroll fraud, 91
skimming, 91
Phar-Mor fraud scheme, 84
vendor fraud, nature of, 93
vendor audits, 93
Fraud triangle, 87
incentive, 87
opportunity, 87
rationalization, 87
Fraudulent financial reporting, 87
Front office modules, 626
G
General authorization, 102
General controls for IT systems, 130–140
AICPA Trust Services Principles, 140–145
antivirus software, 135
authentication of users, 130
authority table, 132
biometric devices, 132
computer log, 132
configuration tables, 133
encryption, 134
firewall, 133
intrusion detection, 136
log in, 131
nonrepudiation, 132
organizational structure, 136–137
password, 131
penetration testing, 136
physical environment and security, 137–139
battery power (UPS), 138
emergency power supply (EPS), 138
generators (EPS), 138
uninterruptible power supply (UPS), 138
public key encryption, 134
secure sockets layer (SSL), 135
security token, 131
service set identifier (SSID), 134
smart card, 131
symmetric encryption, 134
two-factor authentication, 132
user IDs, 131
user profile, 132
virtual private network (VPN), 135
virus, 135
vulnerability assessment, 135
wired equivalency privacy (WEP), 134
wireless protected access (WPA), 134
General journal, 44
General ledger processes, 44, 516–520
risks and controls in, 520–528
special journals, 517
subsidiary ledgers, 518
Generalized audit software (GAS), 276
Generally accepted auditing standards (GAAS), 257
standards of fieldwork, 258
standards of reporting, 258
Generators (EPS), 138
Ghost employee, 456
Global positioning systems (GPSs), 234
cloud computing as a conceptual design, 232
ethical considerations related, 240–242
for consultants, 242
for employees, 241
economic feasibility, 221
operational feasibility, 221
schedule feasibility, 221
technical feasibility, 221
internet commerce, 234
IT governance committee, 215
IT systems match to strategic objectives, 220–221
strategic management, 213
system development life cycle (SDLC), 215–219. See also individual entry
Governance, risk management, and compliance (GRC) activities, 274
Government auditors, 255
Graphical user interface (GUI), 581
H
risks from, 144
Hardware exposures in IT systems, 145–156
Hardware, costs of, 631
Hash totals, 163
Header data, 332
Health Insurance Portability and Accountability Act of 1996 (HIPAA), 605
Hierarchical Database Model, 550
High-impact processes (HIPs), 556
Human resources, 429, 479, 624
I
Incentive, 87
Independent checks and reconciliation, 105–106
cash collection processes, 323
cash disbursement processes, 390
fixed assets processes, 451–452
general ledger processes, 525–526
payroll processes, 439
purchase return process, 381–382
purchasing processes, 374
sales processes, 310
sales return processes, 316
Indexed sequential access method (ISAM), 12
Industrial robots, 491
Information criteria, 115
Information risk and IT-enhanced internal control, 256–257
motive of the preparer, 257
remoteness of information, 256–257
volume and complexity of underlying data, 257
Information Systems Audit and Control Association (ISACA), 109, 213, 259
Information technology (IT). See also Auditing information technology
auditing IT processes, 254
controls, maintenance of, 109–110
of conversion processes, 489–492
of fixed assets processes, 453–455
governance, 211–251. See also Governance, IT
IT auditors, 255
IT governance committee, 136
resources, 115
risk and controls in, 110
availability, 110
confidentiality, 110
online privacy, 110
processing integrity, 110
security, 110
Information technology (IT) enabled business processes, 8–10, 592–596
auditor of AIS, 22
business-to-business (B2B), 594
basic computer data structures, 10–11
bit, 10
byte, 10
database, 10
field, 10
file, 10
master files, 11
record, 10
relational database, 11
transaction file, 11
design or implementation team of AIS, 22
for e-business, 15, 615–647. See also under E-business
electronic data interchange (EDI), 15
electronic invoice presentment and payment (EIPP), 16
enterprise resource planning (ERP), 16–17
E-payables, 16
evaluated receipt settlement (ERS), 16
importance to accountants, 22
IT controls, 20
application controls, 20
general controls, 20
IT governance, 21
point of sale system (POS), 15
supply chain, 592
users of AIS, 22
Information Technology Infrastructure Library (ITIL), 213
Information, 542
Infrastructure as a Service (IaaS), 49, 232
Input controls, 269
Input manipulation, 93
Input methods used in business processes, 54–57
dynamics ERP, 54
electronic data interchange (EDI), 56
point of sale system (POS), 56
Integrated test facility (ITF), 271
Intercompany, 15
Interconnected networks, 581
Internal Auditing Standards Board (IASB), 259
Internal control standards, 113–114
Internal control structure of organizations, 17–21
code of ethics, 20
enterprise risk management (ERM), 18
control activities, 19
event identification, 19
information and communication, 19
internal environment, 18
monitoring, 19
objective setting, 19
risk assessment, 19
risk response, 19
IT controls, 20
application controls, 20
general controls, 20
Internal control system, 4, 83–125, 186–188
corrective controls, 99
detective controls, 99
objectives, 97
preventive controls, 97
reasonable assurance of, 108
Internal controls for IT systems, 156–163
application controls, 129, 156–164
programmed input validation checks, 161–162. See also individual entry
source document controls, 157–160
standard procedures for data input, 160–161
batch totals, 163
control totals, 163
electronic data interchange (EDI), 153
general controls, 129, 130–140. See also individual entry
hash totals, 163
internet, 152
local area network (LAN), 151
processing controls, 163
record counts, 163
run-to-run control totals, 163
telecommuting workers, 152–153
wide area network (WAN), 151
world wide web, 152
Internal documents, 59
function managed, 528
time horizon, 528
Internal reports, 59
Internal Revenue Service (IRS), 85, 566
Internal sources of computer fraud, 93–94. See also under Computer fraud
Internal theft, 87
International Accounting Standards Board (IASB), 185
International Auditing and Assurance Standards Board (IAASB), 258
International Federation of Accountants (IFAC), 258
International Organization for Standardization (ISO), 213, 280
International Standards on Auditing (ISAs), 258
Internet, 13–14, 152, 441, 581. See also Networks
cloud computing, 14
extranet, 14
internal controls for, 599–600
internet commerce, 234
internet EDI, 601
intranet, 13
physical structure of, 582–586
spoofing, 95
voice-over Internet protocol (VoIP), 14
World Wide Web (WWW), 13
Internet service providers (ISPs), 582
local ISPs, 583
regional ISPs, 582
Web server, 583
Interrelationships of business processes and AIS, 41–43
processes, 42
resulting reports, 42
transactions, 42
Interviews, 225
Intranets, 13
internal controls for, 599–600
Inventory control, 479
Inventory status reports, 481
Inventory theft, 91
Investors, 184
J
Just-in-time (JIT) production systems, 492
K
Kickback, 91
L
Labeling interchanges, 332
Larceny, 91
Leaving sales open, 337
Letter of representations, 276
Limit check, 162
Local area networks (LANs), 13, 151, 278
Local ISPs, 583
Location-wise implementation of ERP, 633
Log in, 131
quality control, 484
bill of materials, 477
capital budgeting plans, 477
engineering, 477
operations list, 477
production orders, 479
production schedule, 479
research and development, 477
scheduling, 478
economic order quantities (EOQ), 480
finished goods inventory, 480
human resources, 479
inventory control, 479
inventory status reports, 481
maintenance and control, 479
raw materials, 480
routing, 480
routing slip, 480
warehousing, 481
work-in-process inventory, 480
Loss of audit trail visibility, 257
M
Magnetic ink character recognition (MICR), 233
Magnetic tape, 545
Management assertions, 259–261
Management oevrride, 90
Management oversight, 196
Manufacturing resource planning (MRP II), 491, 619
Manufacturing resource planning (MRP), 617
Many-to-many relationships, 548
Market segments of ERP systems, 625–628
Oracle, 626
Peoplesoft, 626
SAP, 626
Master files, 11
Matching
invoiceless system, 395
Materiality, 261
Materials requirements planning (MRP), 619
Materials resource planning (MRP), 491
Mathematical accuracy tests, 270
Microsoft Dynamics GP®
bill of materials preparation, 478
credit limit, 308
general ledger posting, 524
list price of inventory items, 307
payments, 388
payroll register preparation, 435
purchase orders in, 371
purchase receipts in, 372
purchase returns in, 380
transaction modules, 520
Misappropriation of assets, 87
Misstatement of financial records, 87
Modular implementation of ERP, 634
Monus, Michael, 402
Multidimensional analytical processing (MOLAP), 557
N
National Science Foundation (NSF), 581
Networks, 13–14, 582–583. See also Internet
database model, 551
local area network (LAN), 13
risks from, 144
Nonrepudiation, 132
Normalized data
data warehouse, 554
data normalization, 553
primary key, 551
structured query language (SQL), 552
operational database, 554
rules of, 553
O
Observation, 224
Off-site backup, 140
One-to-many relationships, 548
One-to-one relationships, 548
Online analytical processing (OLAP), 557–559
consolidation, 558
drill down, 558
exception reports, 558
pivoting, 558
time series analysis, 558
what-if simulations, 559
Online privacy, 110
Operation and maintenance, 217
availability, 636
confidentiality, 636
online privacy, 636
processing integrity, 636
security, 636
Operational audits, 255
Operational database, 12, 554, 618
Operational feasibility, 231
Operations personnel, 137
Opportunity, 87
Oracle, 626
Organization
chart, 429
IT governance importance in, 238–240
SDLC as an internal control, 239–240
SDLC as part of strategic management, 239
Organizational structure and general controls for IT systems, 136–137
database administrator, 137
operations personnel, 137
programmers, 137
system development life cycle (SDLC), 137
systems analysts, 137
audit trail tests, 273
reasonableness tests, 273
reconciliation, 273
rounding errors tests, 273
Output manipulation, 93
Outputs from the AIS and business processes, 59–60
external reports, 59
internal documents, 59
internal reports, 59
trading partner documents, 59
P
Packet switching, 580
Parallel conversion, 237
Parallel simulation, 272
Password, 131
Paymaster, 438
Payroll fraud, 9I
Payroll outsourcing, 441
Payroll processes, 427, 429–437
corporate governance in, 457–459
ethical issues related to, 455–457
human resources department, 429
organization chart, 429
payroll disbursements journal, 436
payroll register, 435
risks and controls in, 437–440
time sheet, 434
Payroll register, 435
Payroll system flowchart, 63
Peoplesoft, 626
Periodic inventory systems, 486
Perpetual inventory systems, 485
Phase-in conversion, 237
Physical access risks, 145
Physical environment and security, 137–139
Physical inventory count, 488
Physical inventory reconciliation, 488
Pick list, 307
Pigeon, Paul, 402
Pilot conversion, 237
Pivoting, 558
Planning phase, 261
Platform as a Service (PaaS), 49, 232
Point of sale (POS) systems, 15, 56, 300, 327, 335–336
Post-implementation review, 238
Preventive controls, 97
Price list, 303
Primary key, 551
Privacy expectations in e-commerce, 590–592. See also under E-Commerce
Privacy, 110
Problems, this book
administrative processes/controls, 537–538
auditing IT-based processes, 293–294
conversion processes/controls, 501–502
data and databases, 573
e-business and e-commerce, 611–612
expenditure processes/controls, 411–415
fraud, ethics, and internal control, 119–121
internal controls/risks in IT systems, 172–173
payroll and fixed asset processes/controls, 465–466
revenue and cash collection processes/controls, 346–352
symbols, 61
Processing accounting data, 57–59. See also Batch processing; Online processing; Real-time processing
Processing controls, 163, 269–273
balancing tests, 270
Benford's Law, 271
computer assisted audit techniques (CAATs), 271
embedded audit modules, 272
integrated test facility (ITF), 271
mathematical accuracy tests, 270
parallel simulation, 272
program mapping, 271
program tracing, 271
run-to-run totals, 270
test data method, 271
Processing integrity risks, 142–145, 148
Processing integrity, 110, 155, 334
Procurement and logistics, 624
Procurement cards, 401
Production orders, 479
Production schedule, 479
Program manipulation, 93
Program mapping, 271
Program tracing, 271
Programmed input validation checks, 161–162
completeness check, 162
field check, 161
limit check, 162
range check, 162
reasonableness check, 162
self-checking digit, 162
sequence check ensures, 162
sign check, 162
validity check, 161
Programmers, 137
Protocol, 580
Public cloud computing, 154
Public Company Accounting Oversight Board (PCAOB), 113, 191, 258
Public key encryption, 134
Purchase requisition, 367
Purchase return process, 376–380
risks and controls in, 381–383
Purchases journal, 370
bill of lading, 371
blind purchase order, 371
cutoff, 372
packing slip, 371
purchase order (PO), 367
purchase requisition, 367
purchases journal, 370
receiving report, 371
risks and controls in, 373–376
Q
Quality control, 484
Questionnaires, 225
R
Radio-frequency identification (RFID) systems, 492
Random access files, 11
Random access, 545
Range check, 162
Rationalization, 87
Raw materials, 480
Real-time processing, 12, 58–59, 546
Reasonable assurance, 105, 108
Reasonableness check, 162
Reasonableness tests, 273
Receiving log, 313
Reconciliation, 105–106, 273. See also Independent checks and reconciliation
Record counts, 163
Record pointer, 550
Records and documents, 309–310
Redundant array of inexpensive disks (RAID), 331
Redundant arrays of independent disks (RAIDs), 139
Redundant servers, 139
Refund fraud, 92
Regional ISPs, 582
Regulators, 184
Relational database management systems (RDBMS), 631
Relational online analytical processing (ROLAP), 557
Remoteness of information, 256–257
Reporting as general ledger processes output, 526–528
external reporting, 527
Request for proposal (RFP), 227
Resources events agents (REA) in AIS, 72–73
Revenue processes, 300–303. See also Cash collection processes; Sales processes
corporate governance in, 339
channel stuffing, 337
leaving sales open, 337
IT-enabled systems of, 325–328
within the overall system, 301
Rework, 485
Risks, 262
assessment, 101
automated matching, 15–16, 393
availability, 142–143, 145, 279, 331
business continuity, 145
cash disbursement process, 388–391
cash receipts process, 91
categories, 110
confidentiality, 110, 140, 143–145, 329, 394–395
defined, 262
e-business (expenditures), 398–400
from environmental factors, 144
evaluated receipt settlement, 397–398
general ledger process, 520–526
from hacking/network break-ins, 144
from network break-ins, 144
in not limiting unauthorized users, 141–143
operating system, 148
physical access, 145
processing integrity, 110, 140, 143–145, 148, 155, 329–330, 334, 395, 397, 399, 636
purchase return process, 381–383
security, 141, 144–145, 148, 279
Rounding errors tests, 273
Router, 580
Routing, 480
Routing slip, 480
Run-to-run control totals, 163
Run-to-run totals, 270
S
Salami technique, 94
Sales allowance, 318
Sales invoice, 307
Sales journal, 308
Sales order, 303
bill of lading, 307
credit limit, 303
document flowchart, 305
packing slip, 307
pick list, 307
price list, 303
purchase order, 303
risks and controls in, 308–313
sales invoice, 307
sales journal, 308
sales order, 303
sales process map, 304
Sales return processes, 302, 313
credit memorandum, 313
receiving log, 313
receiving report, 313
risks and controls in, 313–318
Sampling, 281
Sarbanes–Oxley Act of 2002, 96, 113, 190–195, 283. See also Corporate governance
conflicting abilities, 637
impact on on corporate governance, 196–199
ethical conduct, 198
financial stewardship, 198
internal controls and compliance, 196–197
management oversight, 196
key provisions of, 192
Section 201 (Services outside the scope of practice of auditors), 192–193
Section 301 (Public company audit committees), 193
Section 302 (Corporate responsibility for financial reports), 193–194
Section 401 (Disclosures in periodic reports), 194
Section 404 (Management assessment of internal controls), 194–195
Section 406 (Code of ethics for senior financial officers), 195
Section 409 (Real-time disclosures), 195
Section 802 (Criminal penalties for altering documents), 195
Section 806 (Protection for employees of publicly traded companies who provide evidence of fraud), 195
Section 906 (Failure of corporate officers to certify financial reports), 194
Section 1102 (Tampering with a record or otherwise impeding an official proceeding), 195
Scalability, 154
Scalable ERP system, 634
Schedule feasibility, 231
Scheduling, 478
Screen scrapers, 46
SDLC as an internal control, 239–240
Secure socket layers (SSL), 135, 144, 586
Securities Act of 1933, 190
Securities and Exchange Commission (SEC), 85, 184
Securities Exchange Act of 1934, 190
Security of assets and documents
cash collection processes, 323
cash disbursement processes, 389
fixed assets processes, 451
payroll processes, 438
purchase return process, 381
purchasing processes, 374
sales processes, 310
sales return processes, 316
Security risks, 141–142, 144–145, 148, 278, 330–331
Security token, 131
Segregation of duties, 103, 309
cash collection processes, 322–323
cash disbursement processes, 389
fixed assets processes, 451
general ledger processes, 522–524
purchase return process, 381
sales processes, 309
sales return processes, 315
Self-checking digit, 162
Sequence check ensures, 162
Sequential access files, 11, 545
Service level agreement (SLA), 49, 232
Service Organization Controls (SOC) Framework, 280
Service set identifier (SSID), 134, 144
Shareholders, 183
Sign check, 162
Skimming, 91
Small to medium-size enterprise (SME), 562
Smart card, 131
Software as a Service (SaaS), 49, 232
Software exposures in IT systems, 145–156
Software piracy, 93
Software programming, 236
Software selection, 218
Software testing, 236
Software, costs of, 631
Source document controls, 158–160
form authorization and control, 158
form design, 158
retention of source documents, 158–160
Source document, 43
Source of capital processes, 513
Specific authorization, 102
e-mail spoofing, 95
internet spoofing, 95
Stakeholders, 181
Standard costs, 485
Station set identifiers (SSID), 152
Storage of data terminology, 544
Strategic management, 213
Structured data, 543
Structured query language (SQL), 552
Substantive testing, 274
Suppliers, 184
Supply chain management (SCM), 7–8, 621, 624–625
business process linkage throughout, 6–8
Symmetric encryption, 134
System conversion, 237
System development life cycle (SDLC), 137, 215–219
conceptual design, 218
detailed design, 219
evaluation and selection, 218
operation and maintenance phase of, 238
operation and maintenance, 217
as part of strategic management, 239
phases of, 219
post-implementation review, 238
software selection, 218
systems analysis phase of, 222–226
interviews, 225
preliminary investigation, 222–223
questionnaires, 225
user requirements, determination, 224–225
systems analysis, 217
systems design phase of, 226–234
conceptual design, 229
systems design, 217
systems implementation phase of, 235–238
direct cutover conversion, 237
documenting the system, 236
parallel conversion, 237
phase-in conversion, 237
pilot conversion, 237
software programming, 236
software testing, 236
system conversion, 237
training employees, 236
systems implementation, 217
systems planning, 217
systems planning phase of, 219–222
payroll system flowchart, 63
symbols, 63
System survey analysis, 225–226
business process reengineering (BPR), 225
systems analysis report, 226
Systems design, 217
Systems development life cycle (SDLC) model, 632
Systems implementation, 217
Systems planning, 217
Systems survey, 223
Systems, Applications and Products (SAP) in data processing, 620
T
Technical feasibility, 230–231
Telecommuting workers, 152–153
Test data method, 271
application controls, 269–274. See also individual entry
authenticity tests, 268
penetration tests, 268
review access, 268
vulnerability assessments, 268
Three way match, 391
Throughput, 223
Tier one, 625
tier one software, 625
Time series analysis, 558
Time sheet, 434
Tone at the top, 181
Totals
hash, 163
Trade-offs in database storage, 554
Trading partner documents, 59
Traditional EDI, 602
Trailer data, 332
Training employees, 236
Transaction authorization
cash collection process, 322
cash disbursement process, 388–389
conversion process, 486
general ledger process, 520–522
payroll process, 437
purchasing process, 373
purchase return process, 381
sales process, 309
sales return process, 313
Transaction file, 11
Transaction logging, 335
Transaction processing systems (TPS), 302, 364
Transparency, 187
Trap door alteration, 94
Treadway Commission, 184
Trojan horse program, 94
Trust Services Principles. See AICPA Trust Services Principles
Turnaround document, 44
Two-factor authentication, 132
enterprise application integration (EAI), 46
general journal, 44
general ledger, 44
modern, integrated systems, 47
screen scrapers, 46
source document, 43
special journals, 44
subsidiary ledgers, 44
turnaround document, 44
U
Underwriter, 514
Unethical management behavior in capital sources and investing, 529–530
Uniform resource locater (URL), 584
Uninterruptible power supply (UPS), 138
UNIX® computer, 580
Unstructured data, 543
User IDs, 131
Users of AIS, 22
V
Value added networks (VANs), 332, 601
Variances, 486
Vendor audits, 93
Vendor fraud, nature of, 93
Virtual private network (VPN), 135, 144
Virus, 135
Voice-over Internet protocol (VoIP), 14
Vulnerability assessment, 135
Vulnerability testing, 398
W
Warehousing, 481
Web-based sale system, 330
Web server, 583
What-if simulations, 559
Whistleblower, 195
Wide area network (WAN), 151, 278
Wired equivalency privacy (WEP), 134, 144, 152
Wireless protected access (WPA), 134, 144, 152
Work-in-process inventory, 480
Y
Y2K compatibility, 620
Z
Zikmund, Paul, 92
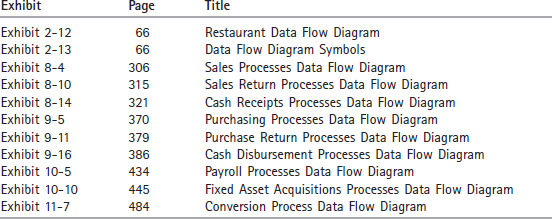
SYSTEM AND DOCUMENT FLOWCHART SYMBOLS
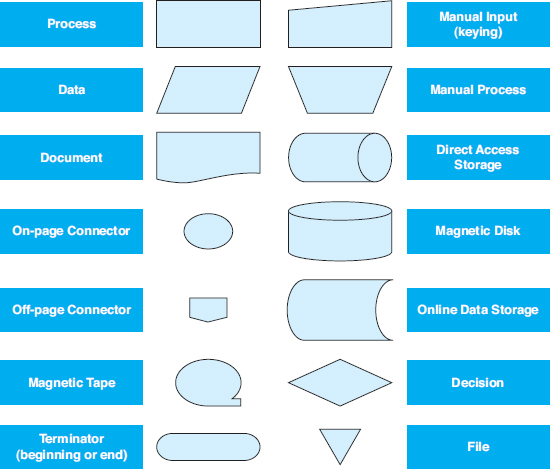
PROCESS MAP SYMBOLS
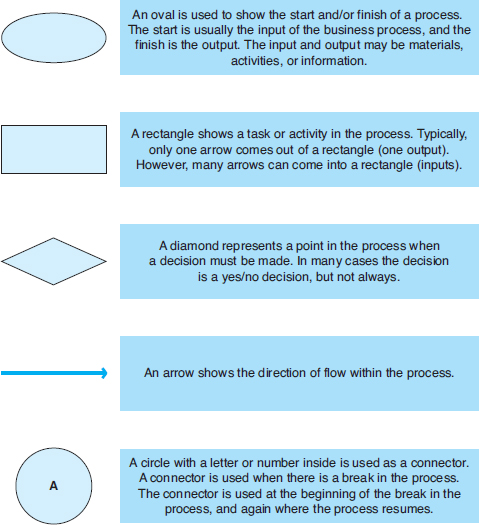
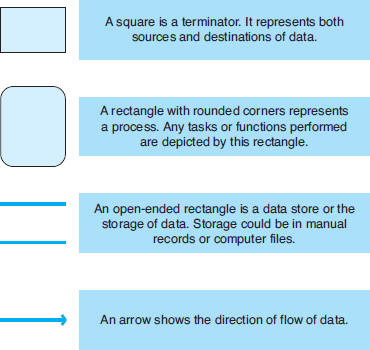
DATA FLOW DIAGRAM SYMBOLS
A LIST OF FLOWCHARTS IN THIS TEXTBOOK
A LIST OF PROCESS MAPS IN THIS TEXTBOOK
A LIST OF DATA FLOW DIAGRAMS IN THIS TEXTBOOK