The security system will be divided into five main parts: the Arduino sensor nodes, the RF network that connects each node to the Raspberry Pi, the MQTT broker that connects the RF network to the web application, the web application that manages the senor events and alerts, and the database that stores the configuration of the sensors and alarms and the history of each sensor.
Each sensor node is comprised of an RF module that allows communication between the network of sensor nodes and several security sensors, such as PIR motion detectors and reed switch doors or window sensors, and both the standard sensors used on the standard home security systems. While these nodes can be battery powered for better reliability, we will power ours by using a USB port and USB power supply.
The Raspberry Pi will serve as both the host server for the web application and database and the base node in the RF network. This will use the same RF modules and software libraries as the Arduino sensor nodes.
Our security system will not use a bell or sounder, such as a conventional security system; instead, it will send e-mail alerts to an address configured via the web interface. It will also allow alarms to be configured much more freely than a conventional system, allowing you to set several alarms for each different area in a house. It will also allow the alarms to act independent of each other.
For the rest of the chapter, we will assume that the security system has three sensor nodes; here, all three have magnetic door sensors and only two out of three have PIR motion sensors.
At this stage, you need to think about where each node will be located, as the RF modules can only transmit over a certain distance before the signal either becomes too weak to ensure reliable communication or is lost completely. From my own testing, I have found that the link between two nodes can rarely travel more than one wall or floor.
Therefore, in order to have a longer distance between the base node and sensor node, the sensor node must communicate through a node that acts as a repeater. This is handled by the network protocol library used on the sensor's nodes and the Pi. We will look at this in more detail later in this chapter, but for now, provisioning at least one sensor node in each room you want to have a sensor in as well as any room between nodes will be sufficient.
The following diagram roughly shows the structure of the system we will use for the rest of the chapter:
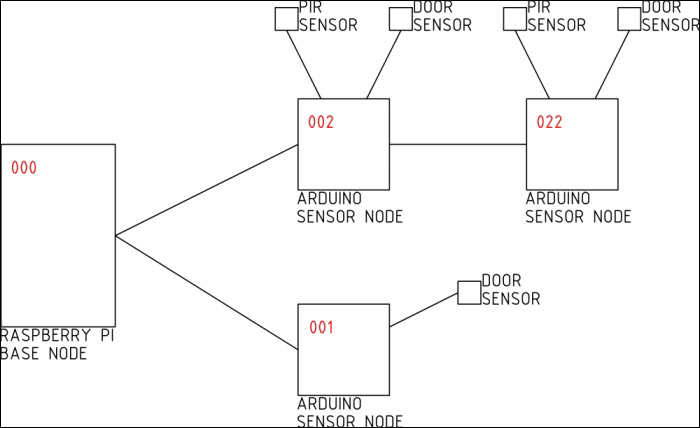
If you are using your own system design, then it helps to make your own diagram similar to this. Make sure to note the sensor node address, location, and MQTT topic of each sensor to help make the programming of each of these sensor nodes and the addition of the sensors to the web application easier.
