CHAPTER 30
Healthcare Cybersecurity Technology
Mac McMillan
In this chapter, you will learn how to
• Define why healthcare is a target of cybercriminals
• Identify the threat and developing threat information resources
• Describe the importance of planning and using frameworks to help plan outcomes
• Develop cybersecurity readiness and technologies that support security
• Develop tests of your cybersecurity readiness and vulnerability
Healthcare Cybersecurity Threat
Arguably, cybersecurity became the number one information technology concern for healthcare organizations in 2015. By early 2016, there was no doubt that it was a top priority, if not the top priority. Many in the IT industry and media referred to 2015 as the year of the hack, but in the healthcare IT segment, we witnessed healthcare mature into a full-fledged battleground with cybercriminals, hackers, hacktivists, and state-sponsored attackers all becoming prominent in 2015 and 2016. For everyone in healthcare, the cybersecurity threat was finally real and inescapable, progressing from theft of data to hacking to attacks that are disruptive. This, however, should not have been a surprise to anyone involved in security, as all the conditions necessary to make healthcare the target it had become began to align as early as 2006 and took a significant leap forward in 2009 with the Health Information Technology for Economic and Clinical Health (HITECH) Act1 that established incentives for “meaningful use” of electronic health records (EHRs) and started healthcare on the path toward increased automation and the wholesale digitization of patient information.
Over the next few years after HITECH became law, healthcare rapidly adopted EHRs and reinvented how hospitals and doctors cared for their patients, managed the enterprise, collected revenue, and measured quality. The application and data became the epicenter of how all things got done in healthcare. The expansion of the healthcare network through a growing supply chain, cloud and software service providers, increased partners, and patient-centric initiatives like telehealth and population health added to the complexity of the enterprise and increased its risks. Healthcare had what cybercriminals wanted and had now made it possible for them to get at it. Understanding the technology implications of the healthcare security ecosystem today requires an appreciation of how the threat has evolved and how it is affecting our environment. Figure 30-1 depicts through several prominent examples how the threat has evolved between 2009 and 2016.

Figure 30-1 The evolution of threats between 2009 and 2016. Numbers represent records and individuals affected.
When the HIPAA Security Rule went into effect in 2005, much of the automation that is available today did not exist yet, patient records were still for the most part in paper form, there were no smartphones or tablets, medical devices were not yet networked, and things like accountable-care organizations (ACOs), health information exchanges (HIEs), cloud services, population health, and the Internet of Things (IoT) were not yet a reality. That all began to change shortly thereafter as one innovation after another in either healthcare or information technology added an additional layer of complexity to the computing environment and, with it, increased risk of cybersecurity events. In 2009, HITECH all but ensured that healthcare would never again see a simple information security environment. The threat, as Figure 30-1 shows, evolved and escalated in sophistication, form, and impact. Today, healthcare confronts the same threats that any other industry sector confronts and is the number one target of cybercriminals because of the amount, type, and value of information it holds that they can monetize easily on the dark web (aka darknet). The cybersecurity threat today comes in many forms, and it attacks weaknesses in technology, organizational processes, and people. As an example of how threatening the cyberattackers can be, in late June of 2016, a cyber extortionist going by the name of “thedarkoverlord” offered for sale on the dark web 655,000 medical records and included an ominous threat: “Next time an adversary comes to you and offers you an opportunity to cover this up and make it go away for a small fee to prevent the leak, take the offer. There is a lot more to come.” Days later the hacker posted for sale an additional 9.3 million records, seeking almost $500,000 worth of bitcoins in exchange.
In the 1990s, when the HIPAA security rules were first contemplated, the Nationwide Health Information Network (NwHIN) was just an idea, EHRs only existed in some hospitals and large practices that had a hospital information system (HIS), and HIEs (as we know them today) and ACOs, creating large networks of connected providers, payers, physicians, and vendors, did not exist. For many organizations, very few systems reached outside the four walls of the institution, and the number of users who had access to patient information was far fewer than today. In 2017, we have enterprises that involve tens of thousands of systems, thousands of applications, huge data repositories, and even more users with access than systems. Add to that the number of third-party service providers, business associates (BAs), that the average provider deals with and the numbers soar. That is the ecosystem that healthcare IT leaders find themselves confronted with today. That ecosystem is characterized by ever-evolving technologies, clinical and decision support systems, a rapid proliferation of networked and mobile devices, remote services, telemedicine to bring healthcare closer to the rural or distant patient, and home health initiatives to bring healthcare to the patient where he or she lives. The delivery of healthcare is not just in the hospital or clinic anymore, it is everywhere, and demands a ubiquitous information presence that can keep up and support it. Patient information is rapidly being digitized in larger and larger amounts and being replicated and disseminated across this ecosystem very broadly, making the information more accessible in more ways, on more devices, and to more people, and introducing more ways that the threat can compromise or exploit it.
The point is that just as healthcare IT is dynamically evolving, so are the cyber threats around it, and those involved in owning a healthcare business, delivering IT services to healthcare, or engaged in information security need to be comfortable with adapting to and managing change. Health organizations that are likely to succeed more often in meeting the threat will have three things in common:
• They will learn their adversary and understand their risk posture.
• They will develop a dynamic plan of action that focuses their cybersecurity efforts.
• They will learn to execute at a high level of precision.
The battle with cybercriminals will not be won by those who sit on the sidelines waiting for a solution to come to them.
Think Like a Bad Guy
When assessing threats, it is always useful to identify what you have that a particular threat might want, which then enables you to recognize those threats that are of reasonable concern. It is also necessary to be objective when considering your state of security and areas of vulnerability. Often, the best way to do this is to ask someone else to evaluate your security posture for you. Another important thing to understand is the general nature of the threat, both directly and indirectly. The Ponemon Institute has conducted independent research into the cost of data breaches for many years now. Consistently, the Ponemon researchers have found that regulated industries such as healthcare pay more for breaches, that the overwhelming majority of breaches are caused by criminals, and that the longer it takes for an organization to detect and react to a breach the more it will cost them.2 Indiscriminate threats account for a large number of network outages and lost data. Most malware attacks today are indiscriminate attacks seeking any network connected to the Internet that is not protected properly. There are also bad actors that target healthcare and patient information both from within and without the hospital. In fact, today the number of incidents perpetrated by insiders still far exceeds the number perpetrated by outsiders, and the number of incidents caused by carelessness or mishandling of systems and information far exceeds the number caused by sophisticated hacks. Therefore, it is important to understand your security weaknesses and those threats that can take advantage of those opportunities to exploit your systems and information. Many external attacks first start with an attack that targets an insider, like phishing attempts, water-cooler attacks, and so forth. These are forms of social engineering, and to understand social engineering, it is helpful to understand the con artist. Two famous con artists are Frank Abagnale, Jr. and Kevin Mitnick. You can find books by both of these individuals, and Frank’s autobiography during his crime years, aptly titled Catch Me If You Can, was also turned into a movie.3 Neither one of these individuals was a hacker, but what is important here is understanding the mindset of the attacker.
There is plenty of motivation for individuals who would commit theft, fraud, or a crime to target healthcare. Healthcare has a tremendous amount of valuable information. More so than any other industry, healthcare collects, retains, processes, transmits, and shares very personal and very valuable information belonging to patients. This includes personally identifiable information, health information, and financial information. At the time of writing, the average price of credit card details on the black market is $1 a number, the average price for a Social Security number is between $1 and $3, while the average price for a medical identity is $50. Healthcare entities collect and store all three of these. Prior to 2000, it was harder to steal this information because many healthcare organizations were still very paper process dominated, but that is not the case anymore. Not only is more of this information digitized, but also there are more systems, greater connectivity, and more people accessing it, all of which introduce new types of threats and attract persistent threats. When famous criminal Jesse James was asked why he robbed banks, he reputedly answered “that’s where the money is.” The same is true for cybercriminals. They go where they can steal the most data, and that is healthcare organizations.
The Big Four: Cybercrime, Cyber Espionage, Hacktivism, and Advanced Persistent Threats
Cybercrime, cyber espionage, hacktivisim, and advanced persistent threats (APTs) are the “four horsemen of the apocalypse” because they are coming, they keep coming, and they are relentless, persistent, and able to constantly reinvent themselves. As soon as we find a way to block them from our networks, or at least make it harder for them to get in, they find a new way. The battle with these four is also an asymmetric contest where the organizations must find and close every vulnerability in their networks and systems and the attackers need only find the one they missed, and the threat only requires periodic victories. For hackers, trial and error is not only part of the experience, it is expected, and with each failure or win, they learn something new. For organizations whose mission it is to protect against these threats, any security breach is failure. Therefore, the first thing that those who engage in cybersecurity need to know is that abnormal is normal. The second thing to know is that the threat is trying to get in continuously, 24 hours a day, 365 days a year. The third thing to know is that you will not be successful 100 percent of the time in keeping the threat out, which is why increasing cybersecurity readiness both inside and out, enhancing detection capabilities, and having solid incident response are imperative.
Cybercriminals come in many forms, from malicious insiders, to information thieves, to identity thieves, to extortionists. Extortion, most often in the form of ransomware, is especially troubling for healthcare organizations because it attacks data availability, which affects the very thing they care most about—patient care. Ransomware itself now has many different forms, from types that attack and lock up systems, to types that attack and encrypt data, to types that attack/steal the information and leave behind an encrypted copy. Extortion can take a more sinister approach when the hacker steals data and then demands a ransom to return the data, typically along with an explanation of how to fix the vulnerability and a promise not to disclose the issue. The problem with responding to extortion is that you are dealing with a criminal. You do not know if the extortionist will return all the data or keep a copy and continue the extortion, has left a back door into your environment to steal more data, or will keep the promise not to disclose the issue.
Cyber espionage is a targeted form of cybercrime. The attacker is after information for the value of the information itself—the intelligence, commercial advantage, and so forth that can be gleaned from it. The attacker could be a hacker looking for intellectual property to sell to the highest bidder, a state actor seeking strategic intelligence, or a rival corporation looking for competitive advantage. Espionage can signal massive breaches, as the attackers are after all the information they can get. These are usually more sophisticated attacks as well, and the hacker may run a ransomware or denial-of-service attack as they leave in order to throw off the investigation.
Hacktivisim is usually cause-based, or an attack based on ideology. For example, an attacker may be unhappy with some position the healthcare system has taken regarding delivery of services or some environmental impact the business is causing. Hacktivists want to make a point. They are usually not interested in stealing information or hurting anyone, but their attacks are no less serious as some have learned the hard way (e.g., Boston Children’s Hospital4 and Hurley Medical Center5).
Finally, advance persistent threats, attacks against the enterprise where the attacker gains unauthorized access and is able to remain undetected for a very long time, are the last of the four horsemen. These attacks generally target the theft of information, not the disruption or destruction of the network. These attacks are typically carried out by more sophisticated attackers such as state-sponsored groups, but they could also be organized criminals looking to exploit financial systems or steal personal information and intellectual property. In many of the large breaches discovered in 2015/16, the attackers were in the target network for more than 200 days prior to discovery. Many of the largest breaches in healthcare were the result of APTs.
The four horsemen are not the only threats that healthcare needs to be aware of. Malware represents another very large concern. Just the sheer volume of malware we see now annually, as discussed previously, and the hackers’ use of malware to deliver ransomware and other malicious payloads, make this last category an ongoing concern. Thankfully, there are multiple technologies that can help mitigate these threats, as we will discuss in the next section.
Cyber attacks, like other criminal activity, tend to follow the path of least resistance or the simplest means of attack. The attacker will almost always try to find the easiest means to breach the network or system. In many cases, the attacker is able to find a vulnerability or trick someone into providing information that will enable the attacker to gain access without having to resort to a complicated technical attack. Sometimes the attacker is a form of automated malware that does not discriminate with respect to who it attacks. The number of malware attacks has grown exponentially in the past 20 years such that, at the time of this writing, leading threat research centers estimate that there were 430 million unique new pieces of malware in 2015, equating to more than 100,000 new attacks daily, and more than 700,000,000 known forms of malware.6 Even more challenging are “zero day” attacks, malware that takes advantage of a software vulnerability that the vendor is unaware of and for which there is no immediate fix. In 2015 there were 54 zero-day attacks or roughly one per week.

NOTE In previous years, reports focused on exploited zero-day vulnerabilities, and now they focus on the total number of vulnerabilities that could potentially be exploited. The new definition demonstrates potential risk more accurately, while the other spoke to actual historical risk. In 2014, the number of vulnerabilities was 4,958, in 2015 it was 4,066, and in 2016 it was 3,986.7
Many recent malware variants are very sophisticated, capable of morphing their appearance, disabling antivirus systems and other security controls, communicating remotely and transmitting data, and masking themselves to make it more difficult to detect and eradicate them quickly. Malware comes in many different forms and is delivered via multiple mechanisms. The volumes are so high that many traditional methods of protection such as anti-virus systems that rely primarily on signature-based rules have become less effective. Today organizations must apply newer technologies that take advantage of heuristic capabilities to recognize potential malware threats. Advanced malware solutions now can detect anomalous patterns in behavior and flag threats before they traverse the perimeter.
If malware were the only threat that healthcare entities had to deal with, the task would be difficult enough, but even as big a threat as malware represents, it is not the most serious risk. In fact, loss of data, compromises, or network outages due to malware account for less than 15 percent of the total threat. The largest losses of data suffered have traditionally been through the physical loss or theft of computer devices, malicious acts or unintentional mistakes by insiders, and actions of third-party business partners. There are literally millions of discrete access events a year that must be monitored and evaluated. A single patient visit lasting a day for a simple procedure can generate more than 150 access events. A longer stay in a hospital for a more serious reason can generate thousands of access events. Taken over the course of a day, a week, a month and the entire universe of patient encounters will generate literally millions of access events. Things as seemingly simple as accounting for disclosures—who has seen a patient’s record—can become a major task. Simple policies, procedures, and manual processes are not adequate to protect either today’s healthcare IT environment or tomorrow’s.
Staying Abreast of the Threat
Computer information security officers (CISOs) need to develop an effective system for gathering relevant threat information to inform their decisions and programs. There are many sources for threat information, such as the National Health Information Sharing and Analysis Center (NH-ISAC; https://nhisac.org/), InfraGard (https://www.infragard.org/), a partnership between the FBI and private sector, and the U.S. Computer Emergency Readiness Team (US-CERT; https://www.us-cert.gov/). In late 2015, Congress passed the Cybersecurity Information Sharing Act (CISA)8 with the intent to establish a clearinghouse and methods of dissemination for threat information in healthcare. Some regional alliances have formed as well where member entities share threat information with one another. However, to be truly useful to a future threat, accurate information needs to be shared in a timely fashion between systems. As processing speeds increase and threats become more sophisticated, aggressive CISOs will need to turn to technology to enable real-time threat information sharing in order to support timely reaction and action. In 2025, simple personal computer speeds are predicted to be 1016 cycles per second (10,000 trillion cycles per second) or the equivalent processing speed of the human brain.9 Larger, more sophisticated platforms and big data will be moving even faster. Security technology of the future will require timely threat intelligence in order to successfully protect the enterprise. The US-CERT in concert with the Department of Homeland Security (DHS) is working to automate the sharing of threat information through the use of several integrated technical specifications. Three of these specifications are
• Trusted Automated eXchange of Indicator Information (TAXII)
• Structured Threat Information eXpression (STIX)
• Cyber Observable eXpression (CybOX)
Together, these specifications provide common standards and languages to describe types of information exchanges, cyber threats, and observable cyber events.10
Training and education are also important for anyone engaged in cybersecurity due to its dynamic and evolving nature. What we know today will not carry us very far into the future. Seek out courses in advanced techniques of defense as well as threat information. There are many different credible sources for this type of training such as SANS, ISACA (previously known as the Information Systems Audit and Control Association), and CompTIA (Computing Technology Industry Association). All of these organizations offer multiple certifications in various security disciplines and functional areas. These organizations and others, like Black Hat, also provide forums to present and discuss threat information. Black Hat is one of the largest threat conferences hosting both hackers and security professionals who share information, know-how, and techniques regarding the latest security threats facing industries. Since 2012, healthcare has been the focus of part of its agenda. Healthcare cybersecurity professionals can glean useful information about the threats they face by attending these types of events.
Systems and cybersecurity professionals are not the only ones who will need better education and awareness. Workforce members will as well. The antiquated practices of the past that relied heavily on briefings and canned computer-based training (CBT) modules will need to be augmented by more advanced techniques using experiential approaches. Providing training to workforce members about phishing is a good example of this. Traditional methods do not work, because users do not internalize the information such that it becomes a habit (changes behavior), nor do they keep up to date on ways to recognize the latest phishing techniques. Phishing exercises repeated on a regular basis that simulate a real phishing message that the user receives in his or her e-mail stream, followed by immediate training if they open it, have proven to reduce significantly the number of repeat offenders. “With repetition, a sustained and well-executed phishing simulation program provides a significant reduction in overall exposure to risk from this ever-changing attack vector and improves the security posture of an organization.”11 Real-time and table-top exercises for workforce members provide the hands-on simulations that enhance the training experience and engage cognitive problem solving. Essentially, we learn better by doing.
Planning for Outcomes: Cybersecurity Frameworks and Standards
A systemic approach to cybersecurity management must begin with a clear understanding of the “big picture,” which means understanding the assets to be protected, the stakeholders, and the impact to the organization given the realization of a threat. The best way to create this understanding is by using frameworks and standards to identify the controls and technology necessary to implement that vision.
The Healthcare Insurance Portability and Accountability Act (HIPAA) provides comprehensive guidance and a legally binding framework for protections applied to patient health information to assure privacy and security. However, HIPAA lacks the overall approach and the necessary guidance to marry cybersecurity to business goals, is silent on many of the current practical realities affecting cybersecurity today, and is considered far too ambiguous on many aspects of cybersecurity to be really useful for designing an effective control environment. HIPAA’s one-size-fits-all design provides a basic set of recommendations that are very helpful and act as a roadmap for small organizations, but fall short when it comes to the advanced challenges of cybersecurity.12 For those reasons, while HIPAA provides a meaningful guide for privacy and security considerations affecting patient health information, it is not considered an acceptable standard or framework to build an effective cybersecurity program. As a result, and in response to the growing cybersecurity threat, healthcare is embracing more mature security frameworks to protect their systems and data.
There are far too many frameworks and standards to discuss in this chapter, but the one most prevalent in healthcare today is the National Institute of Standards and Technology Cybersecurity Framework for Healthcare (NIST CSF). NIST as a government organization has as its primary purpose researching, developing, and publishing guidance for the protection of information technology and data. The NIST Framework for Improving Critical Infrastructure Cybersecurity is a set of industry standards and best practices to help organizations manage cybersecurity risks. The Department of Health and Human Services (HHS) in conjunction with NIST has released a useful crosswalk between the NIST CSF for healthcare and the HIPAA Security Rule. The crosswalk provides “mappings” between the many very specific requirements listed in the NIST CSF and the specifications listed in HIPAA. The NIST CSF is the result of a February 2013 Executive Order titled “Improving Critical Infrastructure Cybersecurity” and 10 months of collaborative discussions with more than 3,000 security professionals.13
Using frameworks for guiding program development and execution offers multiple benefits beyond simply improving our cybersecurity posture. Frameworks afford an opportunity to establish both a target state as well as a prioritization of action with respect to remediation to achieve that target state. It provides reference for discussions both internally and externally around program status, direction, budget, compliance, etc. as well as common road map for continuously mapping and reassessing the program and cybersecurity posture. More importantly it provides a plan that keeps the program focused and creates a structure that allows flexibility to make adjustments when new requirements or changes come along that need to be accommodated. Last, but not least, it promotes compliance, but in a more meaningful way, as a result of sound security. The NIST CSF was the basis for the HIPAA Security Rule and Office of Civil Rights (OCR) “Guidance on Risk Analysis Requirements under the HIPAA Security Rule” and is used across the federal government, including by both the Centers for Medicare and Medicaid Services (CMS) and the HHS Office of the Inspector General (OIG). It is also used by the national research community and by more than 60 percent of healthcare organizations, and is used as part of the Malcolm Baldrige National Quality Award criteria. Whether for meeting a regulatory requirement, meeting program mandates, seeking recognition, or just communicating security readiness to peer organizations, NIST CSF provides a common language and standard for those activities.
Building a Secure Architecture
When building the security architecture, you should think in terms of layers (from the core to the endpoint and everywhere in between), integration, and complementary controls. An example of complementary controls would be signature-based systems and heuristic-based systems, systems that are both context aware and intelligence aware, and systems that use URL, IP address, and file reputation services. Relying solely on one technology, one capability, or one identifying technique is dangerous at best. Today’s threat environment cannot be managed with simple signature-based controls. According to Symantec’s 2016 Internet Security Threat Report, in 2015 there were more than 430 million new unique pieces of malware released and 54 zero-day vulnerabilities identified.6 Greater reliance must be placed on advance detection capabilities and an integrated set of complementary controls. When developing your security architecture, you need to start with your data, then work outward and address databases, applications, infrastructure, the perimeter, and endpoints. Solving the cybersecurity challenges of tomorrow will require a combination of building and maintaining a current environment and investing in advanced security technology.
Maintaining a Current Environment
Cybercriminals continue to go after what are called Common Vulnerabilities and Explosures (CVE), meaning system vulnerabilities that are more than a year old, well known, researched and analyzed, and in most cases addressable. According to Verizon’s 2016 Data Breach Investigations Report,14 more than 85 percent of the incidents studied took advantage of a very old CVE, as much as five or six years old, while most of the remaining 15 percent took advantage of a CVE at least a year old. What this means essentially is that, as systems and cybersecurity professionals, we are our own worst enemy when it comes to making sure our enterprises are as protected as they can be because we are failing to address even the most basic of responsibilities; namely, applying hardening standards as we build out systems and deploy them, keeping those systems up to date with required service packs and patches, maintaining good discipline in managing their configurations and changes, and replacing or upgrading them when they become end of life or no longer supported. There are many reasons for this shortcoming, but the overwhelming one is usually lack of time. Considering the high tempo most modern IT shops keep just to match the rate at which new systems and applications are added and to accomplish the number of major changes or implementations required, they have little time for routine administrative or maintenance chores. The problem with this is that poor maintenance and administration leads to more downtime and greater susceptibility to exploitation. Similar to the automobile you drive, the longer you ignore maintenance, the sooner your network or systems will break down. Dissimilar to the automobile you drive, your network also has active threats attacking it constantly.
There are many examples of hardening guides that can be acquired for just about any device on the network. While there are not specific hardening guides for all systems and devices, there are hardening standards that can be acquired and used to build a guide and to turn it into a specific image to aid in build-outs. There are vulnerability scanners to aid in the identification of vulnerabilities that require patching, as well as scanners that can look for variances in policy or compliance settings on devices. These tools can also aid in the identification of systems either approaching end of life or already there. These scans can be run on schedule or ad hoc as needed. There are technologies for dynamically managing configuration to aid in the rollout of new policies, maintain configuration discipline, track changes, and enforce rules or compliance mandates. A change by an unauthorized person can be either disallowed or automatically rolled back to the original setting.
The firewall is still an important asset in protecting the perimeter and keeping the bad guys out, but today’s firewalls need to be a lot smarter than they use to be. Healthcare organizations should be deploying next-generation firewalls (NGFWs) and unified threat management (UTM) platforms that provide application control and user identity awareness capabilities. UTM platforms generally integrate several protective capabilities on a single platform at the perimeter, virtual private networks (VPNs), an intrusion prevention system (IPS), security protection and management, antivirus, and other tools to provide for more thorough traffic review. Though difficult in every environment due to business needs or network and application traffic requirements, firewall rules can be enabled to block traffic from high-risk countries, related threat information, and certain lists such as bad URLs, known botnet addresses, or known hacking sites. Some advanced firewalls permit blocking of Domain Name System (DNS) queries and will stop or inspect executables. Phishing, botnet, and spam attacks can be greatly curtailed by simply blocking these queries and not allowing automatic execution of code for downloads, attachments, and so forth. Legacy firewalls are not capable of handling the cyber threat healthcare now faces. Note that there are also multiple types of firewalls. Here we discussed perimeter firewalls; we will refer to other firewall types later.
Managing Privileges
Local administrative privileges can and should be eliminated wherever possible to avoid unscheduled or unapproved changes, dangerous downloads, and other risky actions. The first step in effectively managing privileges is to inventory and eliminate those that are not necessary or improperly matched with the user. Normal user accounts should never have elevated privilege, to preclude overuse or inappropriate use. Elevated privileges should also be managed more securely. Elevated privileges include local administrator accounts, privileged user accounts, domain administrative accounts, service accounts, application accounts, and emergency accounts.
Minimally, privileges should be encrypted, especially ones with administrative rights, when traversing the network. Privileges with administrative rights should also be subject to two-factor authentication so that a simple username and password combination is not sufficient to make changes affecting the network or critical applications. A technology that vaults privileges can strengthen the protection of elevated privileges even further. Essentially, all users have a standard user ID and password, but IT personnel who are authorized can authenticate to the vault to check out a set of administrative privileges when needed. The rights are issued to the person who logged into the vault and their usage can be audited. When the IT person is finished, they simply check the admin privileges back in to the vault. If they forget or just fail to do so, at a predetermined time the privileges expire. This eliminates active elevated privileges on the network that can be easily compromised and then used to exploit the network.
Thwarting Cyber Exploitation
Every organization needs to know where its critical systems and data are located before it can develop a cogent strategy for protecting them. One technology that gives us the ability to do just that at a very granular level for information is data loss prevention (DLP). DLP solutions are often thought of as security solutions, but they are actually more accurately categorized as enterprise-level data management solutions that just happen to enhance protection. DLP has three main components:
• Discovery
• Network enforcement
• Endpoint protection
The first component, discovery, uses a process called fingerprinting to accurately identify and index where all of our sensitive information is located throughout the enterprise, including both structured and unstructured data. This is no trivial undertaking. Without knowing where the sensitive information is located, the DLP deployment becomes more difficult. Therefore, discovery is critical to implementing DLP effectively.15 Fingerprinting permits very accurate identification of a document based on multiple key attributes of the document itself. Once a fingerprint has been created, the DLP system can detect the sensitive information contained in the document despite manipulation, reformatting, or modification. Most DLP systems can then identify derivative content from the original when captured in smaller passages, even when cut and pasted or retyped. This gives CISOs a very powerful tool for identifying where sensitive data are located in the enterprise and where they have greater resulting cyber risks.
The network enforcement component of the DLP solution allows for very specific rules to be enabled to allow or block certain activities based on system, user, or destination profile. This aids tremendously in reducing cyber risk by controlling where this information may be stored and transmitted, and by disallowing inappropriate actions by users. More importantly, though, this component provides a real deterrent to exfiltration of data by unauthorized individuals.
The endpoint component extends the protections and rule enforcement capabilities to platforms like desktops, laptops, and tablets, and allows the CISO to prescribe rules governing local storage, use of removable media, or functionality such as printing or thumb drives.
Isolating Cyber Threats
In 2016, multiple damaging attacks on healthcare entities were perpetrated using malware, ransomware, and zero-day viruses and caused serious disruptions to service and patient care. What aided these attacks greatly, both in the attack phase and the exploitation phase, was that many target locations were running flat networks. Flat networks, while greatly simplifying network management, offer little protection for critical assets once the perimeter has been compromised. Add to this the fact that most breaches are not detected for well over 100 days, and a flat network gives an attacker a considerable advantage. A better approach is to create a segmented enterprise that separates and allows apportionment of assets on different subnetworks to improve security. Segmentation if done properly provides many advantages in managing protected health information such as limiting or managing access, reducing risks from malware, and aiding containment and making critical or sensitive assets/databases less visible. Segmentation can be achieved by creating separate virtual LANs (VLAN). However VLANs alone will not provide the security desired. Segmentation is not effective unless enforced by either access control lists (ACLs) or firewalls.
There are many reasons why segmentation is important in healthcare. Health systems have Payment Card Industry Data Security Standard (PCI DSS) requirements for segmenting financial systems from the rest of the network. Hospitals have multiple groups accessing the network, not all created equal in access. Some hospitals seek to enhance their security posture by segmenting vendor-supported or -administered systems. Medical devices are well known for being insecure and representing a risk to the network. Many systems have legacy applications that are end of life and not capable of being secured any longer or are in the process of being replaced and not necessary in the day-to-day production environment. Segmentation firewalls permit organizations to place barriers between sensitive segments of their network or to isolate areas of greater risk. Segmentation also contributes significantly to the organization’s ability to effectively triage an incident and isolate the portion of the network affected, thereby aiding containment and reducing the number of systems that might have to be restored afterward. Internal firewalls can help to achieve defense-in-depth by forcing an attacker to penetrate multiple layers of security to reach mission-critical servers or applications.16
Detecting Cyber Intrusions
While next-generation firewalls generally integrate an IPS capability at the perimeter, the need for this technology goes beyond the perimeter to the internal segments of the enterprise as well. Monitoring anomalous traffic and activity over the network and on critical systems is also important, to detect internal exploitation. Each healthcare organization must determine whether an intrusion detection system (IDS) or an IPS is the best approach for the environment. Some health systems are concerned that IPS, which can automatically block certain traffic, connections, and so forth, may present safety risks if critical systems, communications, or segments of the network are blocked or affected. This is a valid concern and should be considered when determining a detection strategy. If an IDS is chosen over an IPS, then greater reliance will need to be put on active monitoring and alerting. For this reason, many health systems have chosen a managed security service provider (MSSP) that is capable of real-time monitoring and alerting along with stronger algorithms for anomaly detection and false-positive reduction. In addition to network-based IDS/IPS solutions that perform traffic analysis, there are also host-based IDS/IPS solutions that monitor for deviant behavior on servers and other platforms. Hospitals should consider host-based IDS/IPS solutions for many of their high-risk assets or assets that could be easily exploited such as legacy or end-of-life assets.
A good candidate for host-based IDS and key asset that plays a critical role in most healthcare enterprises is the Health Language 7 (HL7) Interface Engine. This asset sits between critical clinical, financial, and other applications and performs translations of data so that those systems can seamlessly communicate with one another. This system must decrypt the data from the sender before performing the translation process and forwarding the data to the receiver. Additionally, most interface engines store or archive a certain amount of the data they handle for contingency reasons. This system sits at the heart of the enterprise application environment, but is often dismissed as a part of the infrastructure because of its function. Interface engines are perfect candidates for host-based IDS/IPS due to their critical nature to operations, the sensitive data they process and retain, and the fact that only a very limited number of people need direct access to the engine.
Detecting Web-Based Threats
Many applications and services are web enabled to support the mobile workforce, collaboration with partners and vendors, and initiatives to promote patient engagement, population health, and a host of other activities. In many of these situations, connecting directly to the network is either not possible or not preferred. Web applications present a definite risk profile as assets that can be easily attacked externally. For that reason, it is highly recommended that organizations work only with reputable vendors when developing these platforms and always perform security testing of the application code to ensure its integrity. The vendors should be performing security testing throughout their development process, and it would be important to review this with them.
Testing of web application code is done from two perspectives: from the outside in, using dynamic application security testing (DAST), and from the inside out, through code review using static application security testing (SAST). Both are important and provide an understanding of the vulnerabilities of the application both from within and from outside.17 Vulnerability scanning and penetration testing, discussed later in the chapter in “Looking for Vulnerability,” is considered DAST. For most commercially acquired web applications, this type of testing is usually the norm. Testing should be conducted against both the application and the hosting platform. Web application firewalls can also be used to provide another layer of filtering and protection for assets.
Detecting the Unknown
Malicious content can enter the enterprise from a multitude of directions, pathways, and devices. Building early and accurate detection can assist incident response efforts by limiting the impact of a particular attack. There are multiple technologies that can aid in detecting and avoiding malware. Antivirus solutions, secure e-mail gateways, secure web gateways, sandboxing, advanced malware detection solutions, and mobile device management solutions are some technologies that should be incorporated into the cybersecurity strategy for protecting the network and information assets. Antivirus solutions have been around for a very long time, and work on a simple premise that there is a list of signatures of known bad actors. When the antivirus protection running at the perimeter or on an internal platform detects/recognizes traffic as possessing one or more of these signatures, it blocks that traffic from entering. There are many different antivirus solutions, and they do not all function the same. Ideally, more than one antivirus engine should be used on different parts of the network: at the perimeter, on the e-mail gateway, on servers and workstations, and on endpoints. Secure e-mail gateways provide malware and phishing detection and prevention. This technology can inspect e-mail for malicious content, attachments, web links, and executables. Secure web gateways work much the same way as e-mail gateways, enabling inbound inspection of web traffic as well as outbound inspection. These can work in conjunction with a cloud-based sandboxing capability to open and inspect questionable content before it has the chance to affect the network. Advanced malware detection solutions should be implemented to help detect malicious content that antivirus just cannot see. Mobile device management solutions are not normally thought of as advanced detection platforms, but with their ability to monitor mobile devices and ensure that they have not been tampered with or had their security features disabled, they can reduce the risk of compromised mobile devices from affecting the enterprise.
Addressing the Ubiquitous Threat of IoT
Society in general is becoming more and more connected and data aware in its quest for fast information in convenient form wherever and whenever users want it. More and more routine processes are becoming automated to enhance convenience in management of functionality. The Internet of Things encompasses many commercial devices, including smart TVs, smart locks, smart refrigeration, smart environmental controls, smart vehicles, and of course smartphones. All are networkable, usually over a wireless connection, but some are on the network itself.
The IoT extends to healthcare as well. Healthcare is being extended steadily out to wherever the patient exists, whether that is in their home, their workplace, or where they recreate. We have medical devices that are connected and communicate both across the ethernet and over the wireless network (see Chapter 31 for more information). These include various devices deployed throughout the hospital setting, devices that travel with or on the patient, and devices that monitor the patient or the patient’s environment. The overwhelming majority of these devices at the time of this writing are not secure and represent a credible cyber threat to both patient safety and the enterprise. “More than 25% of cyber attacks will involve the Internet of Things (IoT) by 2020, according to technology research firm Gartner.”18 As fast as these devices are being developed they are being compromised. These devices represent a particularly attractive target for cybercriminals and hackers because they are additional gateways to the healthcare systems and networks. The numbers of connected devices after 2016 is expected to be in the tens of billions, which represents multiple devices per person. The challenge with these devices, just like medical devices, is that there is no standard architecture or security requirements that apply when companies develop them, so healthcare organizations are left with having to find ways to architect security around them.
Probably the most concerning from an IoT cyber threat perspective are distributed denial of service (DDOS) attacks. A prominent example of this is the Mirai hack that uses sophisticated malware to commandeer smart devices accessible via the Internet and combine them into very powerful botnets capable of launching crippling DDOS attacks. In October of 2016, thousands of critical applications, including EHR systems, were taken offline by a massive Mirai attack that used corrupted devices from all over the world to attack the DNS servers at a company called Dyn. The Mirai attacks underscore the security vulnerability of these devices and the risk they pose to network, communications, and critical services. There are ways to mitigate this risk, but they aren’t easy to implement: they require manufacturers to design devices with fewer inherent flaws and consumers to rethink how they implement these devices and the security they place around them. This type of attack highlights how interconnected we all are as a society and as businesses and accentuates the need for everyone to do a better job of protecting their own environment for the sake of society in general.
Monitoring Activity
Every hospital needs to develop its auditing strategy and enable logging to support that strategy. A log is a record of the events occurring within a computer system or network. A log may be made up of many (hundreds or thousands or even millions) entries. Each entry contains information related to a specific event that has occurred within that system or network. The number and volume of computer logs have increased greatly since 2009 with the advent of EHRs and the massive automation of processes in healthcare over the last decade, creating the need for automated log management.19 The first step is to enable logging on all systems. The second is to move those logs off the primary system to a log repository, usually a dedicated server or a storage area network (SAN). The next step is to implement a log manager. This technology will then aggregate log data and identify security, operational, and compliance events and report or alert as configured. These events can number into the thousands. Many of the mainstream log managers have industry-specific modules to facilitate the reporting and alerting process. If a hospital system has a contract with a managed security service provider, a log manager may or may not be required. If one is used, it will send its logs to the security information and event management (SIEM) system that the MSSP is using. If a log manager is not used, the MSSP usually deploys a collector that in turn communicates with the SIEM. Organizations may opt to perform manual audits of system and user activity although it is not recommended. If they do, then attention must be given to the individual who is going to review the logs/events, planning must be done for log collection and log review, and procedures must be implemented around alerts and communicating escalation, troubleshooting, identifying false positives, remediation and log retention.
Under the HITECH Act patient information was supposed to be digitized and securely held in Certified Electronic Health Record Technology (CEHRT). Organizations were told that as long as they implemented CEHRT in a meaningful way, then security would be sufficiently addressed. However, databases and those who had direct access to those databases were not adequately covered by the security requirements of that technology. Immediately, CISOs understood they had a problem. While access to the data in the EHR could be audited through the application, direct access to the database supporting the application could not. Fortunately, there is technology for this purpose: database activity monitoring (DAM). DAM audits database access, audits users with elevated privileges such as database administrators, and helps protect against cyber events. All forms of privileged user can be monitored in databases, including superusers, administrators, sysadmins, developers, help desk personnel, and third-party personnel. DAM monitors application activity matching specific database actions with specific users to identify abnormal activity. DAM can then thwart certain attacks by creating a baseline of what is normal and alerting/reporting on deviations from that baseline to security analysts.
The insider threat continues to dominate the number of incidents that occur each year, although they only account for roughly 1 percent of the records potentially compromised. However, even if small in number in terms of impact, workforce members who snoop or otherwise access patient information create real compliance challenges for health systems. Fortunately, a new set of technologies called user and entity behavior analytics (UEBA) can profile user behaviors and detect inappropriate activity. Before UEBA came Privacy Activity Monitoring, systems that essentially perform the same log or event analysis, but as it related to application access and activity related to users. Privacy monitoring is widely used in healthcare today as hospitals seek to deal with the insider threat issues, but most privacy monitors fall short of being truly effective beyond narrow compliance monitoring. They rarely catch the person or persons engaged in real crimes like identity theft or medical identity theft because they lack behavioral modeling. These early user technologies are sufficient for monitoring for compliance purposes. Organizations can define their audit program and automate checks against compliance requirements. They can also run ad hoc investigations into user activity and, depending on the number of applications, perform limited event correlation. In some cases they can even create baselines for user behaviors and then monitor against those norms to identify when a workforce member’s behavior is not normal. UEBA combines monitoring of workforce members’ behavior with entity events to identify when either they or third-party individuals are engaging in suspicious behaviors.
Conducting Information Correlation and Analysis
SIEM solutions have long been touted by their vendors as the holy grail of security, enticing many in security to purchase them. Unfortunately, more often than not, figuring out how to use them has proven as elusive as tracking down another well-known grail. In truth, SIEMs are at the top of the security pyramid as it relates to detection and monitoring. SIEMs are very complex solutions that require a significant amount of security expertise and experience to implement and manage. When sitting on top of a well-managed, well-architected foundation of security controls and technologies, they become very powerful correlation engines capable of connecting the dots between multiple events occurring on many systems, at different times, in different parts of the enterprise to produce a cohesive picture of a security event or policy violation. For SIEMs to be such powerful correlation engines, they must gather information from a host of network and security devices and applications, such as IDS/IPS, antivirus, malware filters, vulnerability scanners, policy compliance systems, servers, workstations, databases, application logs, and threat databases. Additionally, SIEMs require sophisticated algorithms to make sense of all the information collected and analyzed.
The sheer volume of security events and attacks detected in the healthcare enterprise makes monitoring, correlation, and analysis all but impossible without technology and expertise. While the technology can be acquired, such as log managers, privacy application monitors, IDS/IPS, and SIEMs, very few health systems have the real expertise necessary to optimize their utility. The average hospital will produce tens of millions of events each month, with the overwhelming number of these being “noise” and only a few being actionable. The trick is being able to synthesize all of those events down to what needs attention. The expertise becomes critical when writing the rules and the algorithms necessary to carry out that synthesis. Expertise is required to know which information is critical, to understand and analyze network traffic, and to know how to optimize each technology to support the correlation process. This is an area in which MSSPs excel. They know how to tune IDS/IPS sensors for optimal performance, how to configure logging to collect the right system/user events, and how to incorporate firewall logs, vulnerability scanning results, and other feeds to facilitate correlation and analysis. They also have the advantage of extensive libraries of specific rules that they can implement and algorithms they can use to support correlation. They can provide these services better, faster, and more reliably because they monitor thousands of organizations across the globe in real time around the clock.
Looking for Vulnerabilities
To provide assurance regarding the integrity of the enterprise and its constituent systems, an organization needs to perform technical testing, a process that begins with automated vulnerability scans and culminates in a penetration test. Technical testing is an important part of any security program. This in-depth security testing allows an organization to better understand its security posture and find potential vulnerabilities before they are exploited by bad actors. Technical security testing includes two important aspects:
• Vulnerability scanning Vulnerability scanning should be performed frequently, often on a monthly or at least quarterly basis, to ensure new issues are identified quickly as well as to verify the remediation of previously found issues.
• Penetration testing (pentesting) Pentesting requires an analyst with a very specialized skill set. Because of this and the nature of pentesting, most organizations perform these tests at least annually. Pentests can be performed as frequently as quarterly.
Vulnerability Testing
Scanning for weakness in the environment is the first step. Vulnerability scanners have large databases of known vulnerabilities and their associated digital signatures. The scanning software will scan the systems within a defined scope for evidence of potential vulnerabilities based on the signatures in its database and how the systems in scope respond to specific types of requests. According to the SANS institute, “Vulnerability Scanning is the art of using one computer to look for weaknesses in the security of another computer—so that you can find and fix the weaknesses in your systems before someone else finds that there is a security weakness and decides to break in.”20
There are numerous tools available that are used to perform automated vulnerability scanning. These tools range from very general testing tools that will test virtually any platform and can test compliance with virtually any standard, to very specific tools that test one type of appliance or system. The cost of these software packages also ranges greatly, from open source (free) to tens of thousands of dollars a year in licensing fees. The tools that have a high cost for licensing are known industry-wide and their results are relied upon universally. The open source community has provided some incredibly useful tools as well. Descriptions of some of these tools follow:
• OpenVAS (www.openvas.org) is one of the most popular of the open source tools available. OpenVAS is a fully functional, regularly updated, and reliable automated vulnerability scanning tool.
• Nessus (www.tenable.com/Nessus), offered by Tenable Network Security, is possibly the most popular general-purpose vulnerability scanning solution available. Nessus is a paid program, for commercial use, but is widely considered the gold standard in vulnerability scanning throughout the industry.
• Qualys Vulnerabilty Management (https://www.qualys.com/suite/vulnerability-management/) and Nexpose from Rapid7 (https://www.rapid7.com/products/nexpose/) are two other popular vulnerability scanning tools that are commercially available.
In general, most of the commercial vulnerability scanners available are roughly equivalent to each other, and they tend to have much the same functionality as well. The paid solutions work better for large organizations because they provide customized signatures, centralized reporting, and several other features that make any of the paid options a good choice.
Before scanning, the scope of what is to be tested must be determined as well as when the testing will be performed. This decision-making process, called scoping, defines the parameters of the testing process and which systems should be tested at what times. This process also specifically defines which systems should not be tested. This is an important step in healthcare, as care must be given to scanning clinical assets and systems connected to patients. Scoping conversations should always include key system owners and IT security specialists. A risk-based approach is used to make scoping decisions.
Performing the actual scan(s) comes next. All popular vulnerability scanning tools have comprehensive scheduling systems built in to make scheduling much simpler. These systems allow the analyst in charge of the program to set up scanning profiles for each type of scan that was determined during scoping. Often, it is preferred to organize assets to support reporting and/or risk concerns. Assets can be grouped by who manages them (in house/vendor) or by responsible group (server team/network team). They can be grouped by sensitivity (clinical/legacy/network), and for sensitive assets or at-risk assets, scans can be run using safer profiles to permit better observation and response if an incident occurs. After the analyst has developed or selected a preconfigured scanning profile, it is time to set up the scanning schedule. Scans can be accomplished automatically on a regularly recurring basis or performed manually on an as-needed basis. Again, careful consideration should be given to hospital operations to make sure that when scans are executed, staff is present to respond if needed.
Scanning tools have the ability to generate reports in multiple formats. Minimally, reports will list the systems scanned, the identified vulnerabilities, and severity ratings. The analyst should be prepared to generate an executive summary report for leadership and a detailed technical report for the system administrators, or owners, that will work to remediate the issues.
The most important aspect, besides the initial reporting of issues, is follow-up. This means that a system administrator or owner informs the scanning team or analyst that they have remediated the previously identified issues. At this point it is the responsibility of the vulnerability scanning analyst to scan that system again to ensure that the vulnerability is no longer present. If the scan reports that the vulnerability in question has been fixed, the vulnerability scanning analyst can sign off that the finding has been remediated.
Penetration Testing
Vulnerability scanning alone is not enough to protect an organization from attack. The next critical piece of a comprehensive technical security testing program is penetration testing. Penetration testing is a test of system or network vulnerabilities by authorized testers in which they attempt to break into the systems that are in scope. This is all done from the perspective of a malicious attacker, either from inside the network or external to the network.
Pentests typically begin with several simple network discovery scans and a vulnerability scan. The pentester will then manually verify any serious findings from the vulnerability scans. By doing this, the pentester is able to confirm the existence and exploitability of the vulnerability scanner’s results. This enables the organization to better understand its security gaps and better prioritize remediation efforts based on likelihood and ease of exploiting those vulnerabilities.
The goal of pentesting is to emulate the activities of a malicious attacker. To help build in a level of consistency, several organizations have taken the time to develop in-depth pentesting frameworks. These frameworks ensure that testing and reporting follow a consistent process that is verifiable, thorough, and repeatable.
Depending on the target organization’s regulatory requirements (i.e., PCI-DSS, HIPAA, Sarbanes-Oxley [SOX], etc.), there may be an annual pentest requirement. The specific framework for these tests is often prescribed. The two most common frameworks in use today are NIST Special Publication 800-115, “Technical Guide to Information Security Testing and Assessment,” and the Penetration Testing Execution Standard (PTES). There are many other frameworks in existence, but the basic principles remain the same in all of them.
Both NIST 800-115 and PTES have a staged approach that follows a logical set of steps, with each step building on the previous steps. The PTES framework breaks down a typical pentest into seven phases, or stages, shown in Table 30-1.
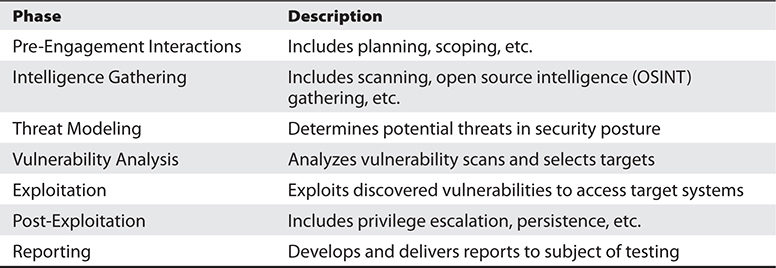
Table 30-1 Seven Phases of the Penetration Testing Execution Standard (PTES) Framework
NIST 800-115 uses only four phases to present the penetration test: Planning, Discovery, Attack, and Reporting. However, all of the same actions are called for in both standards. NIST 800-115 combines the PTES Intelligence Gathering, Threat Modeling, and Vulnerability Analysis phases into the Discovery phase and combines the Exploitation and Post-Exploitation phases into the Attack phase.
There are hundreds of useful tools available to testers that vary greatly in scope, cost, and usefulness. Because of the nature of pentesting, and the hacking community it arose from, the vast majority of popular pentesting tools are open source and free to use.
Most pentesters use a particular Linux distribution called Kali Linux (https://www.kali.org), which is considered the gold standard in pentesting toolsets. This distribution is maintained and funded by Offensive Security (https://www.offensive-security.com/). Kali Linux comes with hundreds of open source tools preinstalled for almost any tester situation, and has hundreds more available for simple installation in the online repositories. There are entire books written about some of the individual tools in the Kali distribution and several books about Kali itself that cover the technical details of these tools.
The makers of Nmap, a very popular open source security tool, have developed a comprehensive list of the top 125 network security tools (www.sectools.org) that contains detailed information on each. Table 30-2 is a brief overview of five of the most commonly used network security tools available and includes links to additional information.
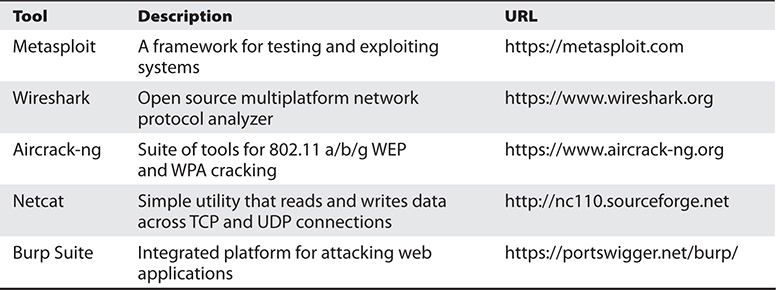
Table 30-2 Five of the Most Commonly Used Network Security Tools
Scoping a pentest is a little different from a vulnerability scan. In vulnerability scanning, the hostnames or IP addresses are populated in a database and scheduled to be scanned. The scanning itself is accomplished automatically. In pentesting, much of the process is completed manually, and as a result, each additional system added to the scope means additional hours the tester will need to expend. On the other hand, it is important to know that despite the time needed, the scope should be as broad as can be managed. By limiting the tester to fewer systems to test, the chances of their detecting a vulnerable system decreases.
It is also useful to remember that criminal attackers do not limit themselves with respect to scope or impacts, nor do they care about whatever policies are in place. They are breaking the law already, so they are not going to leave specific systems alone. If possible, the tester should be allowed to complete a full-scope test at least annually, meaning all systems owned and operated by the entity being tested should be in scope.
After the scope has been determined, the tester follows the steps laid out by the selected framework, starting with discovery. During discovery, the tester scans the in-scope networks and systems for live systems using a simple ping scan. Once the live systems on the network have been identified, the tester performs increasingly complex scans in order to gather as many details as possible about the targets. By the end of this phase, the tester should have a significant list of detailed information about the in-scope systems. These scans provide information such as IP addresses, hostnames, open ports, running services, operating systems, and so on.
The tester then compares what they have learned with a recent vulnerability scan report to identify the most likely targets for the exploitation phase. The exploitation phase begins with vulnerability verifications in which the tester attempts to exploit the vulnerabilities reported from the vulnerability scanner. As the tester moves through the verifications, often more potential targets and vulnerabilities are identified, which are run through the discovery phase again and moved back into the exploitation phase.
After exploitation is accomplished on the first set of systems, the tester begins post-exploitation activities. These typically include exfiltrating sensitive data, adding privileged user accounts, installing malware, and using other techniques to elevate their access and ensure they can get back in (persistence).
A pentesting report is similar to a vulnerability scan report in that it will also include discovered vulnerabilities, risk ratings, and remediation suggestions. The key difference is the analysis is performed by the tester, which provides additional insight into the security and vulnerabilities that no automated systems can match. In most cases the tester will provide the subject of the test with an executive report or presentation along with a detailed technical report for the system owners and administrators.
Red Teaming for Readiness
Another very effective set of activities that can be implemented to ensure an organization is ready for cyber incidents is a series of red-teaming activities such as cyber exercises, physical penetrations, social engineering, and phishing exercises. Each of these activities is designed to emulate an actual cyber threat experience. Red-teaming activities serve several very important purposes:
• They permit review of procedures, response times, coordination processes, team member knowledge, and so forth so that the organization can improve its performance.
• They permit learning from mistakes in a nonimpact environment so that teams can identify areas for advanced training.
• They increase familiarity and awareness among staff, which improve chances of success because staff and team members know what to expect.
Cyber exercises can be conducted as table top exercises, real-time exercises, or simulations. To be most helpful, they should be run at least twice a year. Social engineering tests and phishing exercises, which are really geared toward changing user behavior and elevating awareness of the threats, should be run more often, minimally quarterly, and should emulate actual attacker methods for both general and spear phishing types. Phishing is the number one security threat facing healthcare organizations, but only one-third of the organizations responding to a 2015 HIMSS survey considered themselves adequately trained to repel phishing attempts.21 Anyone who responds to a phishing attempt should be directly immediately to training on what they did wrong and what they should look for in the future. This immediate feedback and refresher training is critical to achieving behavior modification. Physical penetrations can be run once or twice a year to test guards, access controls, surveillance, and so forth.
Chapter Review
This chapter covered a brief history of the changes in healthcare that have contributed to the current environment, the increase in cyber incidents, and factors that have made health information systems and patient information so attractive to the criminal element. It also explained how the healthcare information technology ecosystem has evolved to be more complex and sophisticated, adding further to the challenges in protecting health information. Since the rapid adoption of EHRs stimulated by the HITECH Act of 2009, the threat itself has also become more sophisticated and disruptive, increasingly more focused on the healthcare industry. More than 430 million new unique pieces of malware were released in 2015 and that number is expected to increase each year. The number of zero-day attacks also has risen significantly, rendering traditional signature-based security solutions all but obsolete. There has also been an escalation of targeted attacks that have disrupted services, resulting in millions of records compromised and patient safety put at risk. The types of actors who now target healthcare have also broadened from malicious insiders and cyberthieves focused mainly on fraud to state actors, cybercriminals, extortionists, and hacktivists. Healthcare organizations must increase the level of threat awareness across their workforce and implement technologies and services that provide actionable intelligence in a timely manner to aid risk avoidance and support quick response to cyber events. They should also take advantage of the abundant resources on cybersecurity threats that are made available by organizations such as NH-ISAC, US-CERT, and InfraGard (the FBI partnership).
Organizations that use a security framework to guide their strategic plan improve their ability to build an effective cybersecurity program. The NIST CSF for healthcare was specifically developed to assist healthcare organizations in the implementation of best practices around data protection while meeting compliance objectives. Frameworks provide a common taxonomy for organizations to demonstrate their security compliance, implement continuous assessment against a standard, communicate both internally and externally on cyber readiness, and provide the structure for identifying a target end state with priorities to achieve the target end state.
Effectively combating cyber threats starts with laying a solid foundation that includes addressing the basics of network architecture, system administration, and maintenance. This includes establishing hardware and software refresh cycles to eliminate legacy or unsupported systems, and ensuring the network and systems are hardened appropriately and maintained through consistent patching, change control, and configuration management practices. It also includes ensuring adequate segmentation and restricting and protecting privileges. Elevated privileges should be eliminated, if possible, through vaulting, or at the very least encrypted in transmission and enabled by multifactor authentication.
Building a security architecture that is capable of meeting today’s cyber threats requires addressing every layer of the enterprise, from the core out to the endpoints and third-party services such as Software as a Service (SaaS) via the cloud. It also requires an integrated mix of many different technologies and services that support each facet of the security framework from identification to response. In particular, organizations need to improve detection capabilities. The architecture needs to complement more traditional solutions like firewalls and antivirus with newer behavior analytic technologies like advanced malware solutions. Organizations need to improve audit and monitoring capabilities and consider seriously working with an MSSP to automate things like log management, IDS/IPS, and event correlation with SIEM.
After evaluating controls using a framework and implementing a secure architecture, organizations must be diligent in testing their security posture. Conducting risk analysis, performing security control audits, undergoing vulnerability and penetration testing, and conducting red-team efforts are all important to managing and reducing cybersecurity risks.
Questions
To test your comprehension of the chapter, answer the following questions and then check your answers against the list of correct answers that follows the questions.
1. The cyber threats facing healthcare today include which of the following?
A. Extortion
B. Hacktivism
C. Espionage
D. All the above
2. Which of the following is not typical of how external attacks are initiated?
A. Phishing
B. Social engineering
C. Brute-force attack
D. Water-cooler attack
3. The thing that makes ransomware particularly troublesome for healthcare is:
A. It encrypts data
B. It involves negotiating with an extortionist
C. It undermines the health system’s ability to provide care
D. It only attacks health systems
4. While there are more physical thefts and loss of data events, hacking still represents the biggest risk because:
A. It is the most damaging
B. It represents the largest risk of compromised records
C. It is conducted by cybercriminals
D. It is bad for business
5. Using a framework like the NIST CSF provides which of the following benefits?
A. A guideline for building and selecting controls
B. A way of demonstrating compliance
C. A way of communicating cyber readiness to business partners
D. All of the above
6. Limiting access is a key component of preventing cyber events. Which of the following is not a recommended practice?
A. Encrypting just elevated privileges
B. Vaulting elevated privileges
C. Applying additional authentication factors to privileges
D. Encrypting all privileges
7. Most disruptive attacks that spread rapidly through an enterprise are aided greatly by a lack of ____________.
A. segmentation
B. access control
C. new hardware
D. educated users
8. Successfully monitoring and detection of cyber events in the future will likely involve which of the following?
A. Use of advanced detection systems with behavioral-based approaches
B. Advanced event correlation and analysis
C. Partnering with a managed security service provider for expertise
D. All the above
Answers
1. D. Healthcare organizations today face cyber threats in the form of extortion attempts, wholesale theft of data for espionage, as well as long-term exploitations and hacktivism when groups do not like positions that the organizations have taken on social issues.
2. C. Most hacking starts with social engineering, phishing, or water-cooler type attacks because they are easier and less risky.
3. C. Ransomware has become a very real threat to healthcare because it does affect directly healthcare’s ability to deliver care by disrupting its systems, communications, and data.
4. B. Hacking as of 2015 now represents the greatest risk to patient information from a compromised records perspective. While physical theft and loss still account for the majority of events, hacking, by a wide margin, accounts for the greatest number of records compromised.
5. D. Using a framework like the NIST CSF provides many benefits, including a structure for selecting controls, a method of measuring maturity, and a way to demonstrate compliance or communicate security posture to others.
6. A. Encrypting all privileges, applying multifactor authentication, and vaulting elevated privileges are all recommended practices for limiting access, a key component of making the enterprise more resilient to threat. If hackers cannot get hold of privileges, their task of exploiting the enterprise is exponentially harder.
7. A. Lack of segmentation, typical of flat networks, is the biggest enabler of rapidly spreading viruses, ransomware, and other network attacks. Other factors contribute, of course, but lack of segmentation is the chief limiting factor in being able to stop the spread of an attack once it occurs.
8. D. Successful monitoring requires the integration of many systems, with advanced detection capabilities, and the use of advanced correlation and analysis tools like SIEM. This task, for most organizations, has grown too complex, and requires 365/24 coverage, which most cannot provide, making partnering with a managed security services provider (MSSP) necessary.
References
1. U.S. Department of Health and Human Services (HHS). (2009, Feb. 17). HITECH Act: Enforcement interim final rule. Accessed on August 15, 2016, from www.hhs.gov/hipaa/for-professionals/special-topics/HITECH-act-enforcement-interim-final-rule/index.html.
2. Ponemon Institute. (2016, June). Cost of data breach study: Global analysis. Sponsored by IBM. Accessed on August 15, 2016, from https://app.clickdimensions.com/blob/softchoicecom-anjf0/files/ponemon.pdf.
3. Abagnale, F. (1980). Catch me if you can. Grosset & Dunlap.
4. Farrell, M. B., & Wen, P. (2014). Hacker group anonymous targets Children’s Hospital. Boston Globe, April 24. Accessed on August 15, 2016, from https://www.bostonglobe.com/business/2014/04/24/hacker-group-anonymous-targets-children-hospital-over-justina-pelletier-case/jSd3EE5VVHbSGTJdS5YrfM/story.html.
5. “Zack.” (2016). Hurley Medical Center confirms “cyber-attack” as Anonymous hacking group threatens action over Flint water crisis. Epoch Times, January 22. Accessed on August 15, 2016, from www.theepochtimes.com/n3/1947837-hurley-medical-center-confirms-cyber-attack-as-anonymous-hacking-group-threatens-action-over-flint-water-crisis/.
6. Symantec. (2016, April). Internet security threat report/healthcare, vol. 21. Accessed on August 15, 2016, from https://www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016-en.pdf.
7. Symantec. (2017, April). Internet security threat report/healthcare.
8. Cybersecurity Information Sharing Act of 2015, 114th Cong., 1st Sess. (October 27, 2015). Accessed on August 15, 2016, from https://www.congress.gov/114/bills/s754/BILLS-114s754es.pdf.
9. Diamandes, P. (2015). My predictions for the next ten years. Huffington Post, May 6. Accessed on August 15, 2016, from www.huffingtonpost.com/peter-diamandis/the-next-10-my-prediction_b_7172978.html.
10. US-CERT. (n.d.). Information sharing specifications for cybersecurity. Accessed on August 9, 2016, from https://www.us-cert.gov/Information-Sharing-Specifications-Cybersecurity.
11. PhishMe. (2015). Enterprise phishing susceptibility report. Contributing analysis by University of Cambridge, London School of Economics and Political Science. Accessed on August 15, 2016, from https://ca.insight.com/content/dam/insight-web/Canada/PDF/partner/phishme/PhishMe-EnterprisePhishingSusceptibility.pdf.
12. Yaraghi, N. (2016, May). Hackers, phishers, and disappearing thumb drives: Lessons learned from major health care data breaches. Brookings Institution. Accessed on August 15, 2016, from https://www.brookings.edu/wp-content/uploads/2016/07/Patient-Privacy504v3.pdf.
13. National Institute of Standards and Technology (NIST). (2014, Feb. 12). Framework for improving critical infrastructure cybersecurity. Accessed on August 15, 2016, from https://www.nist.gov/sites/default/files/documents/cyberframework/cybersecurity-framework-021214.pdf.
14. Verizon. (2016). Data breach investigations report. Accessed on August 15, 2016, from www.verizonenterprise.com/resources/reports/rp_DBIR_2016_Report_en_xg.pdf.
15. Forrester. (2016, July 7). The future of data security and privacy: Growth and competitive differentiation. In The data security and privacy playbook for 2017. Accessed on August 15, 2016, from https://www.forrester.com/report/The+Future+Of+Data+Security+And+Privacy+Growth+And+Competitive+Differentiation/-/E-RES61244.
16. SANS Institute. (2001). Achieving defense-in-depth with internal firewalls. Accessed on August 15, 2016, from https://www.sans.org/reading-room/whitepapers/firewalls/achieving-defense-in-depth-internal-firewalls-797.
17. McDonald, N. (2011). Static or dynamic application security testing? Both! Gartner Blog Network, January 19. Accessed on August 15, 2016, from http://blogs.gartner.com/neil_macdonald/2011/01/19/static-or-dynamic-application-security-testing-both/.
18. Ashford, W. (2016). IoT to play a part in more than a quarter of cyber attacks by 2020, says Gartner. ComputerWeekly.com, April 25. Accessed on August 15, 2016, from www.computerweekly.com/news/450288414/IoT-to-play-a-part-in-more-than-a-quarter-of-cyber-attacks-by-2020-says-Gartner.
19. Finn, D. (2016). The future of information security in healthcare. In D. Garets & C. M. Garets (Eds.), The journey never ends: Technology’s role in helping perfect health care outcomes. Boca Raton, FL: CRC Press for HIMSS Media.
20. SANS Institute. (2003). Vulnerabilities and vulnerability scanning. Accessed on August 15, 2016, from https://www.sans.org/reading-room/whitepapers/threats/vulnerabilities-vulnerability-scanning-1195.
21. Healthcare Information and Management Systems Society (HIMSS). (2015, June 30). Cybersecurity survey. Accessed on August 15, 2016, from www.himss.org/2015-cybersecurity-survey.
