Chapter 27. Managing Your Windows Security
In This Chapter:
- Learn to recognize computer security threats
- Find programs that help you secure your computer as well as possible
- Enjoy safer online web surfing
- Correctly respond to Internet Explorer’s security warnings
- Master your Control Panel’s security settings
- Modify your firewall settings
- Keep your computer up-to-date automatically
- Use Windows Defender to monitor all files on your machine
- Set parental controls to safeguard your younger family members
Microsoft is well aware of the security risks Windows operating systems face. When they developed Windows XP, the Microsoft programming team made security a high priority. Nevertheless, the moment Microsoft released Windows XP, the attacks began. In Microsoft’s defense, the security flaws that have since been exposed could not have been 100% foreseen because new hardware and software developments since XP’s release have allowed Trojan programs, worms, spyware, and virus emails to flood users’ systems. Neither Microsoft nor any other developer could have predicted how severe these attacks would become.
Attacks on non-Microsoft operating systems are less frequent than Windows-based systems. This is true, but it’s also true that with the much larger installed base of products, malicious hackers are going to go after the largest number of installations and not spend as much time attacking the other environments. However, Microsoft designers certainly could have made XP a little more secure than they did. Having learned from past mistakes, Microsoft has made a valiant effort to keep Vista secure.
In this chapter, you’ll learn ways Microsoft designed Vista to protect you. If you’ve read articles about computer security in the past, you know that security is a subject that quickly gets highly technical. This chapter addresses security from a hands-on approach that enables you to take charge of common security issues without having to become a security technician to understand what you need to know to protect your safety when using Vista.
Vista Security—A Brief Overview
To make proper decisions regarding security settings, it helps to have an overview of some security approaches Microsoft chose when developing Vista. You probably already understand that before you can make any major security decisions you must be running from an Administrator account, as explained in the Chapter 26, “Separating Users Gives Each the Access They Need.” Without an Administrator user account, you can run common programs but can do very little with system programs.
Security and the stability of your computer go hand-in-hand. You want your computer to remain secure and you want it to operate as expected. If a security threat gets through your protection, your machine will stop working properly. Vista does its best to protect your system-related folders. If a malicious program attempts to write to your Program Files folder, for example, and doesn’t have the appropriate certification to do so, Vista will block the attempt.
Partitioning Danger
Old programs, called legacy programs, might write directly to your Program Files folder without going through the normal security clearance routines that Vista-written programs go through. Vista can’t simply block these programs altogether because some people still want to run programs they purchased long before Vista arrived.
Vista fools such programs into thinking they are writing to your Program Files folder, but they are actually writing to a folder that looks to legacy programs as if it were the Program Files folder. Therefore, if a malicious coder writes such a program that acts like a legacy program, and the code infects a computer’s files, Vista will help ensure that, at worst, the danger will be limited to the user account that was active when the program was installed.
Did you Know?
If such a problem occurs, you can log on to another user account and use your computer normally, accessing all the programs you were able to access from your previous account. This is a good reason to create a second, password-protected Administrator account for yourself now and leave it alone until you absolutely must use it because of damage to your original account. All your personal settings in that other account will be lost, so regularly back up your user account’s files in case you have to restore them to your new account. (Chapter 35, “Protecting Your Data and Programs,” explains how to back up files and folders.) Your user account’s files are always stored in a folder named after your user account name. When you open an Explorer window, you see your account’s folder in your Users folders list as Figure 27.1 shows.
Figure 27.1. All user folders are located inside the higher-level Users folder.

How Safe Is Vista?
Are Vista’s security protection tools adequate to protect you? Vista’s security is wonderful compared to what has come before. But Microsoft would be the first to admit that Vista by itself does not provide a completely secure computing environment. Although nothing can fully ensure that you’ll be safe when you use your computer, you should augment Vista’s built-in versions of the following programs with more complete offerings you can get from known and reputable vendors:
- Firewall—A program that guards your Internet data entry and exit points (called ports) and keeps your always-on, Internet broadband connection secure from intruders. ZoneAlarm and Symantec’s Norton Firewall are two well-known firewall programs. See www.ZoneLabs.com and www.Symantec.com.
- Antivirus—A program that helps keep email-delivered viruses from affecting your system, as can happen if you open some emails or click links in others. Norton AntiVirus and McAfee VirusScan are two capable antivirus programs that you can get to help safeguard your email. See www.Symantec.com and www.McAfee.com.
- AntiSpyware—Try as you might, some programs can find their way onto your computer. You might download and install a free program that you find online and even if that program is safe, it might bring with it other programs called spyware that pop up ads or use your computer’s idle time for sometimes innocent and often troublesome uses. www.WebRoot.com and www.Lavasoft.com provide extremely effective spyware removal tools that you may want to try if Vista’s own Defender doesn’t catch everything for you.
Did you Know?
Most security program vendors provide free trial periods during which you can try the program at no cost. In addition, watch the Sunday color ad inserts in your newspaper for computer stores in your area. After-rebate deals are often available that allow you to get these security-related programs absolutely free after rebate. It’s the hope of the vendors that if they give you the program for a year, you will pay to subscribe for another year of protection.
Software companies offer most security-related programs on a subscription basis, and you have to pay annually to renew your subscription if you want protection against the latest threats. These vendors attempt to stay on top of the latest problems and send you updates regularly (sometimes daily, depending on what’s happening in the world of computer infections). As long as you’re paid up, you will get the latest updates.
You Cannot Have Too Much Money, Too Much Good Health, or Too Much Computer Security
Throughout the rest of this chapter, you’ll learn how Vista offers protection for each of the problem areas just mentioned. Use Vista as your starting point, base-level security and then build on its security with appropriate programs you get elsewhere.
You cannot be too secure, so having a dedicated, standalone program that guards you against each of these problems is wise.
Did you Know?
You don’t always need one program for each job. Most of the security software vendors listed in the previous list offer complete packages that do a better than adequate job of protecting you from all the dangers described in the earlier list. Using a single vendor and program means that you have to update the programs less often and there are fewer potential conflicts between the programs. Microsoft even offers Windows Live One Care, a security service that guards against the threats described earlier (www.microsoft.com).
Vista Requires Fewer Reboots
Another advantage to Vista’s internal, more secure architecture is that you should rarely have to reboot your computer. A system program you install that modifies the system, such as an antivirus program, should now be able to update all the necessary files without requiring you to reboot your system to complete the installation. It’s Microsoft’s goal to design Vista so that if a program requires a reboot of your computer to finish installing, you return to the same place you were when the reboot occurred. All your open programs and windows should be intact.
By the Way
Windows XP reduced the number of reboots required during program installation, but did not eliminate them. When updating some antivirus definitions, you might have found yourself rebooting more than once just to download and install all the day’s updates.
Perhaps not surprisingly, Microsoft sometimes updates your computer and requires a reboot. This often occurs when one or more Windows Vista system files currently in use have to be changed. In general, don’t expect program and folder windows that were open before the reboot and update to be open when Vista restarts. Sometimes inconsistencies are consistent with Microsoft.
Enjoy Safer Online Surfing
Although Chapter 36, “Combining Vista, Networks, and the Internet,” discusses Internet surfing while using Vista, you should know that Microsoft has tried to protect you not only from outside attacks that might infect your computer but also from yourself.
Don’t Be Phishing Bait
Some people create websites that look like other websites. They might, for example, create a web page that looks just like the sign-in page for eBay or a bank. The design of these sites is to fool you into entering your username and password. The sites store that information so that their owners have access to your account. These are phishing websites and Vista includes some antiphishing tools to protect you.
Every time you attempt to access a web page, if warranted, Internet Explorer displays the web address in a color indicating suspicion: yellow if Vista suspects the site of being a phishing location or red when the site you’re opening is a known phishing location. You’ll see the color in your web page’s address bar. Figure 27.2 shows a website that Vista suspects of being a phishing site and sure enough it is. Vista highlighted this faux-eBay web page with a yellow address at the top and displayed the pop-up warning box to let the user know that the site is extremely suspicious. Even though this looks like a valid eBay login screen, it’s not, as the lack of ebay.com URL in the web address verifies.
Figure 27.2. This looks like eBay, but it’s a phishing web page set up for the sole purpose of stealing eBay IDs and passwords.
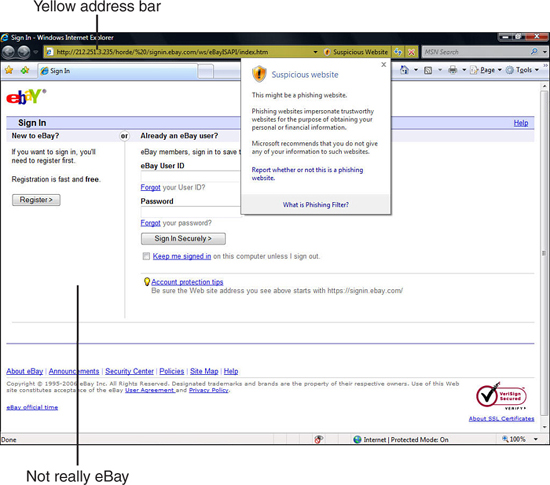
When the address is red, Internet Explorer is warning you that you’re looking at a known, invalid web page that is most likely a phishing site, so don’t enter any information there. When address is yellow, double-check the source of the address to ensure that it’s reliable.
Did you Know?
In general, banking, auction, and other sensitive financial and reliable websites will address you by your name or user ID to indicate they are legitimate when sending you emails with links to websites. They also rarely if ever ask you to provide confidential information.
Just keep an eye open for the colored address bar; if you see yellow or red, forewarned is forearmed.
Internet Explorer Blocks
Vista runs Internet Explorer in Protected Mode, which disallows much of the malware that can give you problems when you surf the Internet such as ActiveX controls (small programs that download and run) and download files that begin downloading when you click a button or a link that triggers them.
The problem today is that you’ll many times run across a valid website that needs to place an ActiveX control on your computer or perhaps you’ll want to download a program such as Adobe Acrobat Reader to read PDF files. When Internet Explorer blocks an activity, Vista displays a yellow ribbon called the information bar toward the top of your screen. You can right-click the information bar and select what you want Internet Explorer to do.
Figure 27.3 shows such a session. The user is attempting to download Adobe Acrobat Reader from the Adobe.com website. This program is a perfectly good program that you can download and install safely, and yet Internet Explorer stopped short of letting the program arrive without alerting you with an information bar.
Figure 27.3. Internet Explorer wants to make sure that you want to download a file.

Did you Know?
Vista beeps to help indicate that the information bar appeared, so it’s a good idea to keep your speakers turned up loud enough to hear system sounds. Without the beep, it’s easy to miss the information bar and not know what to do when you want to install an ActiveX control or download a file.
Right-clicking the information bar gives you options. You can agree to download the file, in which case Adobe continues sending the program to the computer and the Acrobat Reader installs. Clicking the What’s the Risk? option opens the Windows help screen, shown in Figure 27.4, which explains the purpose for the warning and why Vista requires that you confirm the download. Clicking More Information takes you to more-detailed Vista help screens that describe how you can achieve a safer Internet surfing experience.
Figure 27.4. Vista provides help that explains why it temporarily blocked you from downloading a file.

By the Way
Internet Explorer prompts you to confirm such a download whether you’re working from within an Administrator or a Standard user account. Your account level does not affect Internet Explorer’s operation.
Internet Explorer, although made by Microsoft, doesn’t discriminate. If you attempt to download and install an ActiveX control from Microsoft.com, the information bar pops up and does its job even though the source is valid. IE’s goal is to let you do whatever you want to do, but to make sure that you triggered the action intentionally.
Become Familiar with Control Panel’s Security Features
You don’t have to be a security expert to understand your Control Panel’s security-related groups shown in Figure 27.5. Chapter 24, “Controlling Windows Vista,” gives you an overview of Control Panel’s security groups if you want only a quick impression. But this is a good time to spend a few moments learning more about Vista’s security-related offerings; lots of people want to get into your files right now and you do not want to let them do so.
Figure 27.5. You can go a long way toward making your entire computing experience safer by visiting your Control Panel’s Security group.

Your computer connects to every other online computer in the world every time you check email and surf the Internet—and connects all the time if you subscribe to an always-on broadband connection such as DSL or a cable modem.
The Security Center, shown in Figure 27.5, works like a dashboard to give you a bird’s-eye view of your computer security status. Depending on what you find, you can explore other options in your Control Panel’s Security group. Each section, Firewall, Automatic Updating, Malware Protection, and Other Security Settings shows green if Windows sees at least some protection there, yellow if possible danger exists, and red if probable danger exists. Click the arrow to the right of each section name to expand that section and read more details.
In Figure 27.6, the user is running without virus protection. Although you cannot see color in this book’s figures, the group is yellow and not red because the user has no email account set up, so the lack of virus protection isn’t as critical as it would be with Outlook installed and running. If you connect to the Internet and you turn off your firewall, Vista will color the Firewall group red because you’re running naked without any protection from intruders.
Figure 27.6. The Security Center gives you an overview of your security status.

By the Way
As with most of Windows Vista, you can access many of the same security settings from different areas of Vista. For example, you can change Windows Update, Windows Firewall, Windows Defender, and your Internet option settings from the Security Center by clicking the links at the left of the screen.
Did you Know?
Click the Windows Security Center’s Change the Way Security Center Alerts Me option to display Figure 27.7’s Windows Security Center dialog box. In this box, you determine how you want Vista to warn you when you have a security problem: by displaying a pop-up icon and message, displaying just the icon, or keeping quiet until you elect to view your Security Center status. These days you cannot afford to be lax in your security, and choosing to see a pop-up icon and message the moment one of the four critical Windows Security Center’s elements is in danger is the best way to stay notified and safe.
Figure 27.7. Let Windows make you aware of security holes the moment they appear on your computer.

Stay Behind the Firewall
Windows Vista improved on Windows XP’s firewall because now the firewall monitors both inbound and outbound Internet traffic. (The XP firewall monitored only inbound traffic.) This means that if you do happen to get an infected program, perhaps from a friend’s CD-ROM that had a free game on it, that program cannot use your computer and Internet connection to do its bidding without first getting permission from you.
To access the firewall and its settings, open your Control Panel’s Security group and select the Windows Firewall option. A Windows Firewall status screen appears that contains much of the same information you saw at the Security Center in Figure 27.5. Clicking the Change Settings option opens the Windows Firewall Settings dialog box shown in Figure 27.8 (after you confirm that you want to open the dialog). There you can turn off your firewall if you suspect a program conflict with the firewall and want to check to see whether the firewall might be causing the problem.
Figure 27.8. You can control your firewall settings and even turn off your firewall temporarily.

Watch Out!
Obviously, if you have an always-on Internet connection, never leave your firewall turned off for more than a few moments.
You can click to check the Block All Incoming Connections option to stop all inbound Internet connections. If you want to connect to a network that isn’t secure (or that you’re unsure of), you can keep all Internet intrusion out of your computer while you work on that less-secure connection. For example, you want to connect your laptop to a network inside a conference room to share files with others, but you’re unsure whether the network you’re about to connect to has adequate protection on its inbound Internet traffic. You can keep all traffic (other than from the network itself) from getting through to your computer until you disconnect from the network and restore your laptop to its previous state that allowed inbound Internet traffic.
The Exceptions tab enables you to specify exceptions to the firewall. Generally, you should make changes to this dialog box page only if you’re familiar with computer communications. Vista usually makes the Exceptions settings when you perform other tasks. For example, when you elect to share files and a printer with others on a network, you’ll usually access this option from your Network window. Vista checks the firewall’s exceptions list File and Printer Sharing option when you request that sharing mode. Therefore, in general you won’t select or deselect options from the Exceptions tab.
Did you Know?
It helps to think of the Exceptions tab as you inform the Windows Firewall which programs and computer processes are to be let through the firewall without hesitation.
On the Advanced page, you’ll generally see at least one (and possibly more) network connection that you want Windows Firewall to monitor or not monitor. The assumed default is that you want Windows Firewall to monitor your network connections because they generally include Internet traffic coming to your machine from the network.
Watch Out!
The Windows Firewall is basic, but often that’s all the firewall protection you need. When a malicious hacker wants to enter a computer through its Internet connection, the hacker typically moves on to the next connection if there’s any kind of firewall. (In fact, most of the time, a good firewall prevents a potential hacker from even seeing your computer’s presence on the Internet.) So few connections are actually protected that finding one without a firewall isn’t too difficult, at least until more computer users understand the importance of protecting their systems. (The fact that Windows Vista and Windows XP SP2 turning on their firewalls by default will help to solve this problem as more and more people upgrade their computers.) Despite the fact that Windows Firewall is usually all the firewall protection you need, especially given Vista’s outgoing traffic monitoring feature, upgrading to a more robust firewall such as the one offered by Zone Labs (www.ZoneLabs.com) almost guarantees that you’ll never have an intrusion problem. So, keep your Vista firewall turned on until you’re able to upgrade to a more complete firewall solution to make extra sure that your Internet connection is safe.
Keep Your Computer Up to Date
One of the easiest ways to guard against the latest security threats that develop is to keep Windows Vista updated. When you click your Control Panel’s Security group, you’ll see the Windows Update option. Clicking that option produces the Windows Update window shown in Figure 27.9. Although Windows Update updates such programs as Internet Explorer and Media Player–related settings and add-ins, it also updates your system with any patches that might help prevent a security threat from entering your machine, whether that threat comes from a program you install or from the Internet.
Figure 27.9. Keep your computer’s system software up-to-date to guard against some of the latest threats.

Figure 27.9 shows that no critical updates are available, but one optional update is. Clicking the View Available Updates link describes what that update contains and enables you to select, download, and apply it. If the update relates to security, Windows does not call the update optional—it’s an update (or perhaps multiple updates) that you should install without hesitation.
Did you Know?
Many Microsoft products now update through the Windows Update system. If you have Microsoft Office installed, the Office programs will update when needed through your Windows Vista update system.
Clicking to select the Change Settings link opens the Change Settings window, shown in Figure 27.10, where you can select the frequency of Windows updates. A daily update setting, as shown in Figure 27.10, isn’t unreasonable as quickly as threats can attack these days. Setting updates to occur automatically at 3:00 a.m. or another time when you won’t be using your computer will keep your machine as up-to-date as possible.
Figure 27.10. You can determine when your computer has updates applied.

Did you Know?
Some users prefer to see all updates before they allow the updates to install. Clicking the Download Updates But Let Me Choose Whether to Install Them option ensures that all updates download according to the schedule you select (such as every day at 3:00 a.m.), but doesn’t apply them. An icon in your taskbar’s notification area indicates that the updates are ready to install. After you review the updates and want to proceed with one or more of them, check the updates you want to install and Windows applies them.
Watch Out!
It’s rare, but sometimes Microsoft releases an update that can cause unforeseen system problems. If you’re uncertain about an update or perhaps you’ve read that the update can cause problems (word gets around quickly on the Internet news and blog sites when an update goes badly), before installing that update you can save your system settings by using restore points as described in Chapter 31, “Restoring Your Windows System to a Previous State.” Most updates are supposed to create a restore point for you, but they don’t all seem to do so.
If the updates relate to your Vista system files, Vista might have to violate its own stated goals and require you to reboot your computer before the changes will take effect. In that case, a dialog box like the one shown in Figure 27.11 pops up from your taskbar. You can click Restart Now to reboot immediately, or select a time for a reminder and click the Postpone button.
Figure 27.11. Vista sometimes needs to reboot before it can apply a system update.

Let Windows Defender Help Protect Your Files
Vista includes a new security program named Windows Defender. Windows Defender’s job is to scan files that you retrieve through Internet Explorer and elsewhere and try to ensure that the files are spyware-free. This means that Windows Defender scans files on your computer and looks at them to see whether they fit the pattern of a malicious file that might destroy something or fill your screen with ads that are difficult to get rid of as some programs can do. (Others send Internet Explorer off to advertising websites.) Windows Defender, whose window is available from your Control Panel’s Security group, offers the following kinds of protection:
- Real-time protection—Continually monitors your computer and watches all program installations and system settings, and alerts you if an unexpected and possibly malicious action could result from the program.
- SpyNet community ratings—You can elect to join SpyNet, a group of other Vista users who have agreed to participate. Each time a SpyNet user accepts or rejects a program due to possible malware involvement, SpyNet records that activity. If the same program threatens you, you can see what others have done in the SpyNet community to determine whether it’s safe to install the program.
Watch Out!
Just because lots of other users have agreed to install the program doesn’t necessarily mean that you can safely install it, although the SpyNet community’s decisions are guides for you to consider. You might also be working when a certain problem just became known and very few if any in the SpyNet community have faced the potential threat, so your decision to accept or reject the program can affect what others do. Generally, if the program is from a known source, especially from a major software vendor, you can safely install any program Windows Defender warns you about.
- Scheduled and manual system scans—You can schedule, or manually request at any time, a complete Windows Defender scan of all your files. Windows Defender then sets off to the task of analyzing every file on your computer looking to see whether spyware has infected anything.
Windows Defender looks at each program installation—whether that program is installed by you, through the Internet (perhaps as an ActiveX control), or perhaps through a link or button you clicked in an email—and looks for a known pattern of actions cause it enough concern to warn you about.
By the Way
Spyware changes frequently and new kinds of attacks crop up. When you perform a Windows Update, Windows Defender’s database of known problems often updates as well to ensure that you have the latest monitoring system.
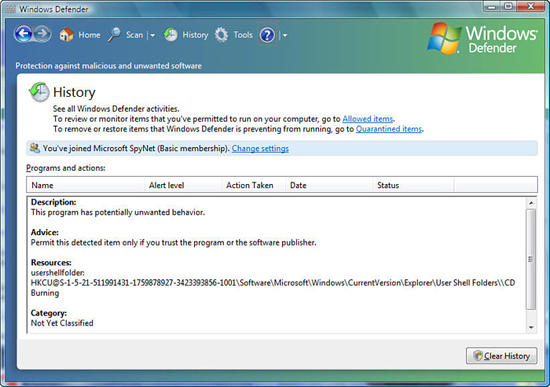
When you open the Windows Defender window, you’ll likely see that you system is fine because Windows Defender is always working in the background to let you know about potential threats. You can click the History button to see when Windows Defender warned you about a potential security threat such as the warning shown in Figure 27.12. The history shows the potential offending program and location, as well as the description and advice Windows Defender gave you when you or something you did triggered this program’s installation.
Figure 27.12. Windows Defender shows you a history of problems it spotted as potentially threatening to your system.
Clicking the Tools button produces a screen where you can change Windows Defender’s settings. Settings include scheduling Windows Defender to perform a full system check weekly, updating your membership in the SpyNet community, and viewing quarantined items (which are programs Windows Defender prevented from running on your computer). Others involve the allowed items that Windows Defender permits to run, or provide quick access to the Windows Defender website, where you can learn more about Windows Defender’s operation.
Did you Know?
If you allow Windows Defender to run a program but then realize you should not, you can stop the program from running in the future (assuming that the program hasn’t done any damage) by opening the Windows Defender Tools window and clicking Allowed Items to display the window in Figure 27.13. Click to select the offending program and click Disable to quarantine that program to keep it from running until you allow it or click Remove to remove the program from your machine altogether.
Figure 27.13. You can change your mind and quarantine or remove programs you allowed to run in the past.

By the Way
You might wonder what happens if you allow spyware to run when you shouldn’t. The worst thing that can happen is that the program can destroy your data. Often, however, spyware performs less destructive tasks such as monitoring your computer activities and sending reports to an advertising website that sends you targeted, pop-up ads. Disabling or removing such spyware makes your system run smoother and causes fewer interruptions for you.
Parental Controls
Microsoft designed Vista’s parental controls so that parents can monitor and limit what their children see through the computer. With the parental controls, you can do the following:
- Restrict the running of certain programs to certain users.
- Monitor a user’s computer usage and view activity reports that list websites visited, blocked websites that were attempted to be viewed, files downloaded, programs run, games played, email sent, instant messages sent and received, and media-related event logs that show what music and DVDs were played (assuming that the title data was available).
- Restrict web surfing and downloads to limit the amount of mature content, drugs, and so forth. Not all websites make it clear to the parental control features what they’re all about, so accurate web restriction is not usually possible 100% of the time. Parents concerned about web content should allow their children to surf the Web only when adults are present.
- Limit computer usage on a user account basis, as you might do to allow a user to use the computer for two hours on a Saturday morning.
- Control games by rating, content, or title (when possible).
- Allow or block certain programs on the computer from running from the user’s account.
By the Way
Modern computer games have ratings that use a system similar to motion picture ratings. Vista can detect those ratings and allow or disallow the program based on the parental controls that you set.
Watch Out!
Some games, including almost all games published before 2002, don’t have such ratings, so you have to specify your parental controls by title or content. Even then you might not be able to control older games because they might not display enough information for Vista to recognize them. In addition, the parental controls options cannot control games installed on a FAT partition (file access table; that is, a disk drive formatted under an older Windows file system).
To access the parental controls, open your Control Panel’s Security group and select Parental Controls to display a list of users. Select a user to display Figure 27.14’s Parental Controls window. The Parental Controls window is also available from within the User Accounts and Family Safety Control Panel group.
Figure 27.14. Set parental controls on game ratings, monitor computer activities, and restrict computer usage with Vista’s parental controls.

Watch Out!
If an Administrator user account exists but has no password assigned to it, any Standard user account can perform any Administrator-level task. For the Parental Controls window options to have any teeth, all your Administrator user accounts must have passwords.
To restrict or allow certain access, click the appropriate link on the Parental Controls window. For example, clicking the Game Ratings screen controls which games the user can run. Clicking the Set Game Ratings link opens a ratings window. Ratings range from EC—Early Childhood to AO—Adults Only, so you can set the highest rating allowed for a particular account.
By the Way
By its very nature, an Administrator user account must have full access to the entire computer and all its settings. Therefore, you can restrict access only to Standard user accounts.
BitLocker Secures Hard Disks
Windows Vista’s BitLocker feature encrypts your disk drive and all its contents with a 48-digit encryption code. When you encrypt a disk drive with a BitLocker encryption key, you will be able to use the disk drive as long as you enter the proper key but nobody else will be able to use the computer.
Watch Out!
BitLocker does not encrypt the individual files you specify; instead, it encrypts the entire disk drive. The Encryption File System is useful for encrypting individual files for those who use the Windows Vista Enterprise, Vista Business, Vista Ultimate versions. However, they can encrypt only files located on their Windows drive (this is usually drive C), not on another drive attached to the computer.
When you use BitLocker on your desktop or laptop’s disk drive, the disk drive becomes incapable of being read by anyone who removes the drive from your computer and attempts to access your files from another computer. BitLocker also keeps encrypted any files that you send to others over a network, although the recipients can decrypt the files if you tell them the key you used to encrypt the data. By blocking such data, you ensure that snoopers who gain access to your computer over the Internet cannot read anything from any file on your computer, including system files that security threats could corrupt.
To use your computer, you either type your encryption key when you first boot the machine or store the key on a USB drive that you insert to boot your computer and then remove when you’re finished. If someone steals your laptop, they cannot access any data on it without the key. You turn on BitLocker from your Control Panel’s BitLocker Drive Encryption group.
Watch Out!
BitLocker technology can be problematic for the average user, which is why Microsoft chose not to include the feature in lower-end Vista installations, including Vista Home Premium. Several factors in BitLocker can cause the computer to be unbootable. In addition, managing BitLocker settings and keeping a BitLocker computer running properly requires extra work to protect the encryption and to keep the hardware running smoothly.
Not all hardware that works with Vista is BitLocker-compatible. If yours is not, you will see a window, like the one shown in Figure 27.15, indicating that your computer does not contain a TPM (trusted platform module). A TPM is what enables the machine to interact with USB drives and connect key encryptions to the machine’s disk drives.
Figure 27.15. You must have appropriate hardware before you can apply a BitLocker encryption key to a disk drive on your computer.

Although the primary focus of this book is on home and small business users who will probably be using Vista Home Premium, you need to know about BitLocker to round out your knowledge of Vista’s security offerings in case you have a need for such data protection and security. Know that the risks and management of a BitLocker system can become a nuisance but, of course, such nuisances are minor when data is critical.
Did you Know?
If you run one of the Vista Home operating systems and feel you need BitLocker protection, display your Windows Start menu, select Extras and Upgrades, and upgrade your Vista installation to a higher version to allow for the BitLocker technology. You should first check your hardware settings to ensure that you have a system that permits BitLocker. The following website contains detailed information to help you decide whether BitLocker technology is right for your needs: http://www.microsoft.com/technet/windowsvista/security/bitexec.mspx.
Chapter Wrap-Up
You now have no reason to be infected with malicious computer threats ever again! Oh, if only that were true! The reality is that no matter how diligent you are and no matter how much forethought Microsoft put into Vista’s security, new threats are dreamed up every day that were never before thought of. You must stay updated, you must keep your security-related software installed and active, and you probably should augment your Vista security software with a purchased security suite to increase the likelihood that you’ll survive whatever comes your way.
Despite the huge number of security threats that can take down your computer, the world is full of countless programs that help you get your work done and enjoy your computer. The next chapter tells you what you need to know to install and remove programs properly.
