We will cover the steps to create an API gateway API and integrate Cognito Authorizer with it, as follows:
- Create an API gateway REST API, as follows:
aws apigateway create-rest-api
--name "API Gateway With Cognito"
--region us-east-1
--profile admin
- Call get-resources to get the root resource ID, as follows:
aws apigateway get-resources
--rest-api-id 3t0t98ifdh
--region us-east-1
--profile admin
- Create a resource with the path greeting and the parent ID as the ID of the root resource:
aws apigateway create-resource
--rest-api-id 3t0t98ifdh
--region us-east-1
--parent-id ufgvoiu8yh
--path-part greeting
--profile admin
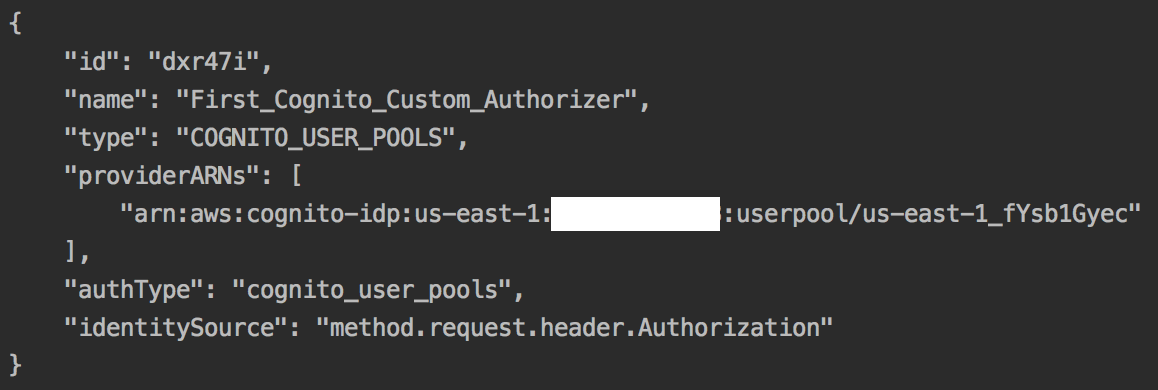
- Create an authorizer for API gateway, of the type COGNITO_USER_POOLS, as follows:
aws apigateway create-authorizer
--rest-api-id 3t0t98ifdh
--name First_Cognito_Custom_Authorizer
--type COGNITO_USER_POOLS
--provider-arns arn:aws:cognito-idp:us-east-1:<account id>:userpool/us-east-1_fYsb1Gyec
--identity-source method.request.header.Authorization
--profile admin
Replace the user pool ID (us-east-1_fYsb1Gyec) with your user pool ID, and account id with your account ID.
If this is successful, you should get the following response:
- Execute the put-method sub-command, with the authorization-type as COGNITO_USER_POOLS and the authorizer-id received as the response to the create-authorizer command, as follows:
aws apigateway put-method
--rest-api-id 3t0t98ifdh
--resource-id rebvv7
--http-method GET
--authorization-type COGNITO_USER_POOLS
--authorizer-id dxr47i
--region us-east-1
--profile admin
- Execute the put-method-response sub-command:
aws apigateway put-method-response
--rest-api-id 3t0t98ifdh
--resource-id rebvv7
--http-method GET
--status-code 200
--region us-east-1
--profile admin
- Execute the put-integration sub-command:
aws apigateway put-integration
--rest-api-id 3t0t98ifdh
--resource-id rebvv7
--http-method GET
--type MOCK
--integration-http-method GET
--request-templates '{"application/json": "{"statusCode": 200}" }'
--region us-east-1
--profile admin
- Execute the put-integration-response sub-command:
aws apigateway put-integration-response
--rest-api-id 3t0t98ifdh
--resource-id b0549c
--http-method GET
--status-code 200
--selection-pattern ""
--response-templates '{"application/json": "{"message": "Welcome $context.authorizer.claims.given_name"}"}'
--region us-east-1
--profile admin
We use $context.authorizer.claims.given_name to retrieve the user attribute given_name that was used when creating the user. The sub-commands put-method, put-method-response, put-integration, and put-integration-response are simplified into a single block within the CloudFormation template for creating the API. In any case, CloudFormation templates are the preferred way to provision resources in AWS programmatically. I have included the CLI commands for a better understanding of the CloudFormation templates.
- Create the deployment, as follows:
aws apigateway create-deployment
--rest-api-id 3t0t98ifdh
--region us-east-1
--stage-name dev
--stage-description "Dev stage"
--description "First deployment"
--profile admin
A sample URL for this deployment will look as follows: https://3t0t98ifdh.execute-api.us-east-1.amazonaws.com/dev/greeting
- Create the user pool client, as follows:
aws cognito-idp create-user-pool-client
--user-pool-id us-east-1_fYsb1Gyec
--client-name my-user-pool-client
--explicit-auth-flows USER_PASSWORD_AUTH
--profile admin
- Create a user sign-up, as follows:
aws cognito-idp sign-up
--client-id 45l9ureterrdqt0drbphk4q3pd
--username testuser5
--password Passw0rd$
--user-attributes Name=given_name,Value=Heartin
- Confirm the user as an administrator, as follows:
aws cognito-idp admin-confirm-sign-up
--user-pool-id us-east-1_fYsb1Gyec
--username testuser5
--profile admin
- Do an initiate-auth API call with the auth flow as USER_PASSWORD_AUTH, to allow for simple authentication based on username and password:
aws cognito-idp initiate-auth
--client-id 45l9ureterrdqt0drbphk4q3pd
--auth-flow USER_PASSWORD_AUTH
--auth-parameters USERNAME=testuser5,PASSWORD=Passw0rd$
If it is successful, this command will return the access token, ID token, and refresh token.
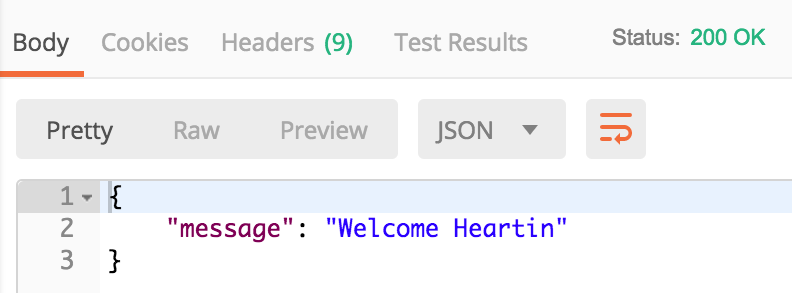
- Finally, you can execute the URL by using a REST client, such as Postman. You need to select the authorization type as Bearer Token and copy the ID token value that you received in the initiate-auth request into the token field, as follows:

If it is successful, you should get the following results: