Installing Active Directory and DNS has always been fairly straightforward. You can always use Server Manager, but using PowerShell is really quite simple.
This recipe starts with two non-domain joined hosts, DC1 and DC2. Each host is running Windows Server 2019 with no tools loaded. After creating the initial forest and forest root server (DC1), you convert DC2 to be another domain controller that also runs DNS.
- On
DC1, install the AD Domain Services feature and the associated management tools:Install-WindowsFeature AD-Domain-Services -IncludeManagementTools
- Install
DC1as the forest root domain controller in theDC1.Reskit.Orgforest:$PSSHT = @{ String = 'Pa$$w0rd' AsPlainText = $true Force = $true } $PSS = ConvertTo-SecureString @PSSHT $ADHT = @{ DomainName = 'Reskit.Org' SafeModeAdministratorPassword = $PSS InstallDNS = $true DomainMode = 'WinThreshold' ForestMode = 'WinThreshold' Force = $true NoRebootOnCompletion = $true } Install-ADDSForest @ADHT - Restart the
DC1computer:Restart-Computer -Force
- After rebooting, log back in to
DC1asReskitAdministrator, then view theRootDSEentry onDC1:Get-ADRootDSE | Format-Table -Property DNS*, *Functionality
The next part of this recipe runs on DC2. Based on the previous steps, DC1 is now a domain controller. DC2 begins as a workgroup server with no additional roles/features added:
- Log on to
DC2and check thatDC1can be resolved and can be reached over445and389fromDC2:Resolve-DnsName -Name DC1.Reskit.Org -Server DC1 -Type A Test-NetConnection -ComputerName DC1.Reskit.Org -Port 445 Test-NetConnection -ComputerName DC1.Reskit.Org -Port 389
- Add the AD DS features to
DC2:$Features = 'AD-Domain-Services', 'DNS','RSAT-DHCP', 'Web-Mgmt-Tools' Install-WindowsFeature -Name $Features - Promote
DC2to be an additional domain controller in theReskit.Orgdomain:$URK = "[email protected]" $PSSHT = @{ String = 'Pa$$w0rd' AsPlainText = $true Force = $true } $PSS = ConvertTo-SecureString @pssht $CREDHT = @{ Typename = 'System.Management.Automation.PSCredential' ArgumentList = "$URK,$PSS" } $CredRK = New-Object @CREDHT $IHT =@{ DomainName = 'Reskit.org' SafeModeAdministratorPassword = $PSS SiteName = 'Default-First-Site-Name' NoRebootOnCompletion = $true Force = $true } Install-ADDSDomainController @IHT -Credential $CredRK
- Reboot the
DC2host:Restart-Computer -Force
- After rebooting, log on to
DC1and view the forest:Get-AdForest | Format-Table -Property *master*,global*,Domains
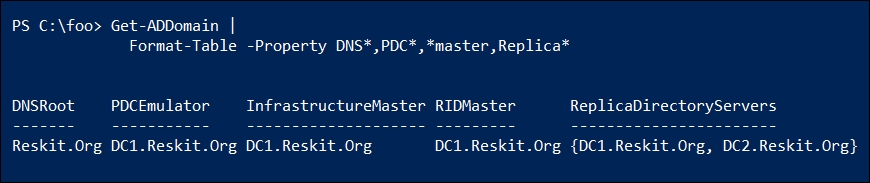
- View the details of the
Reskit.Orgdomain:Get-ADDomain | Format-Table -Property DNS*,PDC*,*Master,Replica*
In step 1, you install the AD Domain Services feature and the management tools (the PowerShell module and AD-related MMC consoles), which looks like this:

In step 2, you install DC1 as the forest root domain controller, which looks like this:

This step generates several warning messages. In this case, these warnings are benign and you can ignore them. After the DC promotion has completed, in step 3, you reboot the host. This generates no console output. Once you have rebooted DC1, in step 4, after you log on to DC1, you examine the RootDSE, which looks like this:

In step 5, after logging in to DC2, you check to ensure that you can resolve the IP address for DC1 from DC2 and that you can reach the other DC over ports 445 and 389. If these checks fail, promoting DC2 to be a domain controller is also going to fail. The output of this step looks like this:
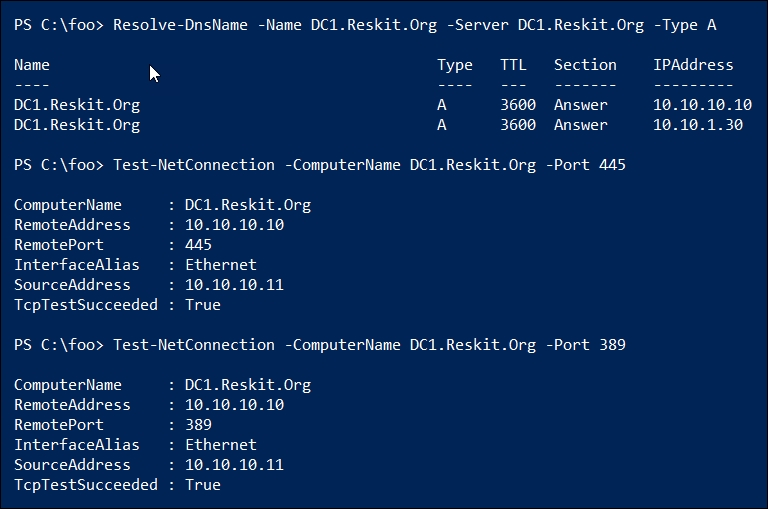
These tests show that DC2 can contact DC1 over key ports, so should be capable of being promoted to be a domain controller. In step 6, you add the ADDS features to DC2, as you did earlier for DC1. The output of this step looks like this:

In this step, you add some additional tools, including the RSAT DHCP tools. You have options as to how much you add at each point. In this case, you need the AD-Domain-Services and DNS Services features, whilst the others are optional.
With connectivity tests succeeding and the pre-requisites installed, in step 7, you promote DC2 to be another domain controller in the Reskit.Org domain, like this:

After completing the installation of DC2 as a domain controller, in step 8, you reboot the host which produces no output.
After DC2 has completed rebooting in step 9, log in and examine aspects of the Reskit.Org forest, like this:

In the final step, step 10, you examine details about the Reskit.Org domain, like this:
In step 2, you create DC1 as the first domain controller in the Reskit.Org forest. After the installation process completes, you must reboot DC1 before it can function as a DC, which you do in step 3.
In step 4, you examine the Root Directory Server Agent Service Entry or RootDSE in your domain. This entry, which is part of the LDAP standard as defined in RFC 2251 Section 3.4, enables an LDAP server to provide information about the capabilities of that server and the data that it contains to other LDAP servers and clients. This information is available without requiring any authentication. For more details on the RootDSE object and its attributes, see: https://docs.microsoft.com/en-us/windows/desktop/adschema/rootdse.
In step 5, you checked for connectivity on ports 445 and 389. With Windows Server 2019, port 445 is used for SMB file sharing, while port 389 is the port for LDAP. Domain-joined systems need access to these ports to access the domain controller for group policy details.
After completing the installation of AD on DC2, you need to reboot DC2, after which DC2 is a second domain controller in the Reskit.Org domain and is also a DNS server.
