If you host multiple secure servers at the internet scale, you may find that certificate management can be challenging. Each time you add a new IIS host into your infrastructure, you need to ensure that all of the correct certificates are in place on that host and the correct web binding (binding the certificates to IIS) is in place for each secure site. To add to the workload, you need to deal with certificate expiration and the renewal of certificates across each IIS server that utilizes those certificates.
Windows 2019 includes a feature, the Central Certificate Store (CCS), that simplifies managing certificates. With CCS, you store certificates in a central location, such as on an SMB file share, and use IIS to load certificates from the central CCS share.
In this recipe, you configure SRV1 to use a new share on DC1, which holds the CCS SMB share. You create the certificate store, create a new certificate for SRV1, and move that certificate to the central certificate share on DC1. You then configure IIS to make use of the central store, rather than using the local certificate stores, like you did in the Configuring IIS for SSL recipe.
This recipe uses two servers: SRV1 is an IIS server and DC1 is configured to hold the SSL CCS. You should have both servers up and running. Also, this recipe assumes that you have IIS at least partly loaded and set up for SSL (in other words, you should have run the Install IIS and Configure IIS for SSL recipes in advance). This recipe does check and ensure that the needed features are added to SRV1. You should also ensure that the Active Directory (AD) cmdlets are loaded on SRV1.
- Remove the existing certificates from
SRV1:Get-ChildItem Cert:localmachineMy | Where-Object Subject -Match 'SRV1.Reskit.Org' | Remove-Item -ErrorAction SilentlyContinue Get-ChildItem Cert:localmachine oot | Where-Object Subject -match 'SRV1.Reskit.Org' | Remove-Item - Remove SSL web bindings, if any exist:
Import-Module -Name WebAdministration Get-WebBinding | Where-Object protocol -EQ 'https' | Remove-WebBinding Get-ChildItem IIS:SslBindings | Where-Object Port -eq 443 | Remove-Item - Create a shared folder and share it on
DC1:$SB = { If ( -NOT (Test-Path c:SSLCerts)) { New-Item -Path c:SSLCerts -ItemType Directory | Out-Null} $SHAREHT= @{ Name = 'SSLCertShare' Path = 'C:SSLCerts' FullAccess = 'Everyone' Description = 'SSL Certificate Share' } New-SmbShare @SHAREHT 'SSL Cert Share' | Out-File C:SSLCertsReadme.Txt } Invoke-Command -ScriptBlock $SB -ComputerName DC1 | Out-Null - Check the share on
DC1:New-SmbMapping -LocalPath X: -RemotePath \DC1SSLCertShare | Out-Null Get-ChildItem -Path X: - Add new SSL certificates to the root certificate store on
SRV1:$SSLHT = @{ CertStoreLocation = 'CERT:LocalMachineMY' DnsName = 'SRV1.Reskit.Org' } $SSLCert = New-SelfSignedCertificate @SSLHT $C = 'System.Security.Cryptography.X509Certificates.X509Store' $NOHT = @{ TypeName = $C ArgumentList = 'Root','LocalMachine' } $Store = New-Object @NOHT $Store.Open('ReadWrite') $Store.Add($SSLcert) $Store.Close() - Export the certificate to a PFX file:
$CertPW = 'SSLCerts101!' $SSHT = @{ String = $CertPW Force = $true AsPlainText = $True } $Certpwss = ConvertTo-SecureString @SSHT $CertHT = @{ Cert = $SSLCert FilePath = 'C:SRV1.Reskit.Org.pfx' Password = $Certpwss } Export-PfxCertificate @CertHT - Move the certificate to the
SSLCertShareshare onDC1:$MHT = @{ Path = 'C:SRV1.Reskit.Org.pfx' Destination = '\DC1SSLCertShareSRV1.Reskit.Org.Pfx' Force = $True } Move-Item @MHT - Install the CCS feature on
SRV1:Install-WindowsFeature Web-CertProvider | Out-Null
- Create a new user for the certificate sharing:
$User = 'ReskitSSLCertShare' $Password = 'Pa$$w0rd' $SSHT2 = @{ String = $Password AsPlainText = $true $Force = $True } $PSS = ConvertTo-SecureString @SSHT2 $NewUserHT = @{ AccountPassword = $PSS Enabled = $true PasswordNeverExpires = $true ChangePasswordAtLogon = $false SamAccountName = 'SSLCertShare' UserPrincipalName = '[email protected]' Name = 'SSLCertShare' DisplayName = 'SSL Cert Share User' } New-ADUser @NewUserHT - Configure the SSL CSS in the registry:
$IPHT = @{ Path = 'HKLM:SOFTWAREMicrosoftIISCentralCertProvider' Name = 'Enabled' Value = 1 } Set-ItemProperty @IPHT $IPHT.Name = 'CertStoreLocation' $IPHT.Value = '\DC1SSLCertShare' Set-ItemProperty @IPHT - Enable the SSL CCS, as follows:
$WCHT = @{ CertStoreLocation = '\DC1SSLCertShare' UserName = $User Password = $Password PrivateKeyPassword = $Certpw } Enable-WebCentralCertProvider @WCHT $CPHT = @{ UserName = 'ReskitSSLCertShare' Password = $Password PrivateKeyPassword = $Certpw } Set-WebCentralCertProvider @CPHT - Set up SSL for a default site:
New-WebBinding -Name 'Default Web Site' -Protocol https -Port 443 $SslCert | New-Item -Path IIS:SslBindings�.0.0.0!443
- Remove the certificate from
SRV1:Get-ChildItem Cert:LocalMachineMy | Where-Object Subject -Match 'SRV1.RESKIT.ORG' | Remove-Item -Force - Now, view the website with SSL, as follows:
$IE = New-Object -ComObject InterNetExplorer.Application $URL = 'HTTPS://SRV1.Reskit.Org/' $IE.Navigate2($URL) $IE.Visible = $true
In step 1, you remove all certificates from the LocalMachine's MY certificate store. In step 2, you remove any SSL bindings for SRV1. In step 3, you create a new folder to hold centrally provided certificates, and share it on DC1. These three steps produce no output.
In step 4, you check the contents of the \DC1SSLCertShare share, which looks like this:
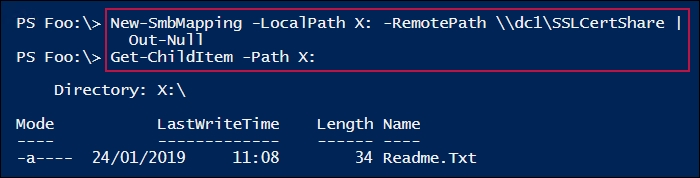
In step 5, you create a self-signed certificate in the LocalMachineMY certificate store. This certificate is then copied into the LocalMachineRoot certificate share. This step produces no output.
In step 6, you export the newly created self-signed certificate to a PFX file, which looks like this:

In step 7, you move the PFX file containing the certificate to the SSLCertShare share on DC1. In step 8, you install the Web-CertProvider feature to SRV1. In step 9, you create a new user in the AD for certificate sharing. In step 10, you configure the SSL CCS in the registry on SRV1. Then, in step 11, you enable the SSL CCS. These five steps produce no output.
In step 12, you set an initial web binding, which looks like this:

With step 13, you remove the certificate from the local certificate store, producing no output. Finally, in step 14, you use Internet Explorer to navigate to the default website on SRV1 using HTTPS:, which looks like this:
In step 5, you created a self-signed certificate in the LocalMachineMY certificate store; then, you copied this certificate into the LocalMachineRoot certificate share. The copy operation has the effect of making SRV1 trust the newly created certificate. In production, you would create a certificate from a trusted Certificate Authority and avoid copying the certificate (since the system would already trust that CA).
