Every Windows printer has a discretionary access control list (ACL). The ACL contains one or more access control entries (ACEs). Each ACE defines a specific permission for some specific group or user. You could define a group (such as SalesAdmins) and give that group the permission to manage documents, while you give another group (Sales) access to print to the printer.
By default, when you create a printer, Windows adds some ACEs to the printer's ACL. This includes giving the Everyone group the permission to print to the printer. For some printers, this may not be appropriate. For this reason, you may need to adjust the ACL, as shown in this recipe.
The PrintManagement module contains a number of cmdlets that help you manage the printers; there are no cmdlets for managing ACLs on printers. You can always use .NET directly to manage the ACL, or you can use a third-party script that does the job for you. But the code for that is complex (and easy to mess up). For simplicity in this case, you're going to download and use a script, Set-PrintPermissions.ps1, available on TechNet.
The SetPrintPermissions.ps1 script enables you to grant or deny printer permissions to AD users or groups. In this recipe, you use this script to remove the permission for members of the everyone group, then enable print, document, and print management to members of a different group. The script uses permission names that are familiar to IT pros, making this script easy to adapt.
A downside to this script is that there's no feature in the script to display the permissions on a printer object. You can always use .NET security classes to delve into the permissions, or (as you do in this recipe) just use the GUI to verify the actual permissions.
Note
During the development of Windows Server 2019, printers that are created with the recipes in this chapter have some interesting ACEs set. One ACE is set with an SID that relates to the SID that belongs to 'defaultuser0'. To avoid confusion, the graphics in the How it works… section don't show these ACEs.
This recipe uses AD accounts to set permissions based on the Create-SalesGroup.ps1 script . You need the PSRV print server and the DC1 domain controller. To test the permissions, you can use CL1.
- Download the
Set-PrinterPermissions.ps1script:$URL = 'https://gallery.technet.microsoft.com/scriptcenter/' + 'Modify-Printer-Permissions-149ae172/file/116651/1/' + 'Set-PrinterPermissions.ps1' $Target = 'C:FooSet-PrinterPermissions.ps1' Start-BitsTransfer -Source $URL -Destination $Target - Get help on the script:
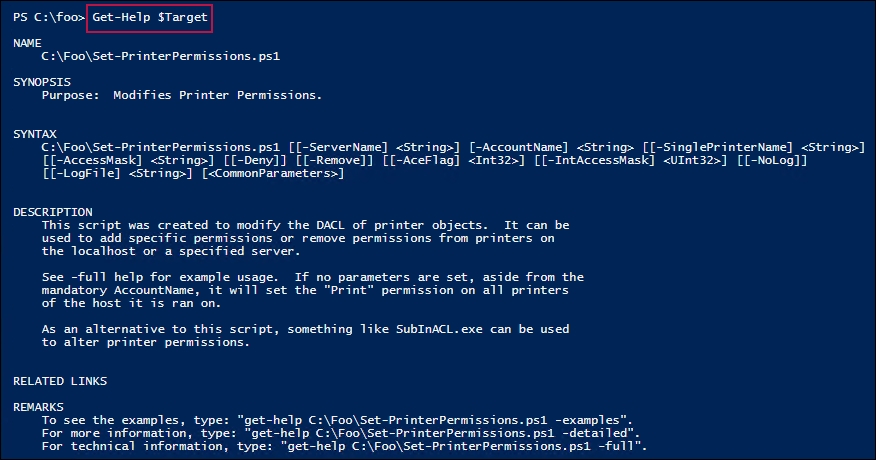
Get-Help $Target
- Use
PrintUI.DLLto bring up the printer properties GUI:rundll32.exe printui.dll,PrintUIEntry /p /nSalesprinter1
- From the GUI, click on Security to view the initial ACL.
- Remove the
EveryoneACE from the ACL forSalesPrinter1:$SPHT1 = @{ ServerName = 'PSRV' Remove = $True AccountName = 'EVERYONE' SinglePrinterName = 'SalesPrinter1' } C:fooSet-PrinterPermissions.ps1 @SPHT1 - Enable the members of the
Salesgroup to print to this printer:$SPHT2 = @{ ServerName = 'PSRV' AccountName = 'ReskitSales' AccessMask = 'Print' SinglePrinterName = 'SalesPrinter1' } C:fooSet-PrinterPermissions.ps1 @SPHT2 - Give
SalesAdminspermission to manage the documents:$SPHT3 = @{ ServerName = 'PSRV' AccountName = 'ReskitSalesAdmins' AccessMask = 'ManageDocuments' SinglePrinterName = 'SalesPrinter1' } C:fooSet-PrinterPermissions.ps1 @SPHT3 - Bring up the Printer GUI:
rundll32.exe printui.dll,PrintUIEntry /p /nSalesprinter1
- Click the Security tab and view the updated ACL.
In step 1, you used the BITS service to download the Set-PrinterPermissions script. This step generates no output.
The Set-PrinterPermissions script has comment-based help, which provides usage assistance. In step 2, you used Get-Help to view the basic help information, which looks like this:
In step 3, you used PrintUI.DLL to bring up the properties of the Salesprinter1 printer. In step 4, you viewed the initial ACL for the printer, which looks like this:

In step 5, you used the Set-Printerpermissions script to remove the default ACE, allowing everyone to print to the printer. In step 6, you enabled the members of the sales group to print to the printer, and in step 7, you enabled the members of the sales admins group to manage the printer. These steps produced no output to the console.
In step 8, you printed the printer UI to view the updated ACL, which looks like this:
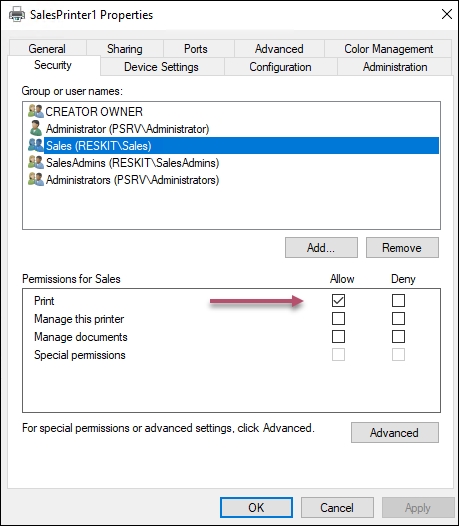
If you click on Sales, you can see their permissions, like this:

In step 1, you used the BITS service to download the Set-PrinterPermissions script using the URL of the script. Alternatively, you could have used your search engine and downloaded it directly. The script isn't available on PowerShell Gallery.
In step 3 and step 8, you used PrintUI.DLL to display a print-management GUI from which you can view the updated ACL for this printer. As you can see, the members of the Sales group are able to print, and members of the SalesAdmins group can manage the printer.
