One area of concern for responders is the use of Full Disk Encryption (FDE). Windows system administrators are likely to be familiar with FDE tools such as BitLocker, which is now part of the Windows OS. Outside of that, there are a number of tools such as VeraCrypt that allow users to encrypt individual files all the way to entire volumes. As part of the acquisition process, responders should check for any encryption.
Tools such as Endpoint Disk Detector from Magnet Forensics determine whether there are any encrypted volumes. This tool, available for free at https://www.magnetforensics.com/resources/encrypted-disk-detector/, can determine what, if any, encryption is being used. Simply running the executable as administrator starts the application. The following data is then presented:
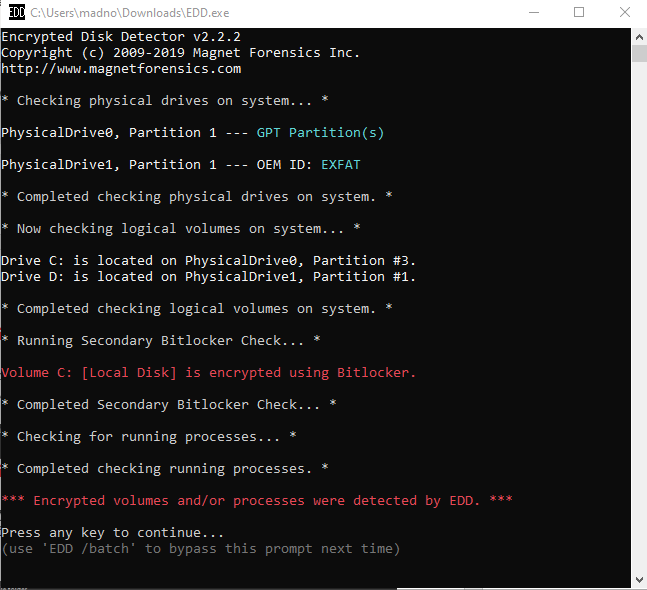
By doing this, the responder has determined that Volume C is encrypted using BitLocker. As a check, the responder should ensure that the appropriate BitLocker key is available if necessary. If an encryption key cannot be obtained, then the responder should acquire the logical volume while the system is still running.
