In order to conduct a proper examination of log files and other network data such as packet captures, they often have to be moved from the log source and examined offline. As with any source of evidence, log files or packet captures have to be handled with due care to ensure that they are not corrupted or modified during the transfer. One simple solution is to transfer the evidence immediately to a USB drive or similar removable medium. From there, a hash can be created for the evidence prior to any examination.
The acquisition of network evidence such as a packet capture or log file should be thoroughly documented. Incident response personnel may be acquiring log files and packet captures from a number of sources over the entire network. As a result, they should ensure that they can trace back every separate piece of evidence to its source as well as the date and time that the evidence was collected. This can be recorded in a network evidence log sheet and entries can be completed for each piece of evidence. For example, the following is a sheet with an entry:
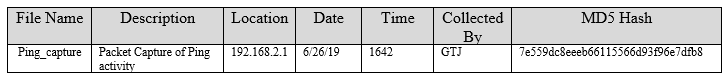
The log entry captures the following necessary information:
- File Name: Each log file or packet capture should have its own unique name. Within the procedures in use by the CSIRT, there should be a naming convention for different types of evidence file.
- Description: A brief description of the file. There does not need to be too much detail unless it is a unique file and a detailed description is called for.
- Location: The location is important. In this case, the packet capture was obtained on the switch located at 192.168.2.1.
- Date and Time: Record the date and time the file was transferred to the medium.
- Collected By: Initials are sufficient for the log file.
- MD5 Hash: A comprehensive overview of hashing will be covered in later chapters. For now, suffice it to say that a hash is a one-way algorithm that is utilized to provide a digital fingerprint for a file. This hash will be recorded at the collection phase and after analysis to demonstrate that the file was not modified during the analysis phase. There are several ways to compute the hash. In this case, the MD5 hash can be computed using the installed hashing program: md5sum on Ubuntu. md5sum has several different options that can be accessed via the command line. For the help menu, type the following:
dfir@ubuntu:~$md5sum --help
That produces the following help menu:

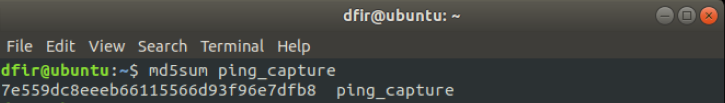
The MD5 hash can be calculated for the packet capture from the switch by simply entering the following command:
dfir@ubuntu:~$md5sum ping_capture
This produces the following output:
Log files and packet captures should be transferred to a storage device as soon as possible. Once the collection is complete, a chain of custody form should also be filled out for the external medium that contains the evidence files. From here, the files can be analyzed.
