Two integrated tools that allow leveraging threat intelligence during an incident are Yara and Loki. Yara is often referred to as the Swiss Army Knife of pattern matching. It was created to assist malware researchers with classifying malware. Through the use of Boolean expressions and strings, a malware sample can be classified.
For example, the Yara rule (https://github.com/Yara-Rules/rules/blob/master/malware/APT_Cobalt.yar) for a variation of the Cobalt Strike looks like this:
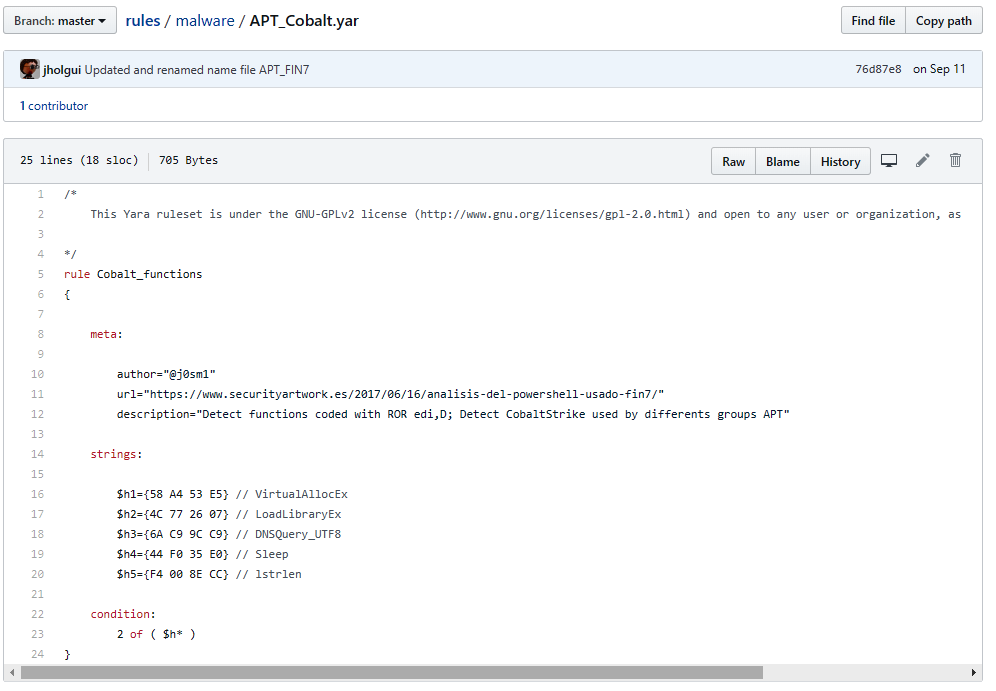
The preceding rule configures Yara to alert you to any strings found as Cobalt_functions.
Yara is available as a tool for use in malware research, but one of the useful features is the ability to integrate the Yara functionality into other tools. One such tool is Loki—a simple IOC scanner (https://github.com/Neo23x0/Loki). This lightweight platform allows incident response analysts to scan folders, files, or even entire volumes for IOCs such as Yara rules, known bad file hashes, filename IOCs, and known C2 servers. Out of the box, Loki has an extensive library of IOCs that are updated regularly:
- To check a system volume for specific IOCs, download and extract Loki to a USB device. Open the Loki folder and the following files are found:

- Loki has to be updated with the most current IOCs, so right-click on loki-upgrader and run as administrator. The upgrader will run, updating both the executable and the signature files. Once completed, the updater will close.
- Navigate back to the Loki file and a new file called signature-base will have been added:
This folder contains all of the IOCs that Loki can search for a volume against. This also allows analysts who create their own Yara rules to load them into the file as well, giving them the ability to customize the solution.
- To run a scan of a system, right-click on the loki application and run it as an administrator. This will start the executable and open the following window:

After the ruleset is updated, Loki will then begin searching the volume for any matching patterns or IOCs:
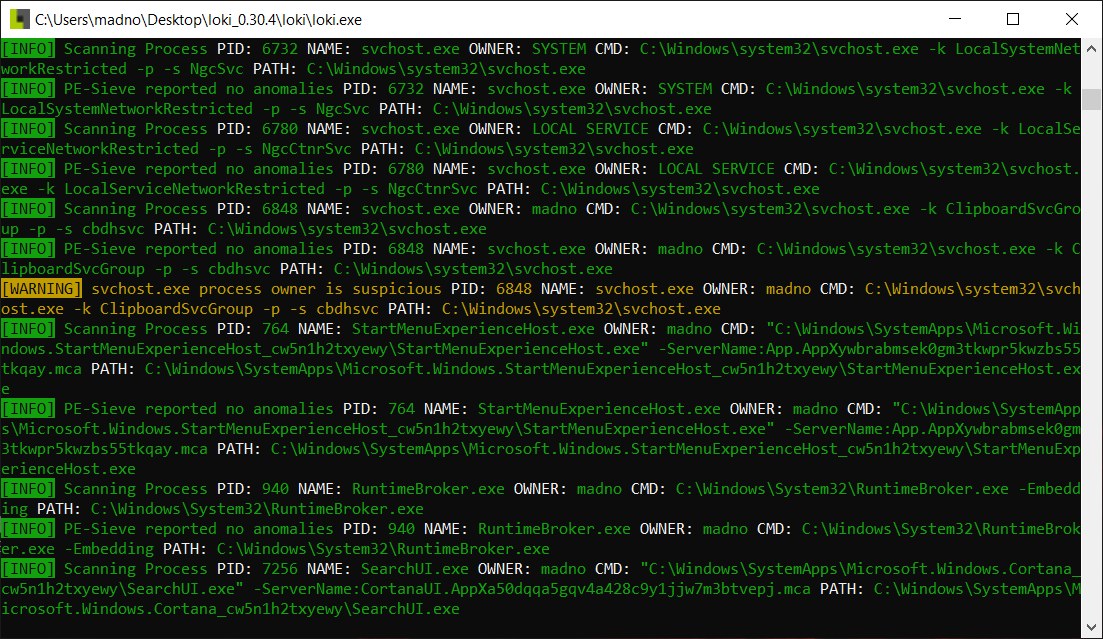
From here, the analyst can take note of any hits and conduct an examination later. Another key feature is that Loki can be deployed on multiple systems as part of a triage of systems that have possibly been infected with a new strain of malware. For example, an incident response analyst may be able to search for the IOC of the Petya ransomware attack using Yara rules taken from a threat intelligence provider, such as Kaspersky's Securelist, which includes a download of the Yara rules.
From here, the Yara rules can then be fed into Loki or another platform and utilized to triage suspected systems.
The number of tools that an incident response analyst can bring to bear is increasing every day. These include commercial tools and freeware tools that integrate a variety of threat intelligence feeds and functionality. These tools can be used proactively to detect and alert as well as investigate an incident in progress. CSIRTs should make a concerted effort to examine these tools and integrate them into their processes. Doing so will aid them in detecting and efficiently investigating an incident.
