Once the memory image is done processing, the main page provides a comprehensive list of the running processes at the time of acquisition. This includes the full path of the process, the process name, and the Process Identification (PID) number.
A review of the current processes indicates that there are three lsass.exe processes with PIDs of 1928, 868, and 680. This is suspicious as multiple lsass.exe entries are indicative of malware behavior:

Another feature of Redline is the ability of responders to examine the processes in relation to their parent processes. The hierarchical process provides a view into the path that processes were executed via. This is useful when examining memory for evidence of illegitimate or rogue processes. Click on Hierarchical Processes in the left pane under Analysis Data. This will change the view to show the processes in relation to their parent process:

An examination of the processes shows two instances of lsass.exe with the process IDs of 680, 868, and 1928. Having a single lsass.exe process is expected, but having three is suspicious because lsass.exe can be spoofed and is often abused by malware coders:
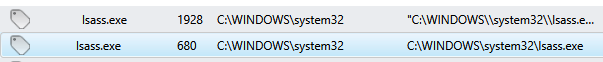
From here, the lsass.exe process with the ID 680 can be investigated further. If you double-click on the process, the following window appears:

This expanded process information shows that this process was spawned by the winlogon.exe process from the System32 folder. This may not be suspicious behavior, as this is expected. Since there should only be one lsass.exe process, the other two lsass.exe processes should be examined further. The lsass.exe with the PID of 868 appears to have been executed with the parent process of services.exe:

The same results are found with the lsass.exe with PID 1928:

At this stage, it appears that this system has multiple lsass.exe processes, which in and of itself is suspicious. The next stage in this process is to dump the address space for all three processes for further examination. To dump the address space, right-click on the process and the following window will open:

Click on Acquire this Process Address Space. From here, Redline will acquire and dump the files associated with the files into a separate zip folder in the directory containing the analysis data:
As all three lsass.exe processes are suspect, they should all be acquired. From here, the files associated with the address spaces can be examined. This will be addressed in Chapter 12, Malware Analysis for Incident Response, where the files will be examined.
This chapter was only able to scratch the surface of the feature set of Redline. In addition to being able to identify processes and extract the data associated with it, Redline also has the ability to identify other key data points, including network connections, DLL files associated with processes, and the ability to see processes in a timeline view. The next section will demonstrate how to extract some of these same data points using the open source command-line tool Volatility.
