REMnux is a freeware command line-based utility for conducting malware analysis. Developed and maintained by Lenny Zeltser, REMnux has a variety of tools that allow analysts to examine suspicious documents, JavaScript, and other artifacts associated with malware. Further, there are tools such as Wireshark that can be utilized to not only analyze the malware but to identify network connections or traffic.
Once downloaded, the file can be converted by the analyst's selected virtualization software. On the desktop are two links to .html files, and a PDF document that contains all of the necessary information for an analyst to conduct an examination. To start an examination, click on the Terminal icon, and an icon window will appear. For most commands, the convention is as follows:
remnux@remnux:~$ <Command><Malware File>
In the following example, a malware executable will be analyzed. In this case, the file will be a binary associated with the Ursnif doc. The file can be found at https://www.malware-traffic-analysis.net/2019/09/04/index.html. Again, ensure that proper precautions are taken when working with malware. One advantage of REMnux as a Linux platform is that there is little risk in downloading a Windows-based malware sample directly onto that system.
Once the file is properly situated, pescanner can be run against the file. pescanner is a tool that statically examines a PE-formatted file. To run the tool, the following command is used:
remnux@remnux:~$ pescanner 2019-09-04-initial-Ursnif-binary.exe
The command produces a good deal of information. It first provides the metadata, including a file hash, the size of the binary, and the architecture for which the binary has been coded, as shown in the following screenshot:

Another key focus point is that REMnux identified that the CRC (short for Cyclic Redundancy Check) does not match, indicating suspicious behavior. A CRC check is normally used to detect errors or changes in raw data contained within software code, through the use of a hashing function. In this case, the executable's metadata indicates that the CRC is 0x0, and in actuality is 0x54247. This anomaly is another indicator that may point toward the file being malicious.
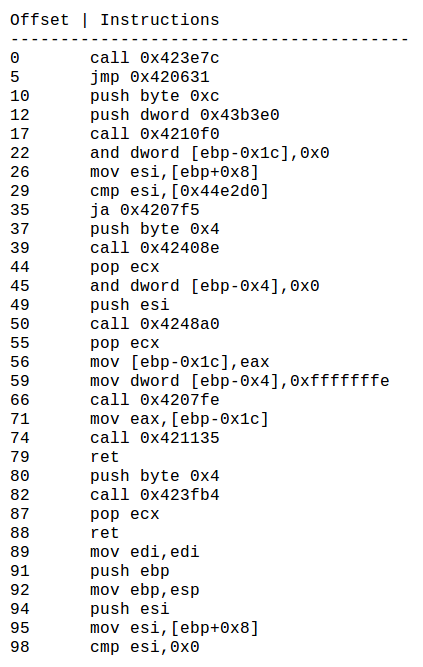
Other information includes the instructions that the malware is programmed to perform, shown in the following screenshot:
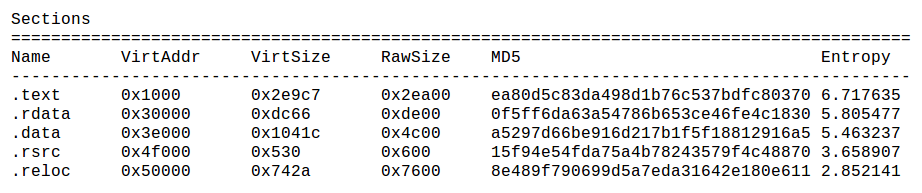
Next, pescanner has identified the sections of memory in use by the piece of malware. There is also a section that details the entropy of specific sections. Higher entropy indicates that a file is compressed or encrypted. In this case, pescanner has indicated that there is no specific memory section deemed suspicious, due to its being outside the norm for entropy, as shown in the following screenshot:
Moving down the results, pescanner indicates which dynamic-link library (DLL) files are imported as part of this malware. From here, the analyst can possibly determine more of the malicious file's behavior, by examining these files, a list of which can be seen in the following screenshot:

Finally, pescanner will indicate which suspicious Import Address Table (IAT) entries are being called by the malicious software. This allows analysts to determine what behavior the malicious code is exhibiting and, possibly, which actions it is performing on the infected system by examining these entries, as shown in the following screenshot:

Boasting a wide range of tools, REMnux is an excellent resource to conduct a wide range of tasks associated with file examination. Further, REMnux includes other tools, such as Rekall and Volatility, so that analysts can perform a panoply of tasks from memory image analysis, in conjunction with malware analysis.
