Responders can also check the loaded DLL files associated with a process. This allows the analyst to determine whether a suspect process accessed these files when it was executed. For example, if a responder would like to examine the DLL files associated with one of the suspect processes, PID 1640, the following command is run:
dfir@Desktop-SFARF6G~$ volatility -f cridex_laptop.mem -profile=WinXPSP2x86 -p 1640 dlllist
The command produces the following output:
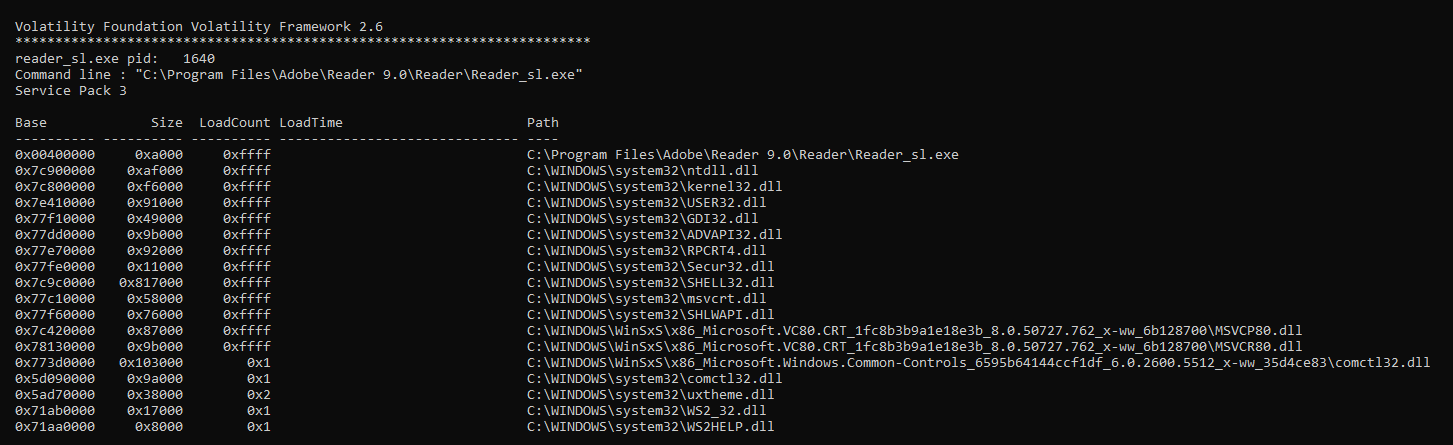
The output indicates that there are several DLL files that are loaded as part of the reader_sl.exe process. Later in this chapter, these DLL files will be acquired for further examination.
