Event Log Explorer is an event log analysis tool that has more features and has an easy-to-navigate GUI. Available as a commercial tool, the creators of Event Log Explorer, FSPro Labs, provide a 30-day trial period in which to test the tool. The tool can be downloaded from the website at https://eventlogxp.com/ and can be installed on the Windows OS.
To begin an analysis of offline event logs, proceed as follows:
- Open Event Log Explorer. The following window will appear:
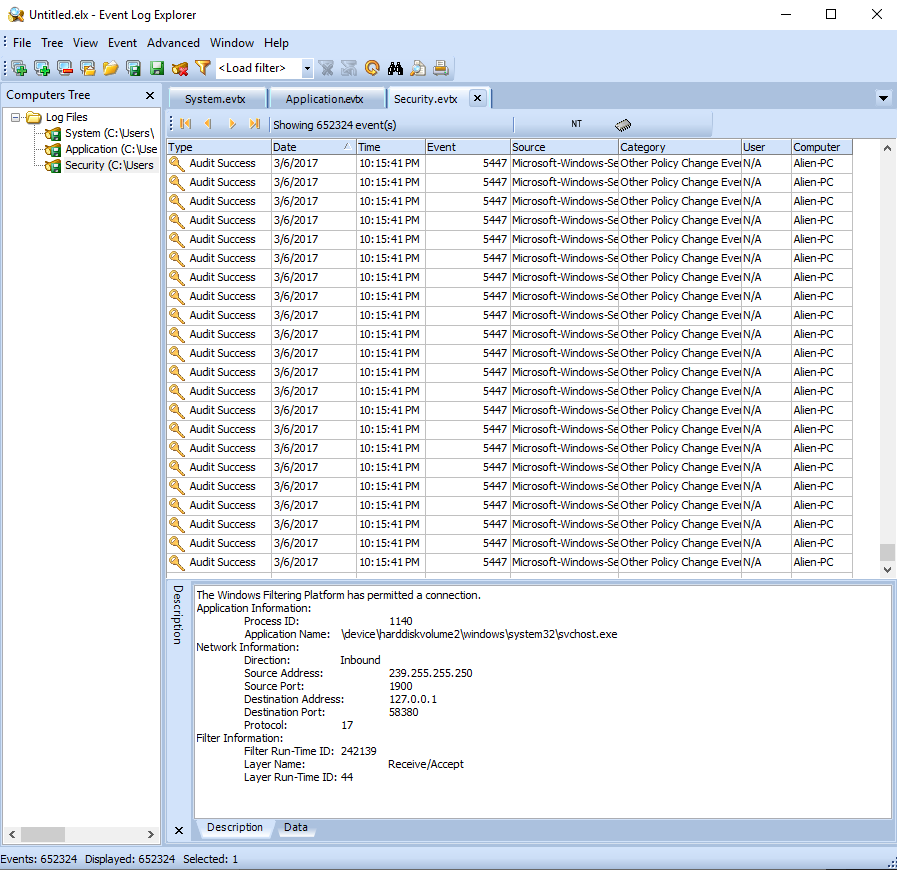
The GUI has three main areas. The center pane contains the individual log entries that are contained within the Windows event log type. The lower pane contains the details contained within each log entry. Finally, the left-hand pane includes the Windows event log types that are under analysis.
- Event Log Explorer will automatically import the localhost's Windows event logs. To remove these logs, right-click on the computer name, and click Remove Computer. Click YES. This will remove the existing Windows event logs.
- To import an event log file or files, click on File | Open Log File | Standard. From here, load the log file from a directory and click Open, as shown here:

- Once the log file or files have been loaded, the responder can utilize the filter to focus on specific data contained within the log files. To open the filter, look for the filter icon on the taskbar:
![]()
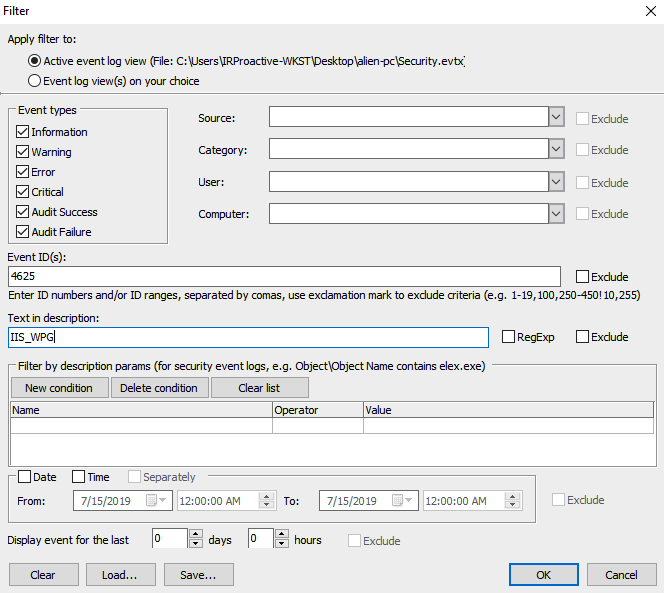
- The filter screen will then open. From here, the responder can filter the event logs on a variety of specific attributes. This includes the event types, event ID, and even keyword searching in the text of the log file entry. In this case, the responder will examine the log entries for the failed logins, event ID 4625, that include the username IIS_WPG that was identified with the DeepBlueCLI triage script. The responder enters the event ID as 4625, and in the Text in description field, the plaintext of the account name, IIS_WPG, as follows:
- The output, after clicking OK, shows the event log entries that match the filters that were entered. An examination of the details of the event log entries indicates that the workstation that was attempting to use those credentials was named Kali, with the IP address 192.168.1.106, as shown here:
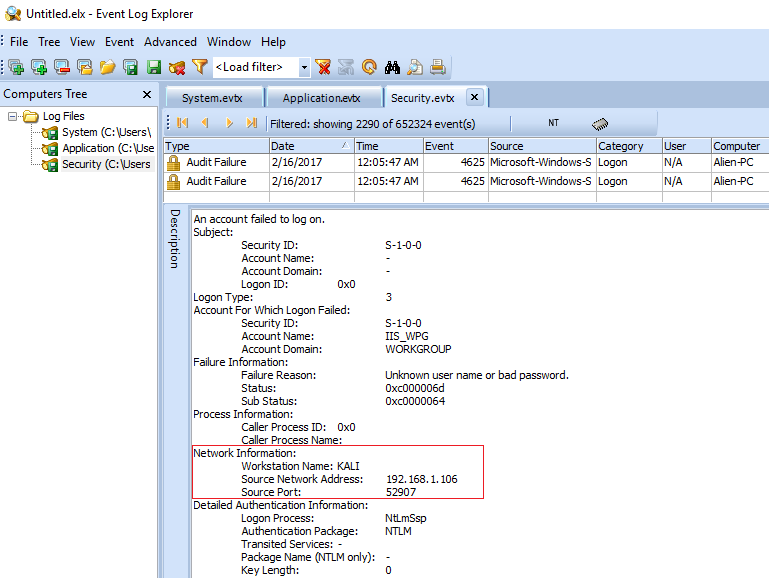
In this brief scenario, the responder was able to take data from the Windows security event logs and extract two very important data points: first, the hostname, Kali (a well-known penetration testing platform), as well as the IP address of the attacking system. They can now use this information to examine other log sources for that IP address and hostname, to discover any additional information concerning that system's activity.
Event Log Explorer has a great deal of functionality that cannot be addressed in this volume. Some of the other features include building custom views, filtering on specific data points, and finding text within log entries across multiple event log files. Even with these features, Event Log Explorer does have some minor limitations. First, responders have to gather the logs onto the system for analysis and load them manually. The second is that depending on the file size, Event Log Explorer may have performance issues, including freezing. Responders should ensure they do not overload the application. Regardless, Event Log Explorer is an excellent tool for responders to include in their toolkit.
