Much like the incident response process, the digital forensics process defines the flow of digital evidence related to an incident, from when it is first identified to when it is presented to either senior leadership or to a trier of fact, such as a civil or criminal court. There are several schemas that define this process and, for the most part, they generally follow a similar path. Here, we will be utilizing the Digital Forensics Research Workshop (DFRWS) digital investigation framework. This framework is depicted in the following diagram:
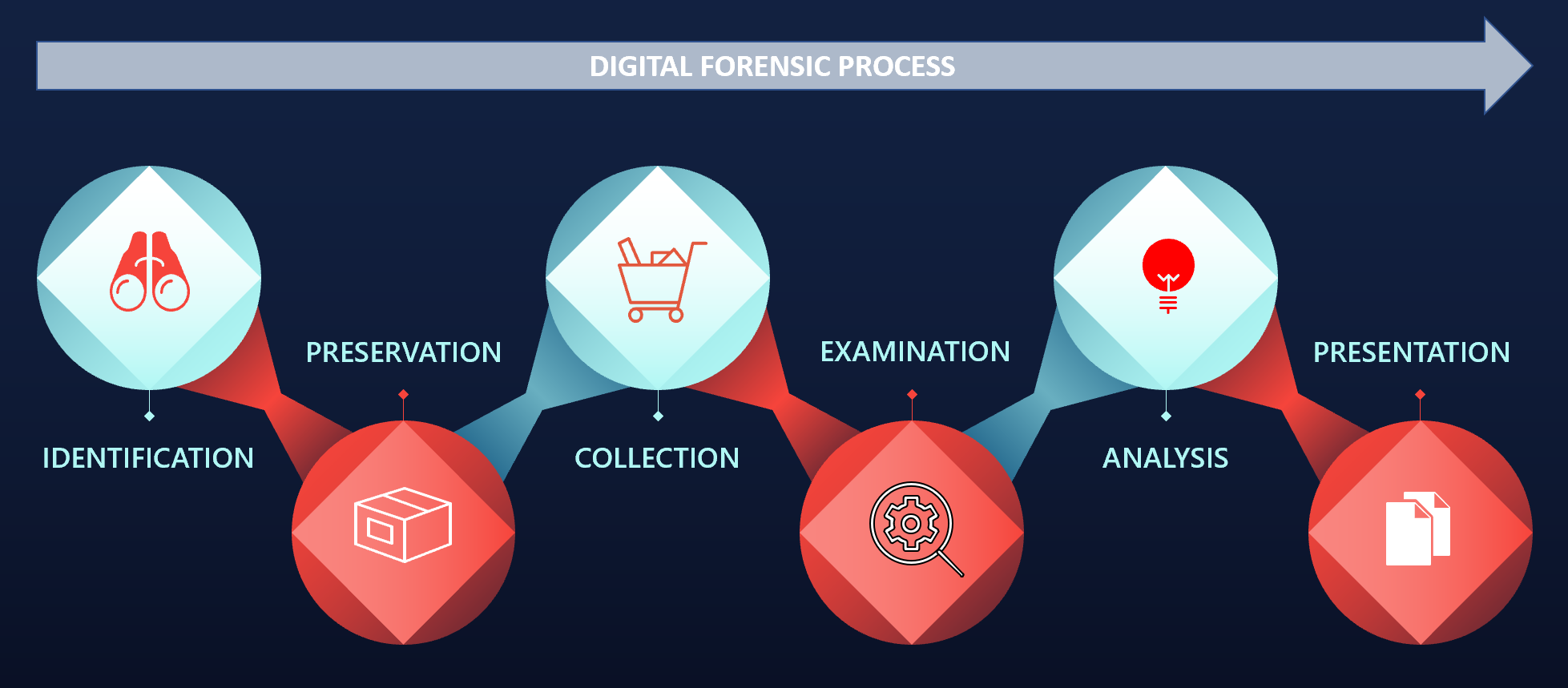
The framework contains six elements:
- Identification
- Preservation
- Collection
- Examination
- Analysis
- Presentation
From an incident response standpoint, personnel will not normally seize network components or critical systems and take them offline unless there is a compelling reason to do so. This is one of the balancing acts inherent in digital forensics and incident response. A purely digital forensics approach will take all relevant evidence, secure it, and process it. This process can take months, depending on the type of incident. This approach, while thorough and detailed, can leave an organization without critical components for some time. The CSIRT may be able to tell the leadership after a month-long analysis which chain of events led to a breach, but that would be pointless if a month's revenue has been lost. The examiners assigned to a CSIRT must be ready to balance the need for thoroughness against the need to resume or continue normal operations.
