One freeware platform that is available is the Malware Information Sharing Platform (MISP). This community project has produced a software platform that can be used by analysts to store data about malware and other exploits. From here, they can share this intelligence within their team or other personnel. MISP is a feature-rich application with such functionality as searching, a correlation engine, the ability to export and import IOCs, and community support where users can share data.
Installing MISP is dependent on the type of operating system platform in use. Complete directions are available at https://github.com/MISP/MISP/tree/2.4/INSTALL. The creators of MISP also have provided users with a complete installation on an Open Virtualization Format (OVA) virtual machine that can be downloaded for testing. The OVA file is available at https://www.circl.lu/assets/files/misp-training/MISP_v2.4.77.ova. This is a good option as it allows analysts to test the functionality of the application without having to populate the database.
For the following demonstration, the training version of MISP will be utilized. Once logged in, the following window will appear:
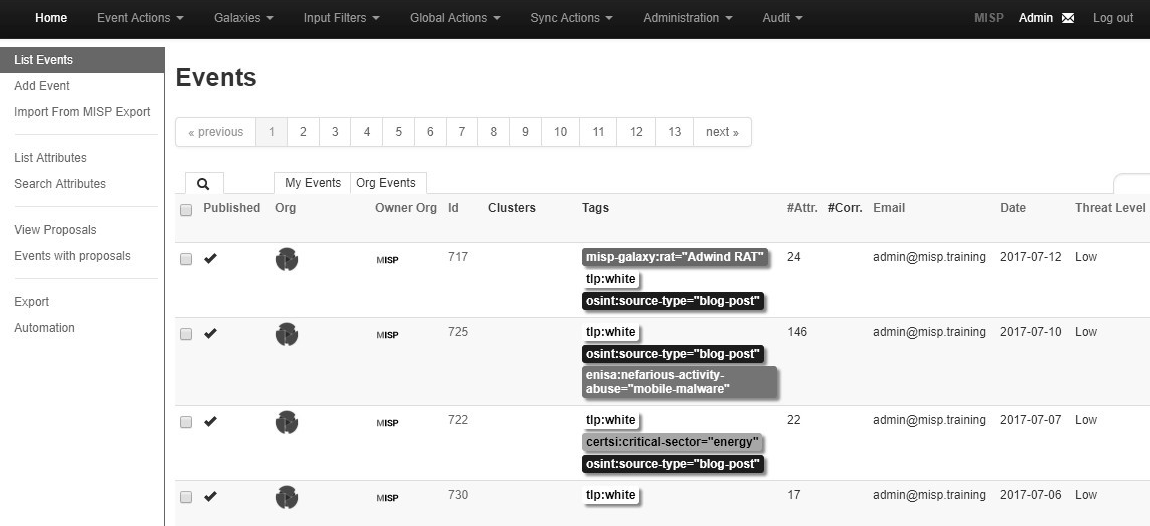
The window contains all of the events that the MISP database has on file. There is a good deal of data on this page, including tags that identify the classifications of events, the date that they were added, and basic information that allows analysts to quickly sort through the various entries.
Clicking on an Event ID or the View icon to the far right of an event brings up another window:
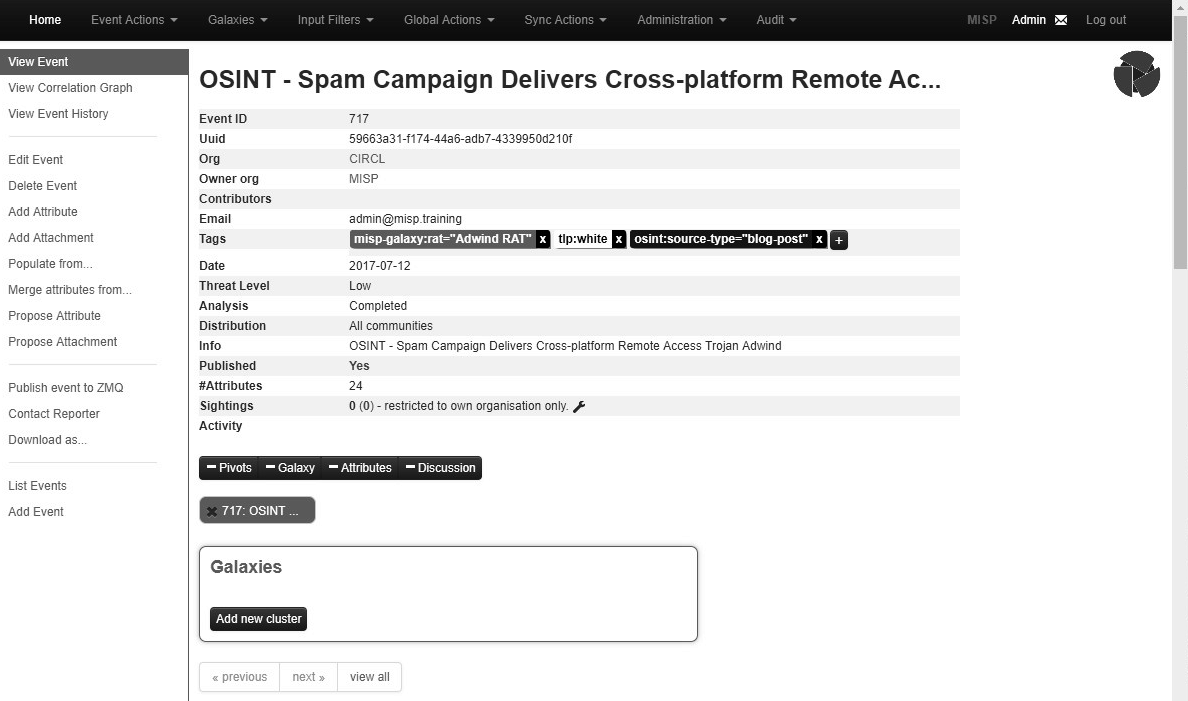
In this window, analysts will be provided with a good deal of intelligence regarding the specific event. First is the event data, which is an overview of the attributes of the IOCs contained within the event:

This data gives the analysts an overview of the event information that was available in the overall home window. Further down, the window reveals the specific elements of the event:
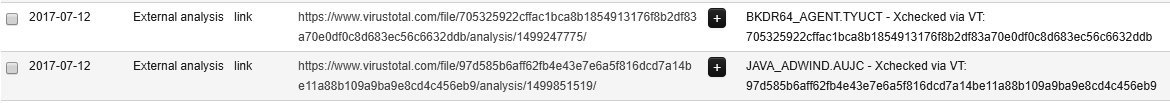
Here, the specific Trojan indicated in the background information has been evaluated by VirusTotal and following the link indicates that 46 out of 61 antivirus providers have detected that this event is linked with a Trojan virus:

The real value of the MISP platform is the IOCs that are associated with this event. Navigating down the window, the analyst can then view the individual IOCs associated with the malware addressed in this event:

From here, the analyst is able to identify specific URLs that are associated with either C2 communications or if the malware is part of a multistaged attack. The analyst can then either correlate those URLs with logs on the firewall or block those URLs through a web proxy to contain a possible malware outbreak.
Further down the window is more specific network information:
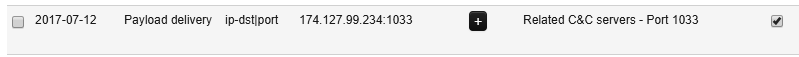
This intelligence allows analysts to drill down to a specific IP address and either block or craft an alert on the network exit point to determine whether there are any additional systems that have been compromised.
MISP also allows analysts to see specific files associated with the event:
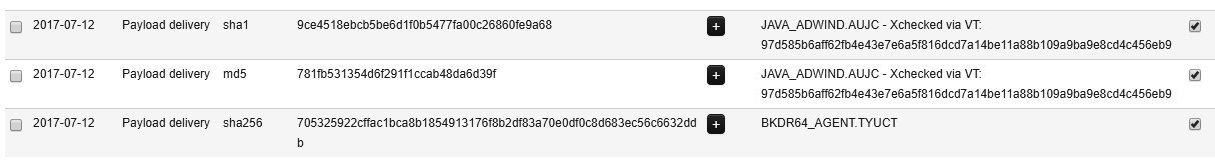
From here, analysts can utilize memory or disk images and search for matching hashes. This allows response analysts to drill down on the specific files that need to be addressed by any analysis and recovery activity.
Threat intelligence needs to be timely in order for it to be effective. In the realm of cyberattacks, intelligence goes stale very quickly. Any platform that aggregates threat intelligence should have the ability to be updated. MISP has the ability to integrate various threat intelligence feeds and add those records to the event view:
- To demonstrate, navigate to the Sync Actions tab and then click on List Feeds. The following window will open:
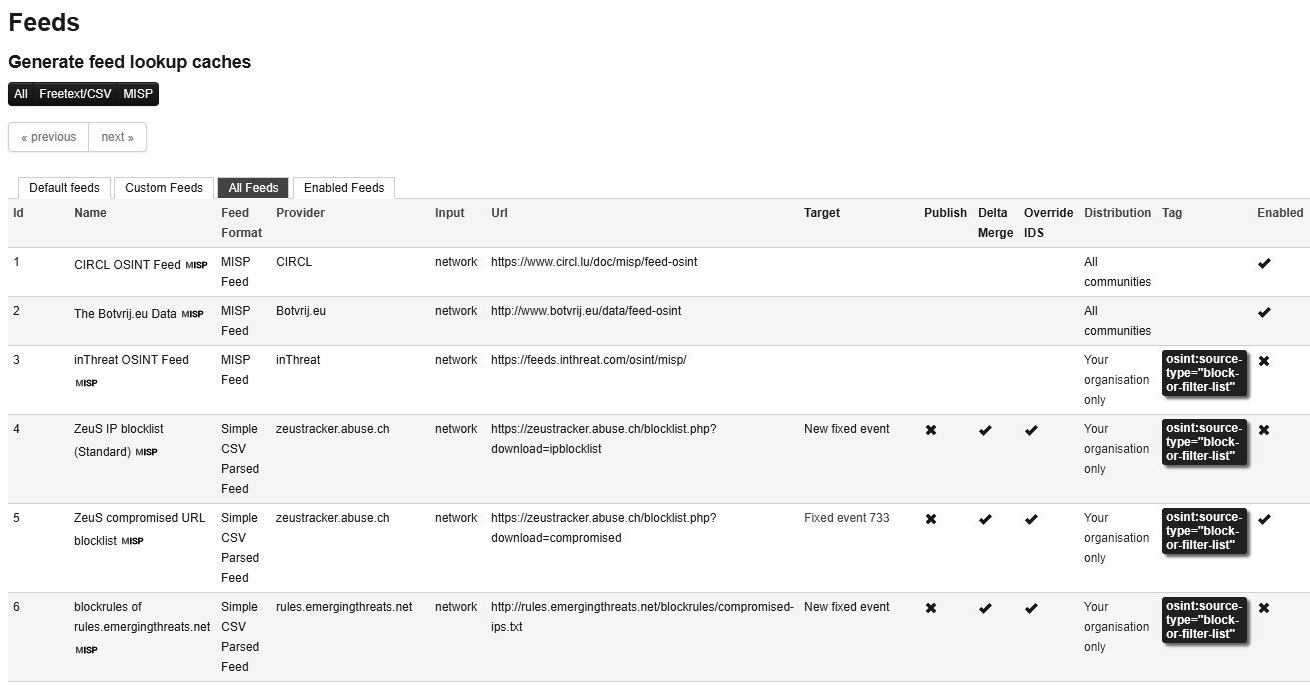
- From here, navigate to the far right-hand corner and to the down arrow surrounded by a circle. This will fetch all of the events from that source. For example, click on the button for source number five. After syncing, an additional entry is made within the events window:

Depending on the type of threat intelligence feed that the organization uses, MISP is able to enrich its dataset by utilizing a connection from those sites. This allows analysts to keep their own dataset from various providers in one searchable location. From here, they can utilize this data as part of their proactive detection capability or to assist during an incident investigation.
