Chain of custody describes the documentation of a piece of evidence through its life cycle. This life cycle begins when an individual first takes custody of the piece of evidence, to when the incident is finally disposed of and the evidence can either be returned or destroyed. Maintaining a proper chain of custody is critical. In the event that a piece of evidence has to be brought into a courtroom, any break in the chain of custody can lead to the piece of evidence being excluded from ever being admitted into the proceedings. It is critical, therefore, to ensure that the entire life cycle of the piece of evidence is recorded.
There are two primary ways that a CSIRT can record and maintain the chain of custody of a piece of evidence.
The first is electronically. There are manufacturers that provide organizations such as forensic laboratories or law enforcement agencies with hardware and software that automates the chain of custody process for evidence. These systems utilize unique barcoded stickers for each piece of evidence. A scanner then creates an electronic trail as it reads these barcodes.
The second method for creating and maintaining a chain of custody is a paper and pen method. This method makes use of paper forms that contain the necessary information to start and maintain a chain of custody. While the paper and pen method can be a bit cumbersome and requires more due diligence to ensure that the form is safeguarded from destruction or manipulation, it is a much more cost-effective solution for smaller CSIRTs that may not have the resources necessary to implement an automated solution.
In terms of what a proper chain of custody form contains, there are several sections, each with its own details that need to be provided. The following screenshot shows a template chain of custody form (an editable chain of custody form is available from NIST at https://www.nist.gov/document/sample-chain-custody-formdocx):

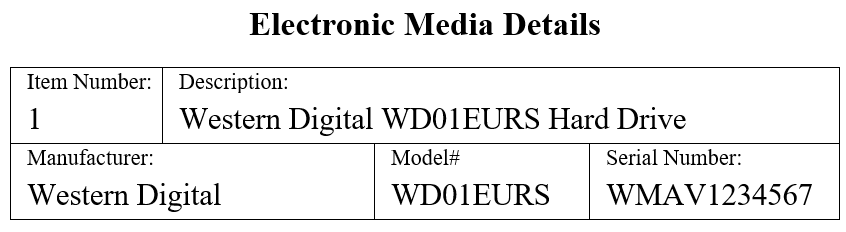
The first of these sections is a detailed description of the item. It may seem redundant to include a number of different elements, but digital forensics is about details. Having the information recorded leaves no doubt as to its authenticity. This description should contain the following elements:
- Item Number: A unique item number should be included on the form. If there are multiple pieces of evidence, a separate chain of custody form will be completed.
- Description: This should be a general description of the item. This can be a simple statement, such as 500 GB SATA HDD.
- Manufacturer: This detail assists in the case of multiple pieces of evidence with potentially different manufacturers.
- Model: As there is a wide variety of model numbers for components, recording this provides further details about the item.
- Serial Number: This is critical, in the event that an incident involves a number of systems with exactly the same configuration. Imagine attempting to reconstruct which chain of custody goes with which HDD if six were all seized together, and they had the same make and model number.
A completed first section for the chain of custody form will look like this:
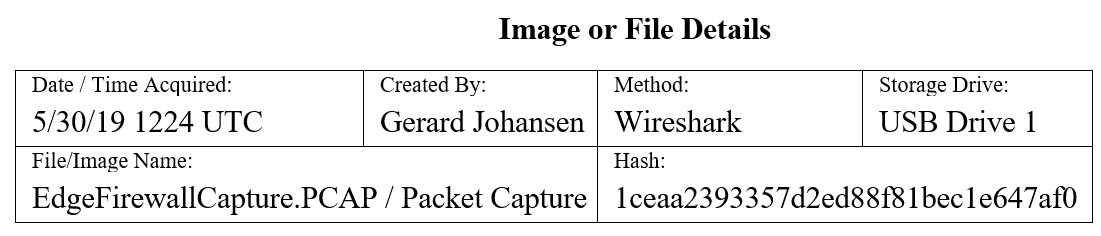
An alternate section can be used in circumstances where the evidence may be log files or images captured during the investigation. These include the following elements:
- Date/Time Acquired: It is important to be precise about the date and time at which specific files are acquired.
- Description: A brief description of the media that was acquired is useful.
- Method: If a software application or forensic tool is utilized to acquire the evidence, it should be noted. In other circumstances such as log files, it might simply be a copy to an external hard drive.
- Storage Drive: In a later section, there will be a discussion on the importance of having external media available for the storage of files. The exact drive used should be recorded on the chain of custody form.
- File/Image Name: The unique filename for the file or image is inserted here.
- Hash: For each individual file that is acquired a unique hash value should be calculated.
A completed Image or File Details section of the chain of custody form will look like this:
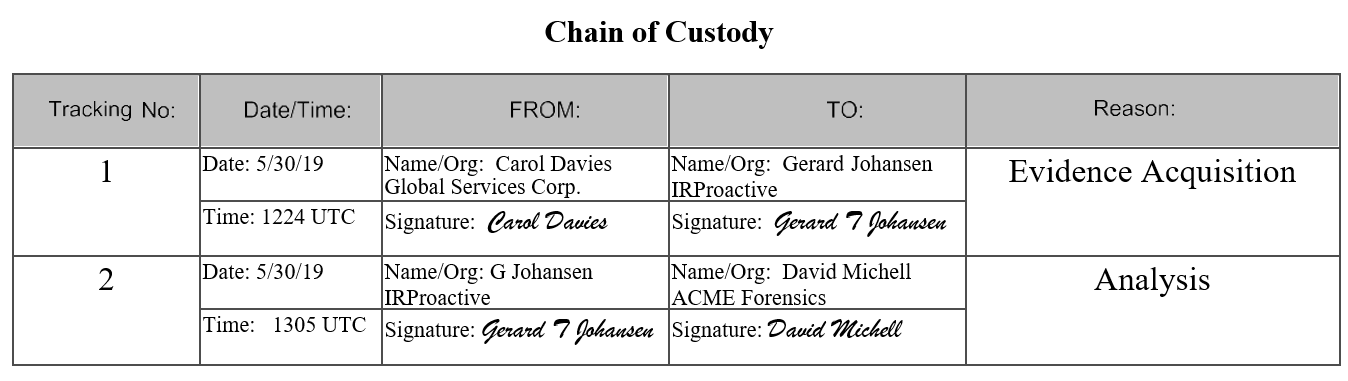
The next section details the specific steps that the piece of evidence took in its life cycle. For each stage, the following details should be captured:
- Tracking No: This number indicates the step in the life cycle that the piece of evidence took.
- Date/Time: This is a critical piece of information in any chain of custody, and applies equally to each step the evidence took. This allows anyone who views the chain of custody to be able to reconstruct, down to the minute, each step in the chain of custody life cycle.
- FROM and TO: These fields can either be a person or a storage place. For example, if an analyst has seized a hard drive and is moving it to a secure storage locker, they would note that as the to location. It is critical to have individuals named within the chain of custody sign the form (when applicable), to enforce accountability.
- Reason: Moving a piece of evidence should never be done without a reason. In this portion of the chain of custody, the reason is described.
The following screenshot is a sample of the movement of the hard drive recorded in the previous screenshot. Each move for each individual piece of evidence is recorded here. The first move is the actual seizure of the drive from the system. In this case, there is no individual custodian, as the drive has been taken from the data center. What is critical is that the author is the custodian of the drive until he is able to transfer it to David Michell of ACME Forensics for analysis. The details are as follows:
The chain of custody is maintained throughout the life of the piece of evidence. Even when the evidence is destroyed or returned, an entry is made in the chain of custody form. These forms should be maintained with any other material generated by the incident and made part of any subsequent report that is created.
