The Société Genéralé CERT has put together a platform titled FIR as a freeware tool to aid incident response teams with the creation, tracking, and reporting of incidents.
This web application can allow anyone within an organization to create incidents, make notes, and track incidents to completion. This tool provides a good deal of features that may make it a very handy tool for incident response teams that have budgetary considerations.
The tool utilizes a MySQL backend database and a combination of Python, Django, and Bootstrap to create a web application environment where analysts and other users can input data, as well as performing queries. Another key feature of the FIR application is the ability to customize fields to fit the organization. FIR can be installed either in a Docker container or installed on a Linux system, such as Ubuntu.
FIR is available for both a development and production environment. The installation of either option is based on the size of the organization and how often data will be put into the system. A complete build guide is available at https://github.com/certsocietegenerale/FIR/wiki/Setting-up-a-development-environment.
For the purposes of this book, we will give you a review of how to customize the platform and how to record an incident. There are other options that can be utilized to tailor the FIR platform for a particular CSIRT. The FIR site at https://github.com/certsocietegenerale/FIR/wiki/User-manual has additional information that is useful.
To create a new incident without any modifications, go through the following steps:
- Once FIR is installed, navigate to the login screen by entering http://localhost:8000 in the URL bar in a web browser. The sign-in form will appear. For the development environment, sign in using admin/admin:

- After logging in, the dashboard will be empty as there are no incidents to record. Click on the New event button in the upper-left corner. The following window will appear:
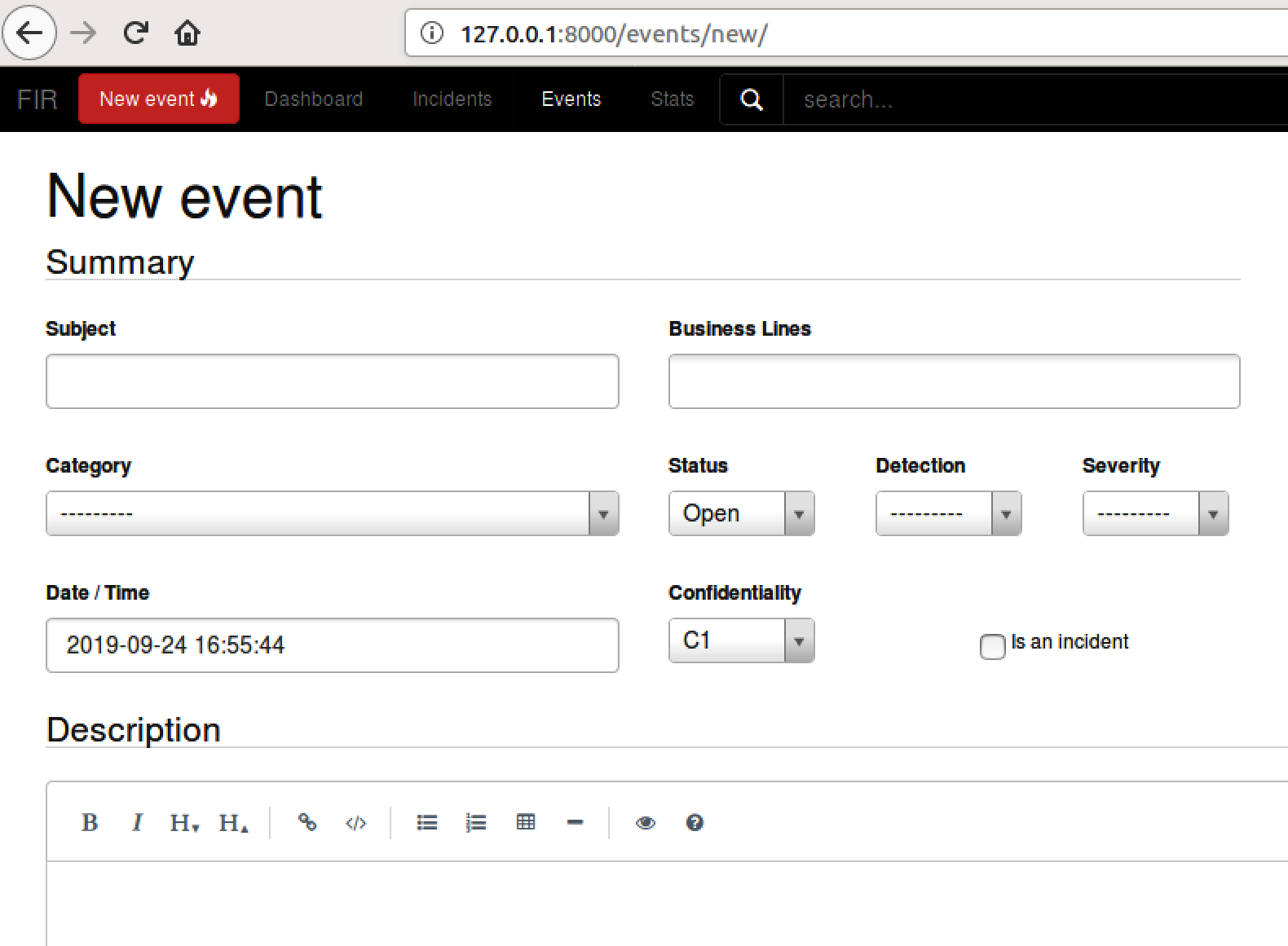
- Within the form, there are several fields that can be utilized to record an incident:
-
- Subject: This is a free text field that can take any plain text. For best practices, this would best be utilized for the individual incident number.
- Business Lines: This is one of the preconfigured fields that can be modified. Depending on the size of the organization, separating out incidents by business lines may show decision makers the security vulnerabilities within that department.
- Category: FIR has a good number of incident categories preconfigured that cover the wide range of attacks that an incident response team could see. There is also the ability to add additional categories.
- Status: This indicates whether the incident is still open.
- Detection: This shows who or what the first entity to detect the incident was.
- Severity: FIR comes preconfigured with severity levels set from 1 to 4.
- Date / Time: FIR automatically sets a date and timestamp for actions performed within the application. During configuration, you may need to modify the settings within the platform to change the time zone. The FIR installation instructions can assist with making that modification.
- Confidentiality: For organizations that have certain levels of confidentiality, this allows a gradation from 0 to 3.
- Create the incident by entering information into the specific fields. In this case, a laptop has been stolen and reported by the user to the incident response team (CERT). In this case, the reporting party has indicated that there are approximately 2,000 confidential files stored on an unencrypted hard drive:

- When the box for an incident is checked, two additional fields, Actor and Plan, appear. These are selections that can be modified to fit the organization. In this case, the actor is the CERT team and the plan will be the Device Loss Playbook. Once the fields are completed, click on Save.
- FIR then opens another window with the incident information. Click on Add and To-Do in the lower portion of the window. This will open up the following:

- In the Task field, enter in Execute Device Loss Playbook and select CERT under Accountable. Once done, click on the plus icon. This adds a task into the FIR system for a follow-up. Click on Dashboard and the incident will appear:

- Click on Tasks and the task that was assigned to the CERT team can be seen:

Through the use of the FIR platform, an incident response team can have a single repository for the incident data, as well as the ability to assign specific tasks to individuals. To further enhance this capability, FIR allows the administrator of the system the ability to make modifications to fields such as the business units or actions. To access this, click on the Admin icon in the top-right corner of the window. This will open the configuration menu:
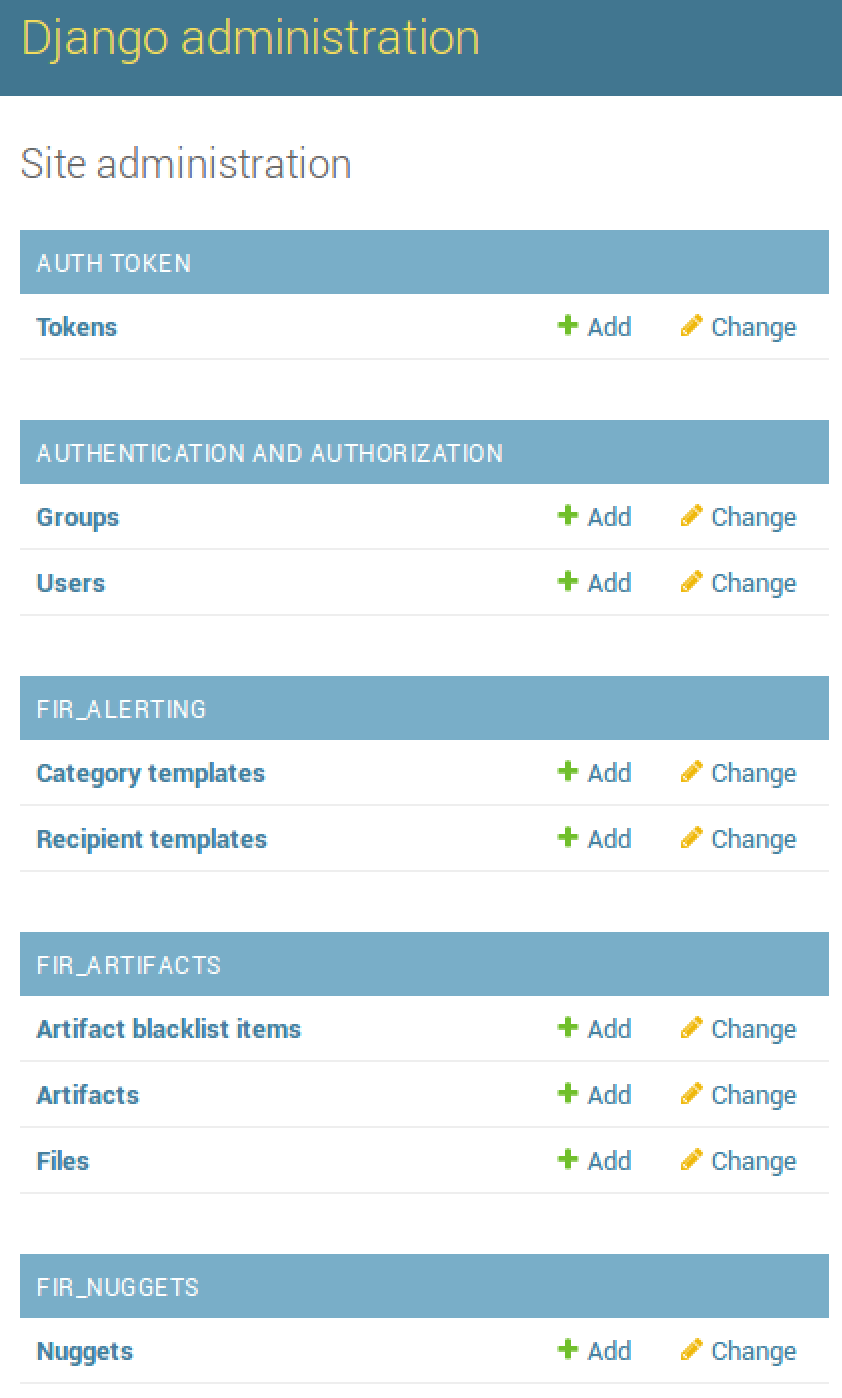
Many of these fields have not been configured yet, allowing the administrator to set specific types of alerting and artifacts. One area that the administrator may want to configure prior to utilizing is the incident information. Scrolling down, the following fields for incidents can be modified by the administrator:
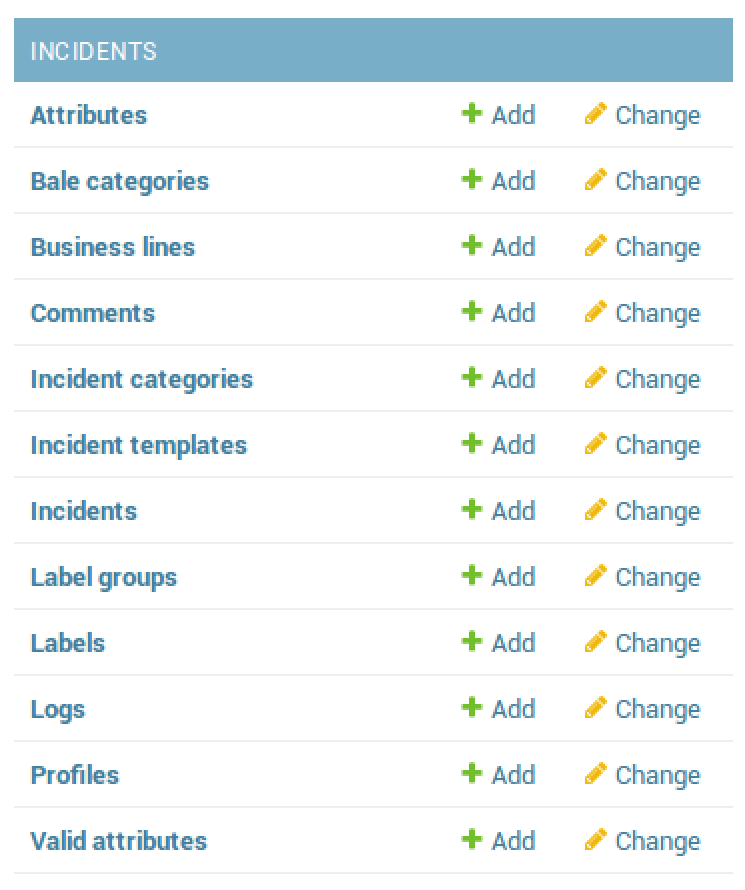
For example, suppose the administrator wants to add malware playbook to the Plan drop-down menu. This addition would immediately alert other CSIRT personnel that the playbook should be executed:
- Click on Labels and the following window will appear:
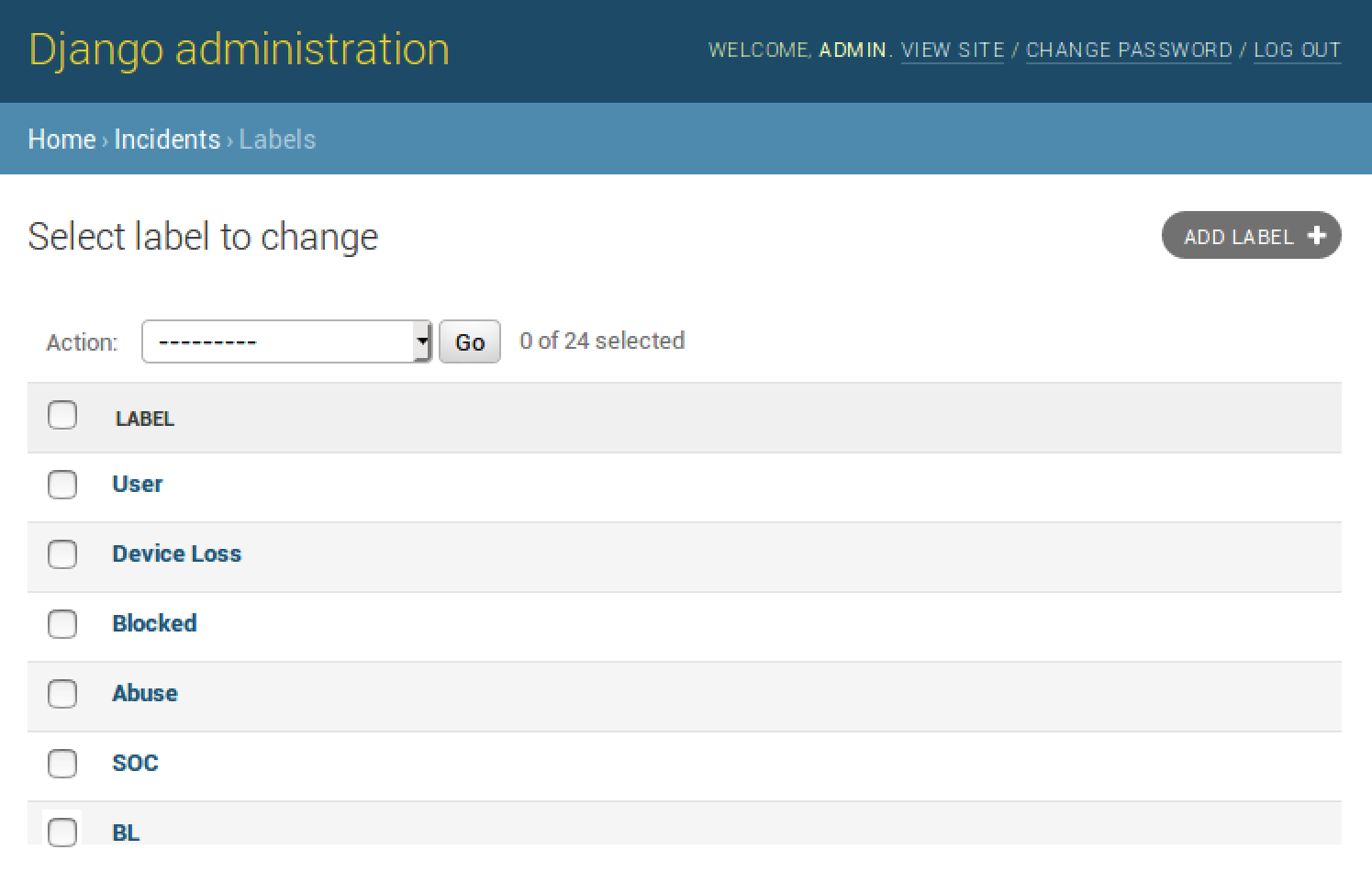
- Click on ADD LABEL. In the text field, enter Malware Playbook. For the drop-down menu, select plan. Finally, click on SAVE:

- Navigate back to the home screen and click on New Event. Click on the Major Incident checkbox. Under Plan, there should be a selection titled Malware Playbook:
This is an example of the many options that are available for modification so that the incident response analysts and team members can tailor the FIR to their own operational needs. The FIR application and other applications like it allow incident response teams to track incidents from detection to conclusion while also providing a central storage place for case information. This becomes crucial when it is time to wrap up the investigation and prepare the documentation necessary for stakeholders and key decision makers.
