The lion's share of this volume addresses the various methods that can be leveraged when investigating an incident. The primary goal of the CSIRT is to utilize methods that follow a systems analysis to address the following key facets of an incident:
- Identifying the scope: In some incidents, the actual scope may not be clearly defined at the initial detection stage. For example, an organization may be contacted by a law enforcement agency that has indicated a C2 server has been taken down. During an analysis of that system, the external IP address of the organization has been identified. From this data point, the scope is first defined as the entire network. From here, the CSIRT would analyze data from the firewall or web proxy, to identify the internal systems that were found to be communicating with the C2 server. From this data, they would narrow down the initial scope of the incident to those systems that had been impacted.
When attempting to identify the scope of the incident, there is a drive to find the patient zero or the first system that was compromised. In some incidents, this may be easy to discover. A phishing email containing a PDF document that, when opened, executes malware can be easily identified by the user or by security control. Other attacks may not be so obvious. While finding patient zero does provide a good deal of data for root-cause analysis, it is more important to identify the scope of the incident first, rather than looking for a single system.
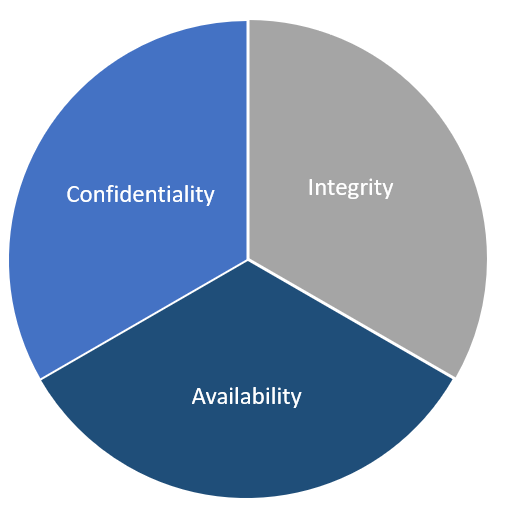
- Identifying the impact: Another key consideration is determining the impact of the incident. Those that have been exposed to the fundamental concepts of information security are well familiar with the CIA triad. The CIA triad represents the elements of security within an information system: confidentiality, integrity, and availability. Any breach or violation of security will have an impact on one or more of these elements. For example, a ransomware incident that impacts 15 production servers impacts the availability of the data on those systems. Impacts against availability related to the incident, either as a direct result or through adversary actions or the time necessary to respond and remediate, are important factors in determining the incident's impact. Other incidents, such as the theft of intellectual property, impact the confidentiality of data. Finally, incidents involving unauthorized manipulation of source code or other data impact the integrity of that data. The following diagram highlights the CIA triad:
Understanding the potential impact an incident may have is important in making decisions concerning the resources that are allocated for a response. A distributed denial-of-service (DDoS) attack against a non-critical service on the web will not necessitate the same type of response resulting from credit card-harvesting malware within a retail payment infrastructure. The impact also has a direct bearing on compliance with laws and other regulations. Understanding the potential impact of an incident on compliance is critical in ensuring that a proper response is conducted.
- Identifying the root cause: The central question that IT professionals and managers will ask during, and especially after, an incident is: How did this happen? Organizations spend a great deal of money and resources to protect their infrastructure. If an incident has occurred that causes an impact, there will be a need to understand how it happened. A goal of an incident investigation is to determine what sequence of events, vulnerabilities, or other conditions was present that led to the incident and the impact. Often, the root cause of an incident is not a simple vulnerability, but a sequence of events and conditions that allowed an adversary to penetrate the security systems and conduct their attack. Through an investigation, these events and conditions can be identified so that they are corrected, or otherwise controlled.
- Incident attribution: One area of debate involved in an incident investigation is incident attribution. With attribution, the CSIRT or investigative body attempts to determine which organization was behind the attack. Incidents may be attributed to nation-state actors, criminal groups, or other cyber adversaries. While there is some importance to attribution from a threat intelligence perspective (Chapter 13, Leveraging Threat Intelligence, will address attribution, as it relates to incident response), resources are better off investigating or containing an incident. Attempting to ascertain the group or groups responsible for an attack is time-consuming, with few positive returns. If the organization's leadership is adamant about determining attribution, the best approach is to comprehensively document the incident and pass off the data to a third party that specifically addresses attribution. Such organizations often combine data from several incident investigations, to build a dossier on groups. If the data supplied matches these, they may be able to provide some context in terms of attribution.
