Having a solid understanding of the facets of forensic imaging is important for incident response analysts. Having an understanding of the tools, techniques, and procedures involved ensures that evidence is handled properly and that analysts have confidence in the evidence they've acquired. In addition, understanding the necessary terminology allows analysts to accurately prepare reports and testify as to their findings if the need arises.
One of the first concepts that should be understood is the difference between forensic imaging and copying. Copying files from a suspect hard drive or other medium only provides analysts with the actual data associated with that file. Imaging, on the other hand, allows the analyst to capture the entire drive. This includes areas such as slack space, unallocated space, and possibly access deleted files. Imaging also maintains metadata on the volume, including file timestamps. This becomes critical in the event that a timeline analysis is conducted to determine when specific files were accessed or deleted.
Often, the terms cloning and imaging are utilized in place of each other. This is a common improper use of terminology in the Information Technology realm. When cloning a drive, a one-to-one copy of the drive is made. This means that the drive can then be inserted into a system and booted. Cloning a drive is often done to make a fully functional backup of a critical drive. While a cloned drive contains all the necessary files, it is cumbersome to work with, especially with forensic tools. As a result, an image file is taken. An image of a drive contains all the necessary files; its configuration permits a detailed examination while utilizing forensic tools.
The second concept that needs to be understood is the types of volume that can be imaged. Volumes can be separated into physical or logical volumes. Physical volumes can be thought of as containing the entirety of a hard drive. This includes any partitions, as well as the master boot record. When imaging a physical volume, the analyst captures all of this data. In contrast, a logical volume is a part of the overall hard drive. For example, in a hard drive that is divided into the master boot record and two partitions, a logical volume would be the D drive. When imaging a logical volume, the analyst would only capture data contained within the D drive.
The following diagram illustrates data that is captured while imaging either a physical or logical volume:
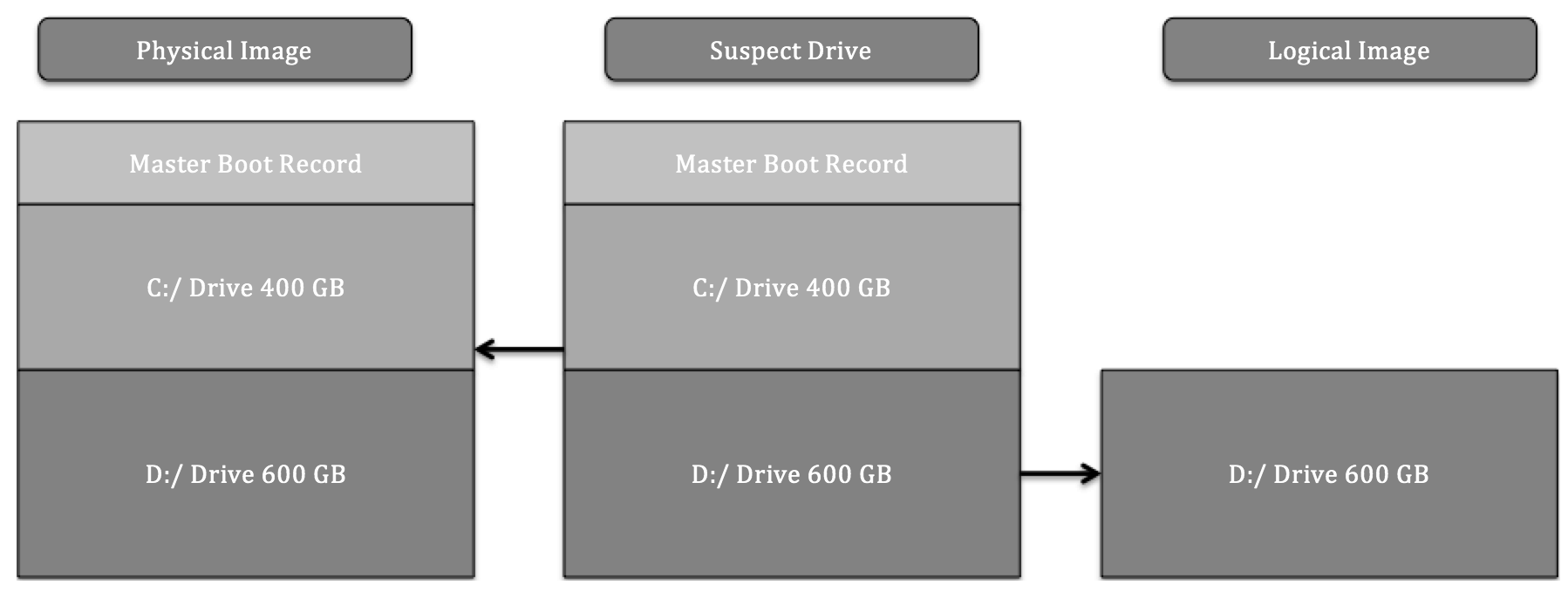
The type of incident that is being investigated largely dictates the type of imaging that is conducted. For example, if an analyst is able to identify a potentially malicious file being executed from the D drive and is intent on only capturing that data, it might be faster to acquire a logical image of only that volume. Furthermore, logical acquisition may be necessary in cases where Full Disk Encryption (FDE) is being used. Without the encryption key, logically acquiring files while the system is running is often the only option that's available.
The one key drawback that a logical image has is that it will not capture unallocated data or data that is not part of the filesystem. Deleted files and other trace evidence will not be part of a logical image. In cases where activities such as employee misconduct are suspected, the analyst will need to trace as much activity as possible, so a full image of the physical volume will be conducted. Time isn't a necessary factor here.
In Chapter 4, Collecting Network Evidence, we discussed the acquisition of evidence such as log files and running memory from a live or powered up system. In much the same way, incident response analysts have the capability to obtain a logical volume from a running system. This technique is referred to as live imaging. Live imaging may be the best option if a potentially compromised system cannot be taken offline, say, in a high-availability production server, and potential evidence is located within a logical volume.
Dead imaging is performed on a system that has been powered down and the hard drive removed. In this type of imaging, the analyst is able to capture the entire disk, including all the volumes and the master book record. This may become necessary in incidents where analysts want to ensure that they capture the entirety of the source evidence so that there is no location that hasn't been examined.
One final aspect of forensic imaging that an analyst should have knowledge of is the types of image files that can be created and leveraged during an investigation. There are several types of image file, some of which are very specialized, but for the purposes of this book, we will focus on the two most common types of evidence file that analysts will most likely create and work with during an incident:
- Raw images: A raw image file contains only the data from the imaged volume. No additional data is provided in this type of image, although some imaging tools such as FTK Imager include a separate file with imaging information. Raw image outputs include the .raw, .img, and .dd extensions. Some software, such as the Linux dd command, provides a flexible option when speed and compatibility with forensic tools may be an issue.
- EnCase evidence files: The EnCase evidence file, or E01 or EX01 file, is a proprietary file format that was developed by OpenText as part of their EnCase forensic tools in 1998. This format was based on the Expert Witness Format (EWF), which was found in the ASR Data's Expert Witness Compression Format. The E01 file contains metadata about the image. The metadata that is contained in both the header and footer captures and stores information about the drive type, operating system, and timestamps. Another key feature of the E01 file is the inclusion of a Cyclical Redundancy Check (CRC). This CRC is a file integrity verification that takes place after every 64 KB of data is written to the image file. This CRC ensures the integrity of the preceding block of data over the entire image file. Finally, the E01 file contains the MD5 hash within the footer of the file. The following diagram illustrates which components of the E01 file are created during the imaging process:

An E01 file is the preferred output for law enforcement and legal entities as it combines the ability to verify evidence integrity with software features such as compression. The E01 file also works with a variety of forensic software.
The information that has been presented here is really just an overview of some of the core concepts of imaging. As a result, there are a great many details concerning forensic imaging that couldn't be included in this book. Having a detailed understanding of forensic imaging will allow an incident response analyst to prepare an accurate report, while also being able to describe how their actions produced the output that served as the foundation of their analysis.
While this book focuses on the RAW and EnCase evidence file formats, there are two other common file formats that responders may encounter, especially if they are working with other organizations:
- Advanced Forensic File Format (AFF4): The AFF4 image file format is an open source project that was developed for the storage of digital evidence and other data. This format is used primarily with the Pmem volatile memory acquisition toolset.
- Access Data Evidence File (AD1): Here, the owner of the Forensic Tool Kit (FTK) suite of tools uses AD1 as their proprietary evidence file.
With the overall concept of forensic imaging addressed, the next step is to look at the tools available to capture a forensically sound image.
