When investigating an incident, it is critical to have an idea of when applications or files were executed. Timestamps can sometimes be found in other aspects of the investigation, such as when examining memory images. Also, identifying specific DLL files or executable files in the memory image can be compared to the date and time they were accessed in order to correlate other activity that's been observed on the system.
Autopsy has functionality specifically for timeline analysis. Simply clicking on the Timeline button at the top of the window will make Autopsy begin the process of parsing out timeline data. Depending on the size of the image file being analyzed, it may take a few minutes. Once completed, the following window will open:
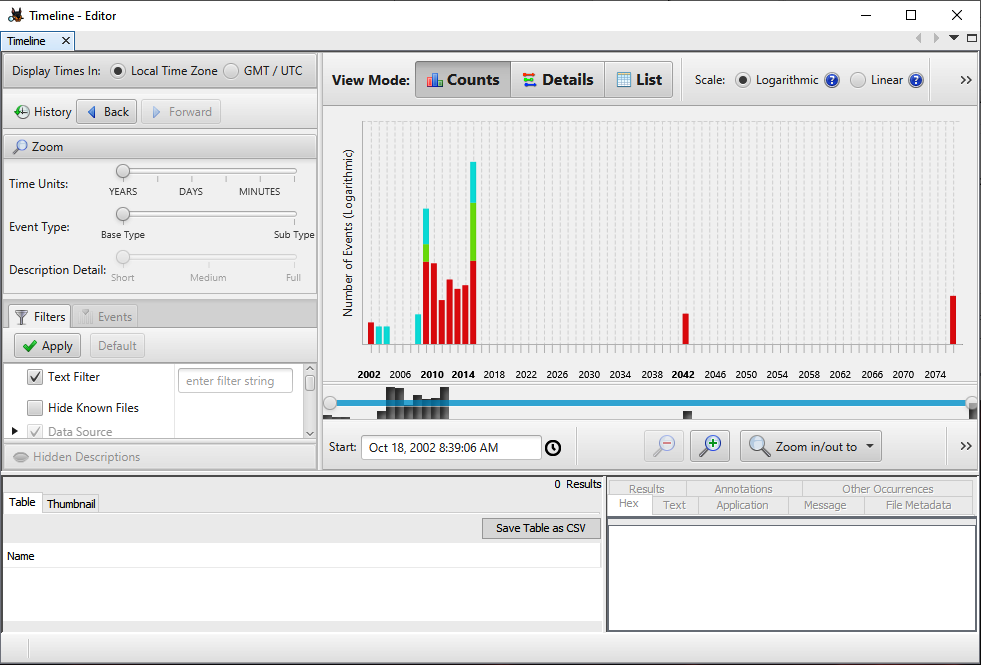
From here, the analyst can utilize several features. First is the text filter on the left-hand side of the screen. From here, the analyst can search for specific text in files. For example, the analyst has already identified that the spreadsheet named pricing decision had been accessed by the system under investigation. If the analyst would like to know whether that file was accessed at any other times, they could enter pricing into the Text Filter box and click Apply, which would produce the following results:
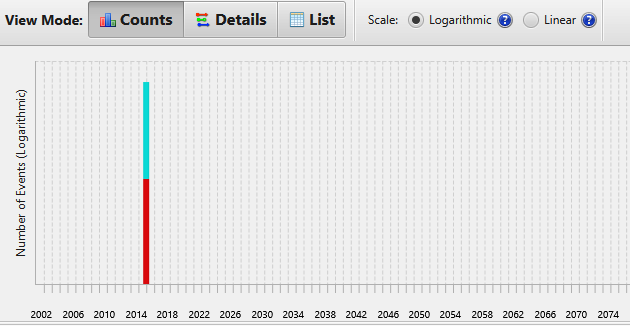
From this graph, the analyst can further drill down into the specific times the file was accessed by clicking on the colored bars.
The responders can now see that the file was only accessed on one particular date and time from this system.
