Another tool that responders should be familiar with when it comes to malware analysis is the pattern-matching tool YARA. YARA (short for Yet Another Ridiculous Acronym) is a schema to identify and classify malware, through the creation of text-based rules. YARA rules are a combination of strings and Boolean expressions that are married with a condition, to determine if a specific file has any of the attributes contained within the YARA rule. For example, the following is a YARA rule created by Florian Roth for the Stuxnet malware and is available at https://github.com/Yara-Rules/rules/blob/master/malware/APT_Stuxnet.yar. This rule has been written to examine a suspect file for full-word strings that are associated with the Stuxnet malware, and the code for this can be seen here:
rule Stuxnet_Malware_3
{
meta:
description = "Stuxnet Sample - file ~WTR4141.tmp"
author = "Florian Roth"
reference = "Internal Research"
date = "2016-07-09"
hash1 = "6bcf88251c876ef00b2f32cf97456a3e306c2a263d487b0a50216c6e3cc07c6a"
hash2 = "70f8789b03e38d07584f57581363afa848dd5c3a197f2483c6dfa4f3e7f78b9b"
strings:
$x1 = "SHELL32.DLL.ASLR." fullword wide
$s1 = "~WTR4141.tmp" fullword wide
$s2 = "~WTR4132.tmp" fullword wide
$s3 = "totalcmd.exe" fullword wide
$s4 = "wincmd.exe" fullword wide
$s5 = "http://www.realtek.com0" fullword ascii
$s6 = "{%08x-%08x-%08x-%08x}" fullword wide
condition:
( uint16(0) == 0x5a4d and filesize < 150KB and ( $x1 or 3 of ($s*) ) ) or ( 5 of them )
}
The previous rule has been written to trigger if the file size is less than 150 KB, and if either the full-word string SHELL32.DLL.ASLR or three of the $S strings are found within the file. YARA rules can be written in a standard text editor as a single rule, or multiple rules within the same YARA file.
YARA rules can be utilized in several different ways. First, they can be written based upon the static analysis of malware or exploits and used to scan memory images through Volatility's yarascan plugin. This allows responders to determine if there are traces of a particular malware in a memory image. Second, multiple rules can be run against files and disk images, to detect the presence of malware or exploits. There are also scanners such as Loki, available at https://github.com/Neo23x0/Loki, that use multiple YARA rules to scan live disks for indicators of compromise (IoCs).
Writing YARA rules can sometimes present an issue during an incident. This is due to the fact that other techniques of malware analysis, such as PeStudio or pescanner, are needed to extract strings and other indicators. Another option with regard to YARA rules is the tool yarGen, by Florian Roth. This Python script, available at https://github.com/Neo23x0/yarGen, allows responders to create YARA rules for specific files that have been identified during the course of an incident.
For this example, a file associated with the 2019-09-04-malware-from-Ursnif-and-Trickbot-infection file set previously examined contained a Microsoft Word document. Indicators extracted from that file may be useful in analyzing other systems. yarGen can be utilized to create a rule from that file. Proceed as follows:
- Download yarGen from GitHub at https://github.com/Neo23x0/yarGen.
- Uncompress the ZIP file.
- Navigate to the directory containing the yargen.py script. It is a good practice to put samples in a single directory, as yarGen works against files contained within a directory.
- Use the following command syntax to create the YARA rule. In this case, the -m directs yarGen to scan the directory Malware for the files for which the rule will be created. The -o is the output file, generally a text file with the extension .yar:
remnux@remnux:~/Desktop/yarGen-master$python yarGen.py -m Malware -o sample.yar
The script will run, and then produce a YARA rule such as this:
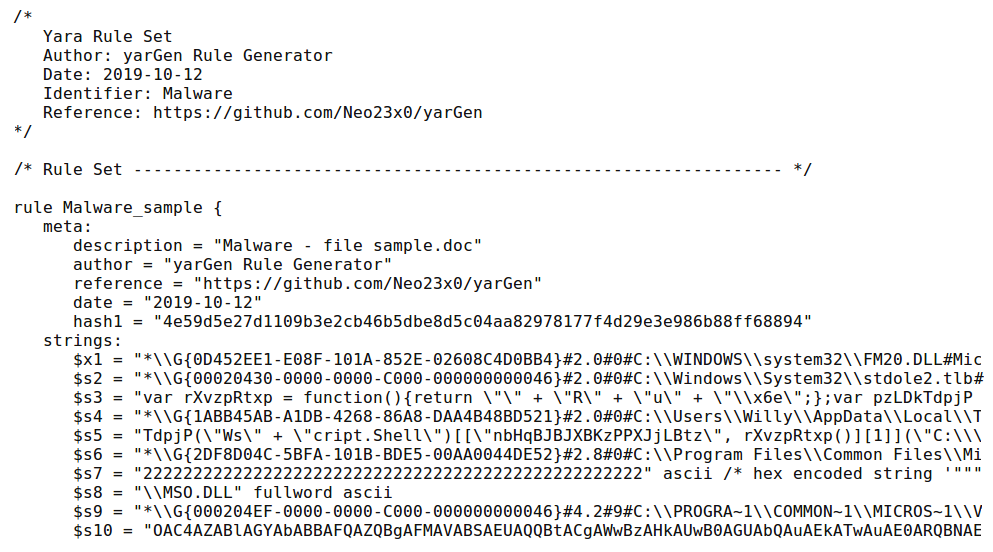
yarGen has taken the various strings associated with this particular file and created the rule. yarGen is a good option for responders, in the event that they are dealing with a number of systems or files, and they do not have the necessary time to conduct a full static analysis to extract strings.
This has been a very limited exploration of YARA and its capabilities. YARA rules are a powerful tool that can be leveraged during an incident. As rules can be crafted not only for malware but for any file, responders have the ability to scan other systems for IoCs related to exploits or scripts that an adversary has utilized, as part of their attack, that may have bypassed anti-virus or other detective controls.
