As discussed previously, depending on the incident, responders may be examining multiple Windows systems. Each of these systems may contain several thousand, or even a hundred thousand, event log entries. There is no possible way for a responder or team of responders to be able to examine that many individual entries. This equates to the often-used saying it's like finding a needle in a haystack. To address the large datasets that are often encountered in Windows event log analysis, responders can utilize the DeepBlueCLI tool. This PowerShell script, developed by Eric Conrad, detects suspicious Windows event log entries, such as service creation, account creation, a high number of logon failures, and malicious PowerShell usage. By focusing on these more critical event types, responders will be able to analyze more log files and potentially identify suspicious activity.
To run DeepBlueCLI, proceed as follows:
- Download the PowerShell script from the GitHub site: https://github.com/sans-blue-team/DeepBlueCLI.
- Open PowerShell, and navigate to the directory containing DeepBlue.ps1.
- Execute the DeepBlue.ps1 PowerShell script by pointing it to a specific Windows event log file—in this case, the Windows security event log, as shown here:
![]()
- Enable the script, if necessary, by entering R, as shown here:

After the script has run, it will produce a text output in the PowerShell window. In this case, the DeepBlueCLI script was run against Windows security event logs from a potentially compromised system. A review of the output indicated some potential signs that the system was attacked by an adversary, as can be seen in the following screenshot:
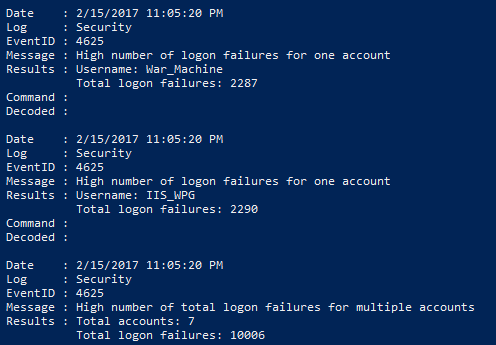
From the preceding screenshot, there are three indicators of potential brute-forcing of credentials. The first is that the username War_Machine had attempted a total of 2287 logons that were failures. Second, the username IIS_WPG executed a total of 2290 logon failures. Finally, the output indicated there were a total of seven accounts that had a high number of failures. This data allows responders to focus their attention on the event ID 4625 and those accounts, for potential evidence of a compromise.
DeepBlueCLI also provides data associated with account creations. As previously discussed, the event ID 4720 indicates that an account has been created on the system. For example, if the responder has indications that the system under examination has been infected with Carbanak, they may be able to see if any new accounts have been created on the system. The following is a sample output:

From the output, there are three new accounts that have been created. Each follows a very similar naming convention. From here, the responder can check with the access management team or system administrator to see if these names are legitimate. In the event that there is an indication that one or more of these names are not legitimate, the responder now has a data point from which to pivot and conduct other searches.
The one major drawback with Windows event log triage tools such as DeepBlueCLI is that they often focus on finding the low-hanging fruit, or those event logs that are often clearly indicative of abuse. They do make it easier for responders to triage a larger dataset, but responders should be aware that they are not foolproof, and there is a chance that an event log entry or entries may be missed.
Once a responder has been able to narrow down the entries that are important, there are several tools and techniques that can be leveraged to analyze the important log files.
